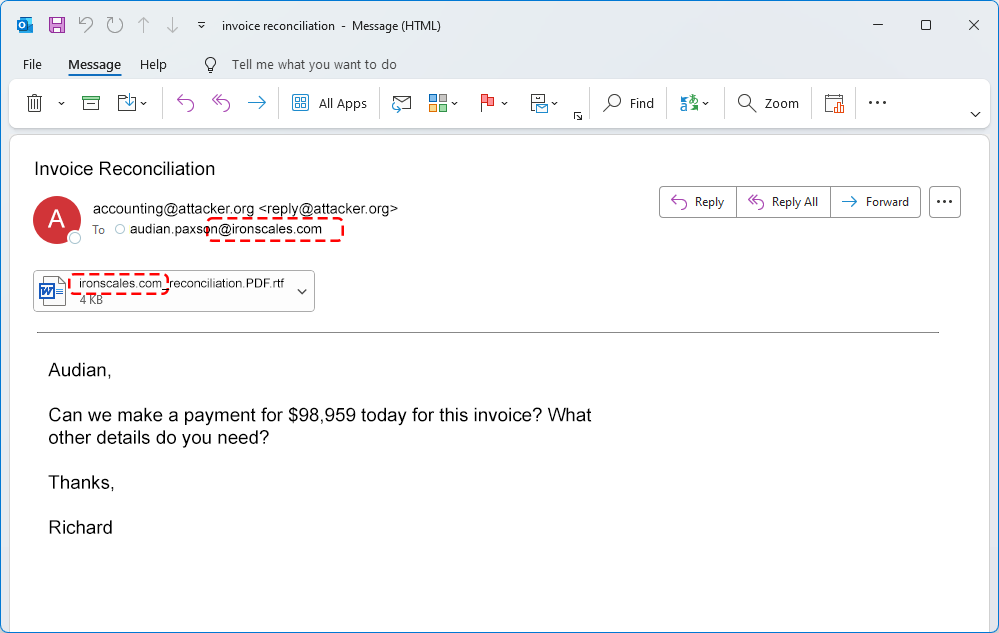
The 2025 Phishing Surge Proved One Thing: Chasing Doesn't Work

Let's get something out of the way: retrospectives are mostly an eye roll when I see them. Mandatory-yet-irrelevant information I have seen over the course of the past 12 months. Someone gathers up the...
Read more
/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)









.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)