Table of Contents
Accidental Data Exposure Explained
Accidental Data Exposure, also known as Sensitive Data Exposure, refers to unintended instances where sensitive data becomes accessible to unauthorized individuals or entities. This could range from personal information such as social security numbers and banking details to corporate data. It is crucial to distinguish between intentional data breaches, which are often the results of cyberattacks, and accidental exposures, which occur without malice or intent.
How does Accidental Data Exposure happen?
Accidental Data Exposure usually stems from oversights, errors, or lack of proper security awareness. Some common causes include:
-
Weak Encryption or No Encryption: Data that is not encrypted, or weakly encrypted, is easily readable if accessed. If this data is exposed inadvertently, unauthorized parties can easily interpret and misuse it.
-
Software Flaws: Sometimes, vulnerabilities in software can lead to unintended data leaks, especially if the software is responsible for data storage or transmission.
-
Human Error: Simple mistakes, like uploading data to an incorrect database, misconfiguring a server, or sending sensitive information to the wrong email recipient, can lead to significant exposures.
10 Common Ways Sensitive Data is Leaked
Sensitive data can be leaked through a variety of vectors. Some common vectors include:
-
Email and Messaging Systems: Accidentally sending sensitive information to the wrong recipient or inadvertently including it in email/messaging threads. Attackers also employ phishing tactics to deceive recipients into divulging confidential information.
-
Physical Theft: The theft of devices like laptops, smartphones, external hard drives, or paper documents that contain sensitive data.
-
Cloud Storage Misconfigurations: Incorrectly configured cloud storage buckets (e.g., AWS S3 buckets) that are inadvertently set to public, allowing unauthorized access.
-
Unsecured Network Transmissions: Transmitting data over unencrypted or poorly encrypted network connections can expose sensitive data to eavesdroppers or man-in-the-middle attackers.
-
Application Vulnerabilities: Weaknesses in software applications, such as outdated software or vulnerabilities to SQL injection, can be exploited to access sensitive data.
-
Social Engineering: Tactics used by attackers to manipulate individuals into divulging confidential information. This can include pretexting, baiting, tailgating, and other forms of deception.
-
Third-party Vendors: Often, sensitive data is shared with third-party vendors for various reasons. If these vendors do not have robust security practices, it can lead to data leaks.
-
Unsecured APIs: Application Programming Interfaces (APIs) without proper authentication or authorization checks can expose sensitive data.
-
Web Browsing and Downloads: Visiting malicious websites or downloading dubious files can result in malware infections that exfiltrate sensitive data.
-
Mobile Apps: Some mobile apps, especially those not sourced from official app stores, can have malicious code that accesses and transmits sensitive data.
Recognizing these vectors is the first step in creating a comprehensive strategy to protect against data leaks. Regular audits, updates to security protocols, employee training, and the implementation of both technical and administrative controls can help mitigate the risks associated with these vectors.
How to prevent Accidental Data Exposure
While the causes of accidental data exposure are varied, the steps to prevent them are consistent and can be broadly applied across various scenarios:
-
Invest in Security Training: Equip your team with the knowledge of cybersecurity basics. This includes practices like using robust passwords, recognizing phishing attempts, and understanding the importance of data confidentiality.
-
Implement Strong Encryption: Always encrypt sensitive data. In the event of an accidental exposure, encrypted data remains secure as it is unreadable without the decryption key. Additionally, always store encryption keys separately from the data.
-
Enhanced Security for External Storage: When utilizing third-party or cloud storage platforms, always add extra layers of security. This might include additional encryption or using private, non-public cloud directories.
-
Hire Security Experts: Especially for businesses that deal with vast amounts of sensitive data, having a dedicated security team or consultant is invaluable. They can identify potential vulnerabilities and recommend best practices tailored to your specific needs.
-
Conduct Regular Risk Assessments: Before embarking on any data processing activity, evaluate its potential risks. Tools like a Data Protection Impact Assessment (DPIA) can guide you in this process, ensuring that any potential pitfalls are identified and mitigated beforehand.
By understanding the nature of Accidental Data Exposure and being proactive in implementing preventative measures, individuals and organizations can significantly reduce the risk of unintentional data leaks, safeguarding the privacy and security of sensitive information.
IRONSCALES Accidental Data Exposure Prevention
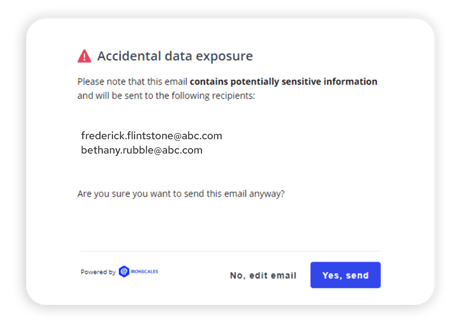
IRONSCALES helps prevent email-driven accidental data loss with real-time alerts. These mailbox-level alerts increase employee awareness and safeguard against the inadvertent transfer of sensitive data. The IRONSCALES Accidental Data Exposure capability utilizes advanced technologies to promptly identify and notify employees about emails that may leak sensitive data—enhancing their security awareness and proactively preventing potential data leaks in real-time.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)












