Learn the benefits of M365 Business Premium Defender
Cybersecurity incidents are increasing by the day and affecting all organizations, regardless of size or industry. Vendors have stepped in with different advanced cybersecurity products to help organizations fight these cybersecurity threats. One of these advanced cybersecurity solutions is Defender XDR (Extended Detection and Response).
Microsoft Defender XDR is one of the most popular XDRs in the industry and serves as a container for many of the security solutions that Microsoft has developed for its M365 suite, such as Microsoft Endpoint Detection and Response (EDR), Microsoft Defender for Office (MDO), and Microsoft Defender for Identity (MDI).
While Defender XDR contains a lot of components and security features, different M365 licensing modules provide customers with different sets of Defender XDR capabilities, and it can often be difficult to understand all these modules or tell the difference between them. Notably, one of these M365 licensing modules is M365 Business Premium, which is often confused with M365 Business Defender for Business.
In this article, we shed light on the M365 Business Premium license and discuss how it is superior to the standard Microsoft Defender for Business plan. We also discuss how to enhance M365 Business Premium with other security packages to significantly enhance your cybersecurity protection without needing to acquire more expensive licenses, such as Microsoft E3 or E5.
Summary of key M365 Business Premium components
The table below lists the main components that are included in the M365 Business Premium licensing model.
| Component |
Description |
|
M365 Defender for Business (MDfB)
|
MDfB contains Microsoft's EDR solution, attack surface reduction, threat and vulnerability management, and more.
|
| Microsoft Intune |
Included with the premium license, Microsoft Intune is the cloud-based unified service for managing both corporate and BYOD devices. |
| Exchange Online Archiving (EOA) |
EOA helps organizations manage their email data securely in the cloud, provides users with additional mailbox storage for their email content, and specifies email retention policies. |
| Windows 10/11 Business |
Windows 10/11 Business is a set of device management capabilities that complement Windows 10 Pro for the centralized management and security control of devices that are part of Microsoft 365 Business Premium licensing. |
| Enhancement possibilities |
Despite M365 Business Premium being a premium license, it can be further enhanced with add-on packages or other third-party email security solutions to improve your security defense as a whole. |
M365 Defender for Business (MDfB)
MDfB (standalone) is the standard Defender XDR licensing model that Microsoft offers for small and mid-sized organizations; it is often confused with “M365 Business Defender Premium,” which doesn’t actually exist. The premium license for businesses is actually named “M365 Business Premium” (note the missing word “Defender”). That’s because M365 Business Premium doesn’t provide any extra Defender XDR features compared to the MDfB license; rather, it complements it with other necessary solutions, which we will see in this article, e.g., Microsoft Intune.
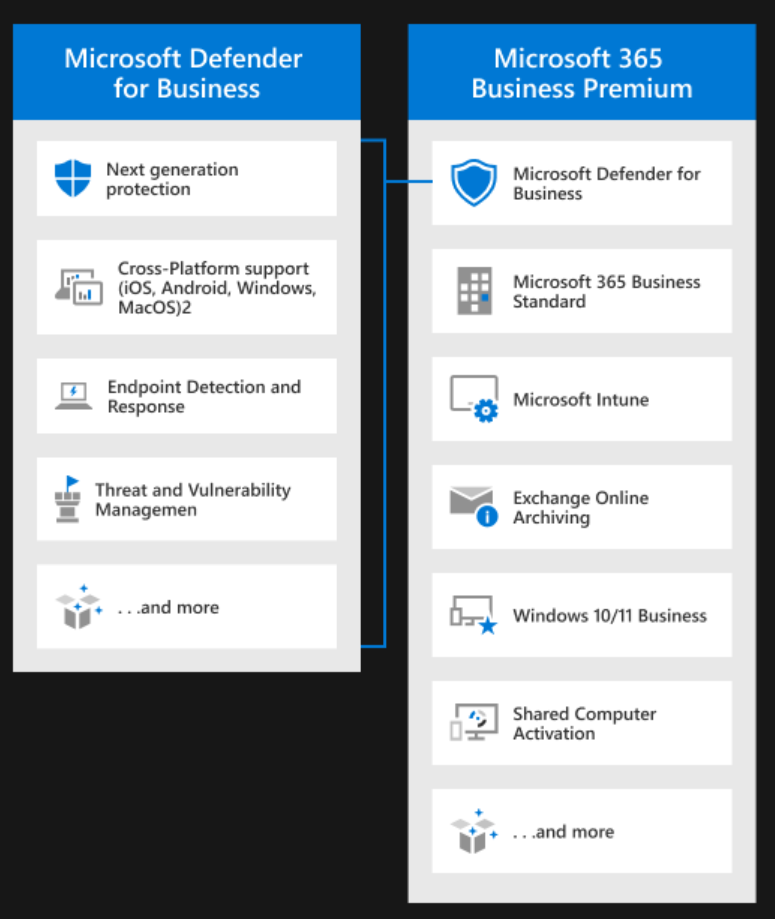
MDfB as part of the M365 Business Premium license (source)
Despite M365 Business Premium not providing any additional advanced features for Defender XDR, MDfB alone provides many of the crucial security features of Defender XDR and is often enough for most small and medium-sized companies:
- Microsoft Defender for Endpoint (MDE): Microsoft’s EDR solution continuously monitors all activities on endpoint devices—ranging from memory allocations to network connections—correlates all logs to detect complex attacks and alerts the security team about suspicious behavior on endpoint devices. It is one of the core components of Defender XDR.
