Table of Contents
Abuse Mailbox Explained
An Abuse Mailbox refers to a designated destination where users can report suspicious emails to IT and security teams for further investigation and analysis. It serves as a crucial component in tracking and preventing potential email threats within an organization. The Abuse Mailbox acts as a centralized triage dashboard that enables security teams to assess user-reported emails, remediate attacks, and address any false alarms. It plays a vital role in email security by facilitating the identification and mitigation of malicious emails such as business email compromise (BEC) and credential harvesting attacks.
How does an Abuse Mailbox Work?
The workflow of an Abuse Mailbox typically follows the following process:
-
Security Awareness Training: Employees receive training on how to identify and report potentially malicious emails to the Abuse Mailbox. This training familiarizes them with the necessary steps to take when encountering suspicious emails.
-
Reporting Suspicious Emails: When an employee receives an email that appears suspicious, they report it to the Abuse Mailbox. This can be done by forwarding the email to a specific email address designated for abuse reports, such as abusemailbox@example.com. Some organizations may also provide an integrated "Report Phishing" button in an email banner for easy reporting.
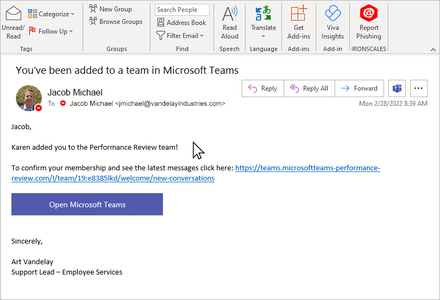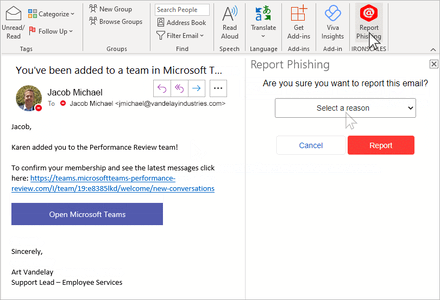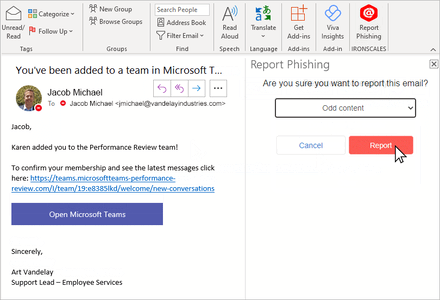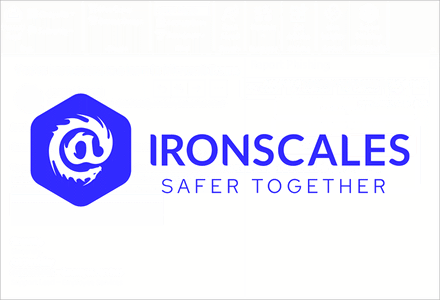
IRONSCALES Integrated Report Phishing Button
-
Manual Investigation: A Security Operations Center (SOC) analyst manually investigates the reported email to determine its nature, whether it is malicious or safe. This investigation involves scrutinizing the email's content, attachments, and other relevant information.
-
Malicious Email Identification and Removal: In the event that the email is found to be malicious, the SOC analyst proceeds to identify the entire email campaign associated with the threat. Once identified, appropriate actions are taken to remove the malicious email campaign from the organization's email system.
Depending on the outcome of the investigation, the SOC analyst may inform the reporting employee about the safety of the email or utilize external tools to identify patterns or larger-scale email attacks targeting specific departments or employees. However, due to resource constraints, some SOC teams may not have the capacity to respond to each individual report.
Why are Abuse Mailboxes Important?
Abuse Mailboxes play a crucial role in maintaining email security within organizations. The following are the key reasons why Abuse Mailboxes are important:
-
Centralized Triage: An Abuse Mailbox provides a centralized repository for user-reported emails, allowing security teams to efficiently assess and manage potential email threats. It streamlines the process of tracking, analyzing, and responding to reported emails.
-
Attack Remediation: By promptly investigating and remediating malicious email campaigns, Abuse Mailboxes help prevent further compromise of an organization's security. They enable security teams to take appropriate actions to neutralize threats and protect employees from falling victim to email attacks.
-
Pattern Identification: Abuse Mailboxes help identify patterns and trends in email attacks, such as specific departments or employees being heavily targeted. By analyzing user-reported emails collectively, security teams can gain insights into the nature and scale of potential threats, allowing them to implement proactive measures to enhance email security.
