Table of Contents
Imagine for a minute that you are the CISO of a financial institution. One morning, a member of your security team hastily awakens you and informs that a major ransomware attack took place overnight. Despite millions of dollars spent on cybersecurity safeguards, the core processing system that connects your bank’s headquarters to all of its local branches has been severely compromised.
Your security operations team soon discovers that the attack has prohibited the bank’s branches from making entries; checks and debits are unable to be paid and transactions cannot be honored. In addition, information about ten thousand customers, including names and social security numbers, are missing. Finally, the team finds a ransom note requesting $25 million for the return of the data and the removal of the malware paralyzing the core processing system.
A catastrophic event like this would affect not just your bank, but also the stability of the national and global finance industry. Could you possibly think of a worse situation to be in?
Ransomware Attacks. A Growing Epidemic
Unfortunately, ransomware attacks such as the one described in the scenario above happen at an alarming frequency. These types of attacks, which often result from a successful email phishing or spear-phishing campaign, are designed to take over a bank’s internal system, lock down computers and encrypt any data that is in the system.
Because the motive for data breaches is increasingly financially focused, banks are a hot target for cyber hackers despite millions spent on security solutions. Verizon’s Data Breach Investigation Report concludes that 89% of breaches in 2015 were motivated by greed or espionage. Earlier this year, cyber terrorists hacked into the Bank of Bangladesh’s account at the New York Federal Reserve Bank via Swift, a global messaging network. With this access, the hackers were able to steal over $80 million from the bank.
What’s most alarming is that attacks on banks and the specific details of such attacks are hardly ever reported. The Global Head of the Fraud Prevention Division at Kaspersky Laboratory, Ross Hogan, explains that, “you’re almost certainly not going to hear about successful ransomware attacks on banks.” Without media attention, these attacks occur much more frequently than you may believe.
Ransomware Attacks. The Five Stages.
A subtle email that appears non-threatening can infect any bank almost instantly. For a glimpse into what a day in the life of a ransomware attack would look like, follow the five stages of an attack below.
- A nation state or hactivist group conducts reconnaissance. The adversary diligently researches what your bank’s email templates look like, how email signatures appear and what kind of verbiage is typically used.
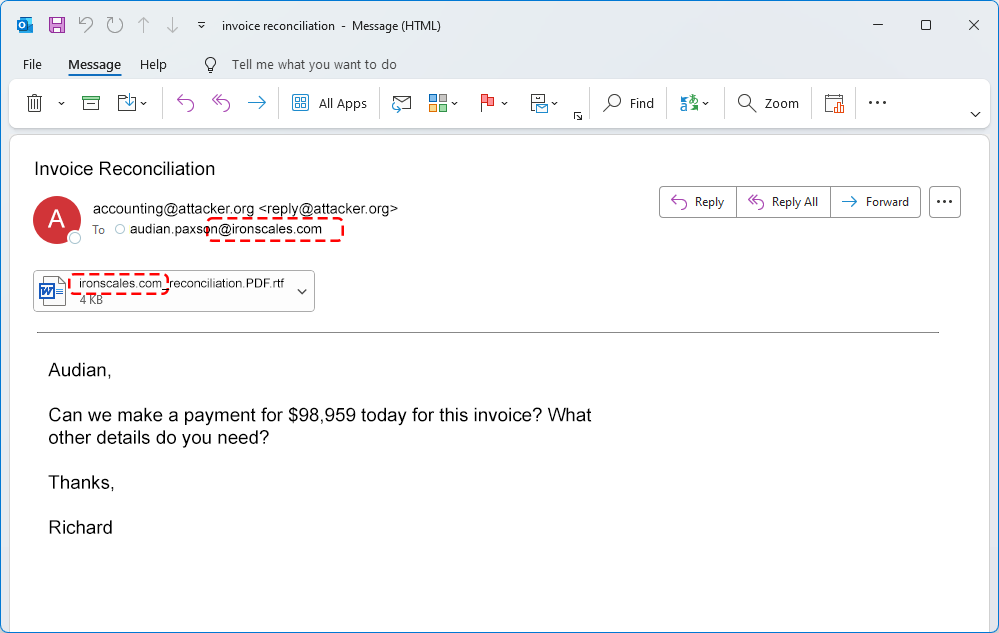
- Next, the adversary launches an email phishing or spear-phishing campaign that targets employees. Those targeted can include anyone from a janitor to a CEO.
- Unfortunately, because the email appears authentic, an employee opens the email, downloads an attachment or clicks on a link. Upon doing so, malicious code is injected into the endpoint, at which time access to networks, servers etc. is obtained.
- Once inside, the adversary is free to access and manipulate critical data, network configurations, and proprietary information. This information is then extracted and encrypted so only the adversary can access.
Finally, the adversary creates a ransom note, which can seek tens of millions of dollars, and holds the information until your bank meets the requested demands.
Determining whether or not to pay the ransom is a decision that every a financial organization must make on its own. Fortunately, new technology exists to prevent organizations from ever having to make this choice.
Stop Ransomware by Mitigating Phishing Attacks
IRONSCALES is the leader in anti-email phishing technologies. Using a multi-layered and automated approach to prevent, detect and respond to today’s sophisticated ransomware attacks, IRONSCALES expedites the time from ransomware attack discovery to enterprise-wide remediation from months to seconds, by significantly reducing the workload on incident responders. Our process is simple: IRONSCALES first challenges all users with a series of staged, real-world email attacks in order to evaluate their individual level of awareness. Based on an analysis of performance, a tailored phishing training campaign, using advanced simulation and gamification, is created to maximize individual awareness and responsiveness to social engineering techniques.
Once trained, vigilant employees, upon suspicion of a phishing attack, can trigger a real-time automated forensic review through the click of just one button, without requiring active SOC team participation. Within minutes, forensics is completed, and an intrusion signature is sent directly to both endpoints, email servers and the SIEM, which then triggers an immediate enterprise-wide automatic remediation response, such as quarantines, disabling of links and attachments, and even permanent removal of email, protecting the entire organization from the attack. Important event information is then automatically and anonymously shared via Federation to ensure the same attack won’t hit any other company under IRONSCALES protection.
Think of a phishing campaign like the head of a snake. Once you cut it off, the rest of the body cannot function. Similarly with ransomware, if phishing attacks can be cut off, the ransomware has no chance to making into the networks, servers and beyond.
For more information on how IRONSCALES can protect financial services organizations from phishing and ransomware attacks, Contact Us
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)