- Attack Surface Reduction (ASR): This is a set of rules that can be activated to reduce the attack surface and make it harder for attackers to achieve their goals. For example, one of the ASR rules can prevent Office applications from spawning dangerous child processes, such as PowerShell.exe or cmd.exe, which are often abused in phishing attacks with malicious Office attachments. A detailed overview of ASR rules and their usage can be found here.
- Auto Investigation and Remediation (AIR): Depending on how it is configured, AIR is a feature that will immediately start an automated investigation the moment an alert is generated by Defender XDR, such as “Email reported by user as malware or phish”, and will try to automatically remediate it, reducing the burden on the security team (which would otherwise have to manually analyze all alerts one by one).
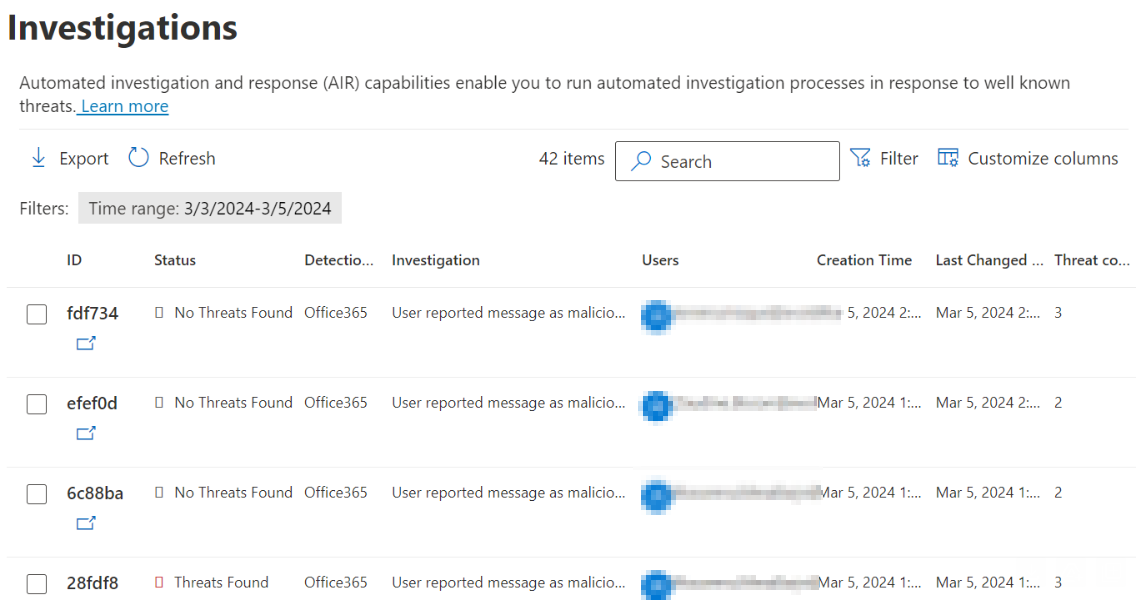
List of AIR investigations in Defender XDR
- Threat and Vulnerability Management: This is a useful module in Defender XDR that helps provide companies with an overview of their software inventory, patch status, and what vulnerabilities affect them, complemented with recommendations on how to remediate issues.

Microsoft Intune
Microsoft Intune is Microsoft’s cloud-based management solution for all kinds of devices—including on-premises or cloud, corporate, or BYOD devices—and with support for a variety of underlying operating systems. Here are some of its benefits:
- It simplifies M365 application management, updating, and patching, as well as deploying application protection policies.
- It automates policy deployment for updates, configuration changes, the deployment of compliance or conditional access policies, etc.
- Microsoft Intune integrates and connects with MDE to scan files, detect threats, and trigger alerts in MDE so that the security team can respond to threats.