Shortcomings of Traditional Abuse Mailboxes
While traditional Abuse Mailboxes serve a valuable purpose, they come with certain limitations:
- Manual Workflow: The workflow of traditional Abuse Mailboxes is predominantly manual, requiring SOC analysts to manually investigate and verify each reported email. This manual process can be time-consuming and inefficient, especially when a significant portion of reported emails are determined to be safe.
- Time and Resource Constraints: SOC analysts may spend a considerable amount of time evaluating employee-reported emails, diverting their attention from other essential security tasks. This inefficiency can result in an underutilization of valuable security resources and delays in addressing critical security issues.
- Reporting Inconsistencies: Employees may sometimes ignore or forget to report suspicious emails they receive in their inboxes. This can occur due to a lack of comprehensive security awareness training or a lack of a simple and easily accessible reporting mechanism. Inconsistent reporting by employees can result in missed opportunities to detect and address potential email threats.
- Flooded Abuse Mailboxes: Organizations that experience a high volume of email attacks or have a large number of employees can quickly overwhelm their Abuse Mailboxes. With limited resources and overwhelmed SOC teams, the timely processing and response to reported emails become challenging, potentially leaving the organization vulnerable to email threats.
- Inefficient Use of the Abuse Mailbox: Some employees may misuse the Abuse Mailbox by sending emails unnecessarily or seeking approval for every email they deem suspicious. This can lead to an influx of non-malicious emails, causing the Abuse Mailbox to become overcrowded and hindering the efficient processing of genuine threats.
How IRONSCALES Enhances the Abuse Mailbox
IRONSCALES offers enhancements to the traditional Abuse Mailbox by leveraging automation and AI-powered analysis to optimize email security operations. Here are some ways in which IRONSCALES enhances the Abuse Mailbox:
-
AI-powered Threat Analysis: Through AI-powered analysis, IRONSCALES automatically evaluates user-reported emails to determine their malicious or safe nature. This analysis helps identify potential threats accurately and efficiently, reducing the burden on SOC analysts to verify every reported email manually saving valuable time for SOC analysts and allowing them to focus on other critical security tasks.
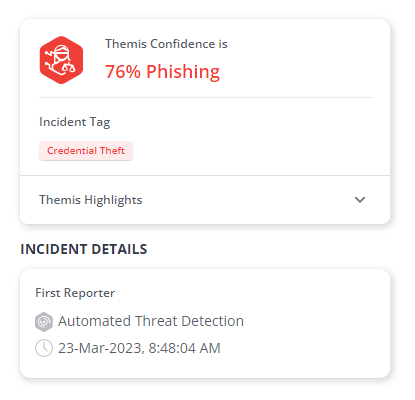
-
Auto-Remediation & Threat Clustering: When a malicious email is detected, IRONSCALES goes beyond individual email analysis. It identifies the entire email attack campaign associated with the threat and automates the process of removing all unreported emails from employee inboxes. This proactive approach helps prevent the spread of lookalike and polymorphic email attacks within the organization.
-
Search, Filtering, and Insights: IRONSCALES provides robust search and filtering capabilities within the Abuse Mailbox. SOC analysts can easily search through and filter user-reported emails based on various parameters, allowing for efficient investigation and analysis. Additionally, the platform offers insights into the attack types of malicious emails, enabling better understanding and mitigation of email threats.
-
Notifications and Reporting: IRONSCALES ensures effective communication with end users by providing email notifications. Users are promptly informed when an email they reported is deemed malicious, and they receive notifications about the remediation actions performed. This feedback loop helps foster a strong cybersecurity culture within the organization.
-
Comprehensive Campaign Details: The platform keeps detailed records of reported email campaigns, including relevant recipients, the email body, and the email header. This information assists in tracking and understanding the scope and impact of email attacks, enabling organizations to implement targeted security measures.
In summary, IRONSCALES' enhancements to the Abuse Mailbox through automation, AI-powered analysis, and comprehensive features result in improved efficiency, accurate threat detection, proactive remediation, and effective communication within organizations. By alleviating manual workload, enhancing security operations, and providing valuable insights, IRONSCALES strengthens email security and helps organizations combat email threats effectively.
Check out the complete IRONSCALES enterprise email security platform here or get a hands-on live demo.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












