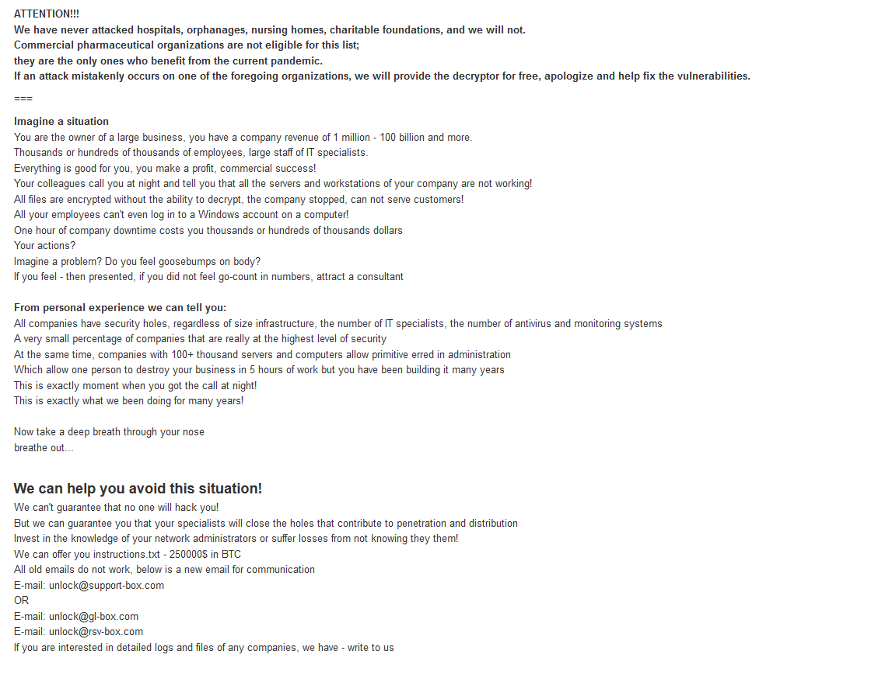
Table of Contents
What is CLOP ransomware group?
CLOP is a notorious high-profile ransomware group that has compromised industries globally. Like other ransomware groups, CLOP hosts a leak site to pressure their victims into paying the ransom they demand.
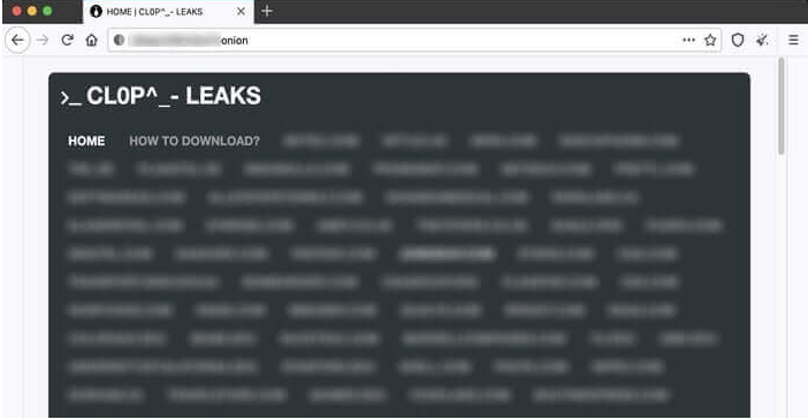
How did we encounter it?
Employees who are personally related to CLOP victims started to receive work emails about future leaks. They were warned that their private information would be published on the dark web should certain conditions not be met.
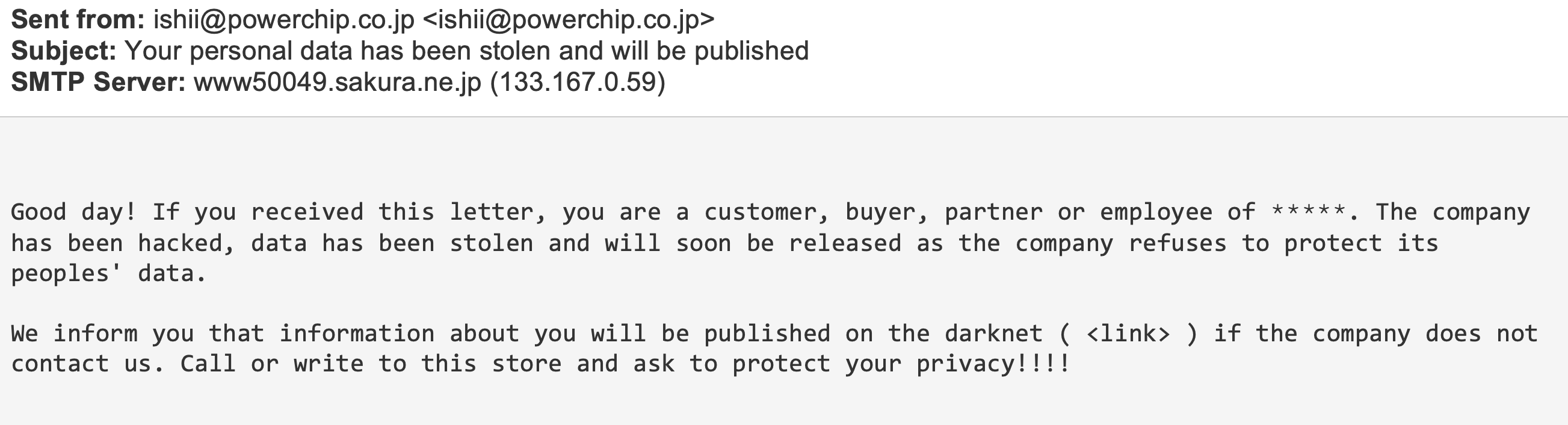 *The company's name was deleted from the email body due to privacy concerns.