- It blocks non-compliant devices from accessing your organization’s data, including emails or other M365 cloud data, until the device is compliant again.
- Device enrollment for any kind of device—Linux, Mac, Windows, smartphone OS, etc.—is supported for both BYOD and company-owned devices.
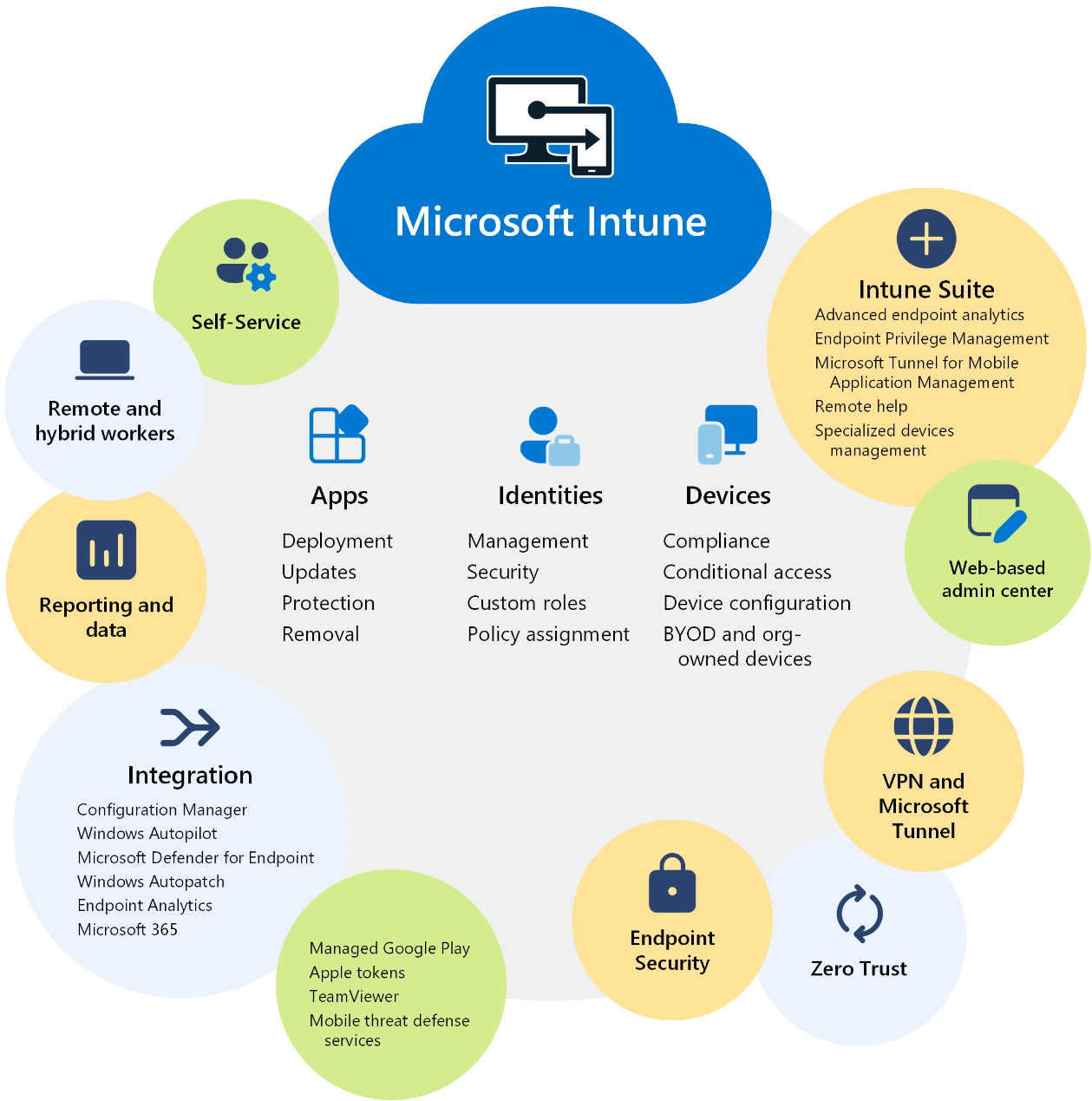
Overview of Microsoft Intune capabilities (source)
Exchange Online Archiving (EOA)
EOA is a cloud-based archiving solution and part of the M365 suite. It helps organizations manage and store their email data securely in the cloud, providing several helpful features for organizations to make it easier to handle email data, such as these:
- Storage management: EOA helps organizations optimize mailbox storage, expanding space for business-critical mailboxes or archiving older, less-needed emails to free up space.
