Table of Contents
When we think about vishing (voice phishing), the usual suspects come to mind: fake refund scams impersonating Norton, PayPal, or Geek Squad.
When one of our security researchers brought this campaign to my attention, I knew right away it was something different.
This wasn’t your typical refund scam or tech-support vishing attempt. Instead, it was targeting something much more personal, healthcare appointments.
It’s smart. It’s subtle. And it works because it feels personal.
Let’s break down how this attack plays out.
IT Security Admins: If you’re thinking this doesn’t concern you because it sounds personal, not corporate, stick with me. I’ll explain why these attacks still matter to you.
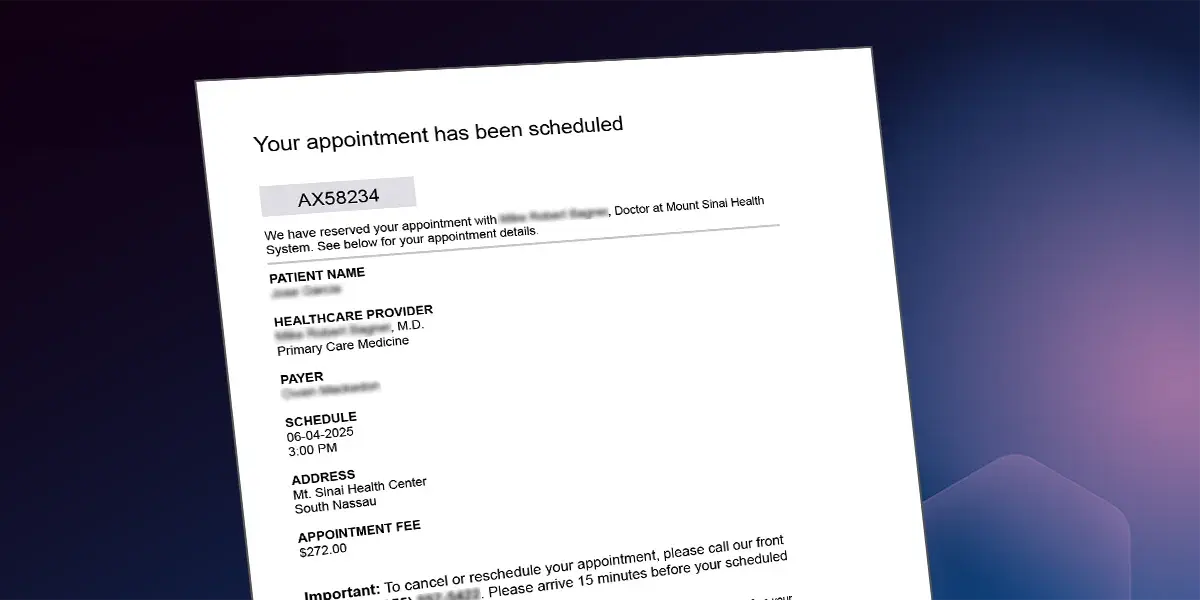
It Starts with a Simple Appointment Email
Actually, the email is nothing flashy. It’s a polite confirmation for an upcoming medical appointment. No links. No malware. Just a friendly heads-up that you’ve got something on the calendar, with an attachment that holds the details.
But open that attachment, and here’s what you’ll see:

Here's what it includes:
- "Your" name (personalized)
- A real healthcare provider’s name (Mount Sinai, Healthgrades...recognizable names)
- An appointment fee of $272
- And a phone number to call if you need to reschedule or cancel
Why This Gets Past Defenses (and People)
Unlike a business email compromise (BEC) attack, there’s nothing inherently malicious in the email itself. No links to fake or shady websites. No suspicious attachments to scan. The danger is all in the social engineering, and the phone number in that PDF.
Here’s why this kind of thing works so well:
1. It Leans on Human Nature
Let’s be honest...most of us feel a little uneasy about healthcare billing. It’s confusing, stressful, and when an unexpected charge shows up, the instinct is to fix it right away.
2. It Slips Past Traditional SEGs
No links? No malware? No keywords to match a filter? There’s nothing to trigger traditional defenses. It's a perfect example of what I talked about in my analysis of almost 2,000 customers' SEG gaps (Barracuda, Cisco IronPort, Mimecast, and Proofpoint SEGs).
This one’s about manipulating behavior, full stop.
3. It Looks Legit
With your name in the message and familiar healthcare brands in the mix, it feels authentic. The attackers aren’t rushing or threatening, they’re relying on trust.
Is This Really an IT/Sec Admin Problem?
It’s easy to dismiss this kind of attack as personal, something that lands in an employee’s private inbox, not their work email. But attackers don’t think that way.
Personal attacks often spill into the workplace:
-
Employees use the same devices for personal and work email.
-
Personal stress impacts professional decision-making.
-
Social engineering doesn’t stop at home, it often pivots into corporate networks once trust is established.
Most importantly, for IT Security Leaders, this is an opportunity to teach and empower employees to recognize these types of attacks. A tactic like this could easily pivot to business targets (and because it feels personal and relatable), employees are more likely to pay attention. When it hits close to home, it feels more real.
The Attack Flow: From Email to Phone Call
Let me walk you through the sequence:
-
The email hits the inbox
Just an appointment confirmation, nothing jumps out. -
You open the attachment
Now you’re staring at a fee for an appointment you don’t remember scheduling. -
You call the number
Wanting to clear things up, you dial and land right in the attacker’s lap. -
They work their script
From here, they can ask for payment details, personal info under the guise of verifying insurance or resolving the issue.
All of this happens without a single piece of malware hitting your system.
An Emerging Twist in Phishing
I’ve seen vishing attacks combine email and phone before, but the healthcare angle adds a new layer. It plays on the same techniques we’ve seen for years, emotional triggers, urgency, and trust - but in a space where people are often more vulnerable.
And that’s the point...attackers don’t always need a link or attachment to capture personal data, they just need you to pick up the phone.
What To Do
I know no one wants to hear “train your users” again, but this kind of attack really leans on people, not just technology.
What security teams can do:
- Educate users on how these tactics work (and yes, that includes phone-based scams)
- Remind folks that just because it looks like it’s from a trusted brand doesn’t mean it is, especially when phone numbers are involved
- Implement domain authentication (like DMARC) to reduce the chances of your brand being spoofed in phishing campaigns. While it won’t stop every attack, DMARC helps ensure emails sent from your domain are trusted and provides visibility into who’s trying to impersonate you.
- Monitor for patterns, even if there’s no malware, similar emails hitting multiple inboxes should raise flags
- Get ahead of multichannel scams, remember, phishing isn’t just about email anymore, think about voice, SMS, deepfakes, and more
This attack stood out to me because it’s just...simple. A convincing setup and a phone number, that’s all it takes. It works because it feels real.
Want to learn more about how DMARC works and how it can help defend your brand? Check out our overview here.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)