*The company's name was deleted from the email body due to privacy concerns.
In the attached link in this email, the recipient will find an ‘onion’ domain website used in the Tor browser designed for anonymous browsing and difficulty to trace.
This onion website directs to the CLOP Tor-hosted leaks webpage, which includes all the companies breached by the CLOP group, information about those companies, and the data they published to show they mean business.
(Image above is an example of a personal document exposed by the criminals. Personal details have been removed from the image.)
How the ransom works
The CLOP group employs a ‘steal, encrypt and leak’ technique for their chosen victims. Victims who don’t comply with the CLOP group’s demand have their personal information published on the CLOP Tor-hosted leak website. Personal details that can be found on this site include email correspondence, private documents, photos, employee identification details, passport information, and much more. The CLOP ransomware group is known to release small bits of stolen information over a period of time while ratcheting up the pressure on the victim to comply throughout.
Phase 1 – Infiltration
In phase 1, CLOP exploits the company’s public-facing infrastructure vulnerabilities to gain access to their network, in addition to malspam campaigns to lure employees to infect themselves with malicious files.
The malspam campaigns were conducted during the week to ensure maximum employee availability to respond, and the network intrusion was conducted during the weekends to ensure minimal chance of detection.
The malspam campaign often used compromised email addresses and names from existing victims (customers, vendors, partners, or other persons of interest of CLOP target), so the campaign would be incredibly convincing with a minimal chance of detection.
Phase 2 - Collection
After infiltrating their victim network, network storage devices, and file servers, CLOP begins to search for the sensitive data they aim to collect.
It can be employee emails and correspondence, financial documents, customer information, and other data that can damage the victim if it is published or get into the wrong hands.
Basically, CLOP wants to collect every drop of data that can add pressure on their victims to pay the ransom and fast.
Phase 3 – Encryption and Announcement of the Ransom
After extracting all the files needed to threaten their victim, the ransomware is deployed.
CLOP deploys their ransomware upon their victim via executable codes, which results in restriction of every crucial service they need (backups software, database servers, etc.) with the addition of some applications being forcibly terminated until the ransom is paid.
Also, CLOP ransomware group often deletes any shadow backup copy that could have been created at a historical point of time by VSS (Volume Shadow Copy Windows Service).
Meanwhile, all the relevant company data is transferred and encrypted to the CLOP Tor-hosted leak webpage with a variation of the word ‘CLOP’ as an extension (‘cl0p’/’CLOP’/’cllp’ etc..) and a unique ransom note to their victim is published to them in a txt file, often a ‘readme.txt’ file.
The ransom note informs the victim of the ‘latest events’ and describes the demands and the non-compliance actions.
Unlike other cyber-criminal groups, instead of providing their victims with a sum of money and a cryptocurrency address, CLOP leaks a list of contact email addresses (hosted on privacy-focused email providers to provide anonymity) or a link to an online chat (hosted by Tor hidden service) for negotiations.
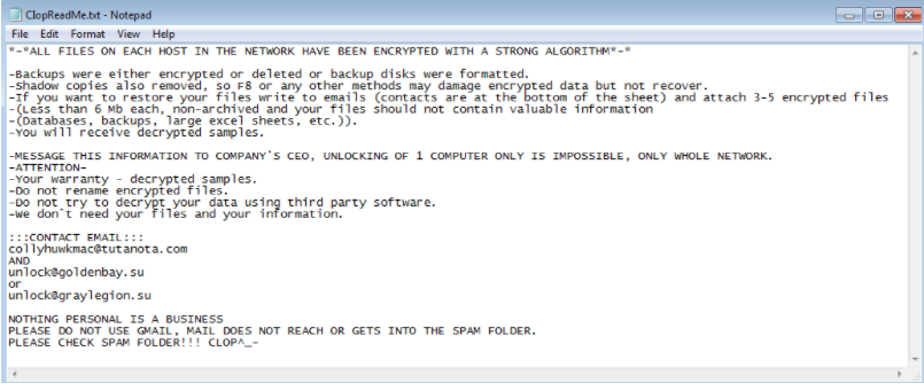
(Image above is an example of a ransom note)
Tips to prevent/mitigate malware
- Invest in cybersecurity tools and services that will detect and prevent threats before they can become an issue.
- Think twice before you open an email attachment or click on links. If the email address or the email content looks suspicious, do not open it!
- Keep your software up to date to ensure that you have the latest security capabilities deployed.
- Do not provide any personal information when answering an email, text message, or instant message. Phishers can gain intelligence by disguising themselves as IT services or other employees and tricking employees into giving them information that can help them with their attack.
- Perform regular system backups and network security assessments.
- Segment your network using firewalls, micro-segmentation and/or other techniques; cyber criminals cannot exfiltrate what they cannot access.
To learn more about IRONSCALES’ award-winning anti-phishing solution, please sign up for a demo today.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)