- Email retention: It enables the organization to decide how long email data should be kept before being deleted by setting up appropriate criteria, such as age or (email) folder location.
- eDiscovery: EOA includes advanced capabilities to search for certain terms across all emails of your organization, supporting different kinds of investigations or security incidents.
- Compliance requirement and management: It helps organizations meet different regulatory and compliance requirements and integrate with the M365 compliance portal, where administrators can manage such requirements centrally.
There is, however, some confusion in the market about EOA archiving and the possibility that employees can delete emails from the archive, which are often important for legal/compliance use cases. In EOA, once an employee deletes an email, the email will be placed in a special folder called “Recoverable Items,” where it will remain for at least 14-30 days, depending on the configuration.
This special folder is hidden, so employees cannot find or interact with it from their mailboxes. They also cannot delete an email from the archive, i.e., from this hidden folder, unless they have administrator permissions on their computers or can connect to the Exchange Online server via PowerShell. This helps organizations with legal/compliance cases by ensuring that no unprivileged employee can permanently delete an email from the archive.

Windows 10/11 Business
Windows 10/11 Business should not be confused with Windows 10/11 editions, such as Home, Professional, or Pro. Windows 10/11 Business is a set of additional cloud services and device management capabilities for Windows 10 Pro. It enables the centralized management and security controls of Windows devices with a valid Microsoft 365 Business Premium license.
While Microsoft doesn’t expand more on this, according to different administrators and blogs on the Internet, one of the few benefits of Windows 10/11 Business for endpoints is the ability to centrally manage them easily via Microsoft Intune.
Enhancement possibilities
Microsoft 365 Business Premium lays a solid foundation for protecting your small or mid-sized business. Yet, by integrating specialized add-ons—either from Microsoft or other trusted partners—you can bolster your defenses, filling in any gaps and enhancing the robust security features Business Premium offers.
Add-on packages
The Microsoft 365 Business Premium license only covers endpoints. If your organization operates business-critical servers, consider the Microsoft 365 Business for Server add-on package to benefit from all the security features that Microsoft offers for servers. Additionally, other add-on packages that can be integrated with the premium license include Microsoft Teams Phone (a cloud-based phone system) and audio conferencing, which allows you to join Microsoft Teams meetings even if you don’t have an internet connection.
IRONSCALES
With phishing attacks being the main initial attack vector in most cyberattacks and often leading to ransomware, investing in email security is crucial for the success of your cyber defense. IRONSCALES provides several products to aid your company in combating the phishing threat:
- Easy two-click integration with Office 365 and Teams with an automated security scan of your emails stretching back 90 days.
- An AI-powered email security feature for Outlook equips employees with a straightforward "Report Phishing" function, facilitating prompt escalation of suspicious emails. Additionally, it provides real-time insights and essential security advice, aiding employees in identifying and handling potential threats with greater confidence.
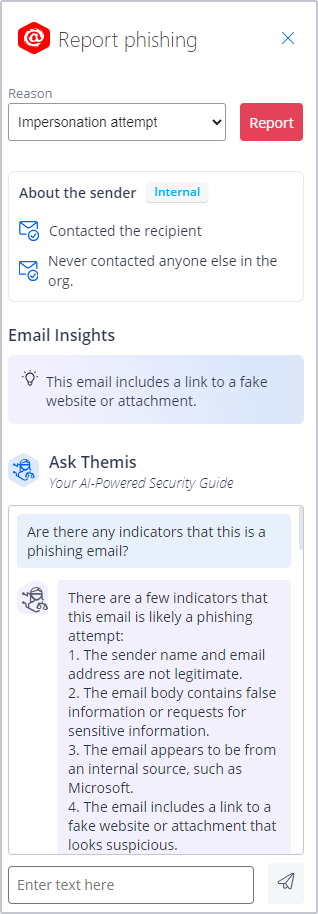
IRONSCALES Themis CoPilot Phishing Button (source)
- A large variety of automated security awareness training (SAT) options, with up-to-date phishing examples from the latest phishing trends. This can be further complemented with one-click phishing simulations to measure the effectiveness of the training and to identify employees who need additional phishing training.

Conclusion
Microsoft has invested a lot in many security products for its M365 suite. However, providing numerous licensing models for the same security tools makes it often difficult to understand the differences between the various licensing models it offers.
In this article, we covered Microsoft’s Business Premium license for small or mid-sized companies in detail. We clarified the difference between it and Microsoft Defender for Business, with Microsoft Business Premium being the most comprehensive of the two. We also looked into how to enhance it with add-on packages from Microsoft or comprehensive email security solutions in the market without needing a more expensive solution (Microsoft E3 or E5).

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










