Table of Contents
Attack Summary Details
- Impacted IRONSCALES customer mailboxes: 5,870
- Impacted IRONSCALES customers: 1,282
- Security Bypass: SPF, Visual Scanners
- Technique: Social Engineering, Malicious Payload, Clone Phishing
Background
Credential theft phishing is one of the most common forms of cyber attacks. These types of attacks are dangerous, effective, and easily scalable. Dangerous because credential theft leads to account compromise. Effective because the emails mimic legitimate vendor emails. Scalable because the generic nature of these emails allows them to be sent en masse with very little effort or expense.
The Attack: Method & Payload
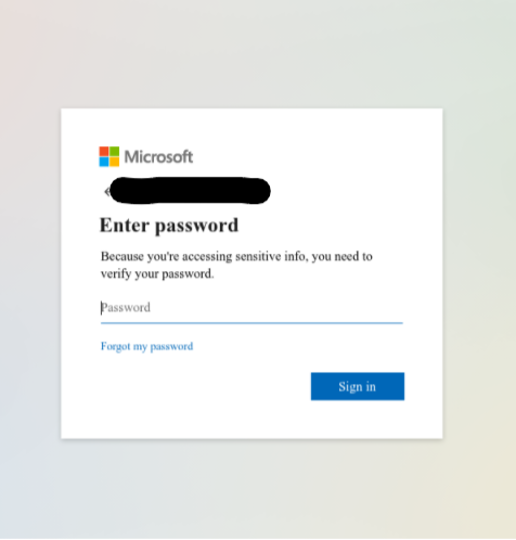
In this phish, the attackers sent an email that impersonated Microsoft and purported to notify the recipient that their account password has expired and needed to be changed. Should the victim have clicked “Keep Your Password now” in the email body, they would have been directed to a malicious landing page.
Recipient: M**** L**** <m*****@s********.com>
Sent from: Remind <editors@fiercepharma.com>
Subject: Your Password Expired!
SMTP Server: wfick.sohab.com (164.90.204.155)
Notification Microsoft Office 365 Alert Dear infoCompany: s***** Email: i***@*****.comAcess To Your Email will be Expired,To use Your current acess or change it click on Button Below Keep Your Pa
Danger: External (editors@fiercepharma.com)
Brand Impersonation, Reported Spam, and more... Details
Report This Email FAQ Skout Email Protection
Microsoft Office 365 Alert
Dear info
Company: s*****
Email: i***@s******.com
Acess To Your Email will be Expired,
To use Your current acess or change it click on Button Below
Keep Your Password now
PM Tracker
September 17, 2021
This week's sponsor is TransPerfect.
Implementation Guide: Top 10 Considerations When Implementing Machine Translation (MT)
Our checklist reviews 10 essential factors to consider when implementing MT for your life sciences content so you can leverage the benefits of increased quality, reduced costs, and shortened turnaround times that this technology offers. Download now!
Today's Rundown
Excision's CRISPR gene editing therapy for HIV is heading into human testing after FDA clearance
Humana rumored to be eyeing Centene takeover, again: report
COVID-19 tracker: Key FDA panel votes down Pfizer's booster application; Biden admin to buy millions more Pfizer jabs
Medtronic buys implanted infusion pump tech to develop new Type 1 diabetes therapy
Gilead's slumping COVID-19 drug takes another hit with study showing no real benefit
Lead exposure continues to be a 'silent epidemic' for kids. These 3 states have the most affected areas
With new facility and leadership, CDMO Genezen is stepping up to the big leagues
New insights into bats' immunity could point to therapeutic approaches for fighting COVID-19
FTC warns health apps must notify users about data breaches or face fines
Fierce Pharma Asia—Takeda's lung cancer nod; 4th death in Astellas' gene therapy trial; Everest's mRNA play
Chutes & Ladders—AltruBio snags new CMO with resume at Sublimity, Ardea, Amgen and Abbott
Publisher: Rebecca Willumson
Associate Publisher: Angelique Alcover
Advertise | Contact
Manage Your Subscriptions
Trouble with your subscription?
Contact Support
Privacy Policy
This email was sent to *********@g***.com as part of the Fierce Life Sciences email list
Payload
The payload in this attack is a fake Microsoft login page.
What to look for
From the perspective of the recipient, understanding email anomalies can help prevent the execution of the attack. The spelling mistakes highlighted in the sample attack email above are typical in phishing emails. While the language and template used in this attack are common, the addition of a newsletter text in the email body is rare and makes this attack unique. The reason why cybercriminals use such a technique is to evade or confuse NLP (Natural Language Processing) based detection mechanisms.
How We Handled This Attack
Our AI named Themis was able to identify and mitigate this attack. She immediately pulled the phishing emails out of the inboxes of all our impacted customers.
To learn more about IRONSCALES’ fully integrated anti-phishing and security and awareness training solution, please sign up for a demo today at https://ironscales.com/get-a-demo/.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)









.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)