Office 365 Email Security
Phishing is one of the oldest types of attacks, but it continues to lure companies into risk. Why? For one simple reason: It is still effective. In fact, according to Microsoft, phishing is the preferred method of threat actors to deploy ransomware–causing considerable financial and reputation damage to companies.
As the digital landscape evolves, the cybersecurity sector is ramping up its arsenal with an array of sophisticated tools to tackle phishing—spanning from endpoint detection and response (EDR) systems to advanced email safeguards and proactive training programs. Among the latest innovations is Microsoft Defender for Office (MDO), which unites a suite of email security functions within an M365 tenant, seamlessly woven into the fabric of Microsoft's EDR ecosystem, Microsoft Defender.
Although potent, MDO's complexity can be daunting with many features that are sometimes hard to configure or understand. Complicating the situation further, Microsoft keeps changing its EDR solution to integrate all Microsoft “Defender For <Product_Name>” options in a single platform with one UI, making it sometimes hard to keep track of the constant changes and where the email security features reside. To help clarify, in this article, we will cover the main email security features that MDO provides, where they reside, what the purpose of each is, and the possibilities for adjusting the configuration.
Summary of key Office 365 email security features
The table below lists seven crucial email security features in MDO that we will describe in this article.
| Email security feature |
Description |
|
Email logs and incident response (IR)
|
These features review all logs for inbound and outbound emails and let you choose from a variety of options for managing suspicious emails.
|
| Alert policies |
Lets you use built-in email security policies and alerting or create your own custom alerting for suspicious emails. |
| Report phishing button |
Users can press the phishing button to report a suspicious email to the security team. |
| Email quarantine |
You can decide what happens with emails that are blocked by one of the anti-phishing policies. |
| Anti-phishing policies |
This feature lets you view and modify anti-phishing policies that can be configured on the Microsoft Defender portal. |
| Zero-hour auto purge (ZAP) |
A feature that recognizes and deletes emails that were initially allowed but later considered malicious (exhibited malicious behavior when interacting with them). |
| Real-time threat intelligence (TI) |
Leverages threat intelligence from Microsoft's extensive global network to enhance detection capabilities. |

Seven email security features of Office 365
In the sections below, we present details on seven main email security features of MDO (for Office 365) that can be configured and used to protect Office 365 users from phishing attacks.
Email logs and incident response (IR)
All emails that are sent to or from users that use Exchange Online (part of Office 365 apps) will be logged and can be viewed in Microsoft Defender, where MDO is currently integrated. More accurately, based on your permissions, you can view the email’s metadata, such as the sender, recipient, subject, email address of the sending server, anti-phishing policy verdicts, the direction of the email, URLs and/or attachments, and email security protocol (DMARC, DKIM, SPF) verdicts. You can then use any of these pieces of information to search for emails of interest from the UI (under Email & collaboration → Explorer):
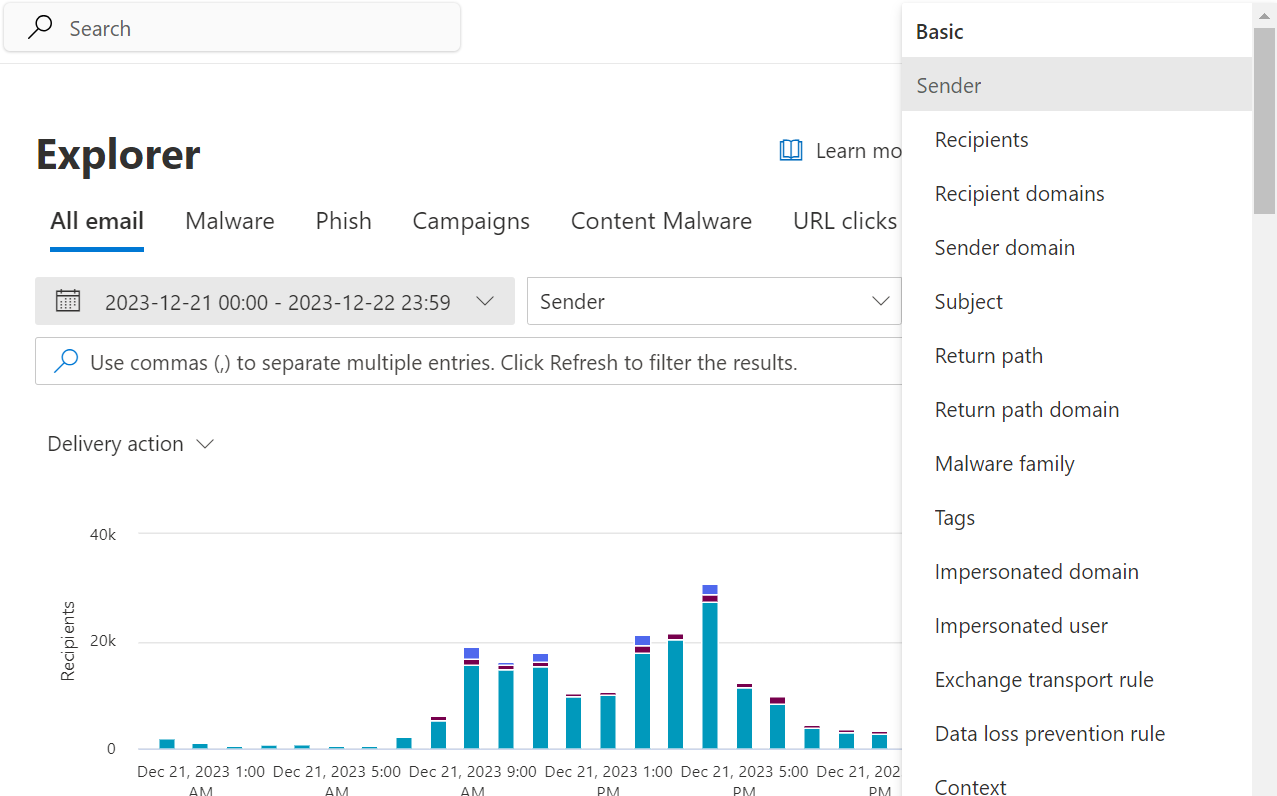
MDO: searching emails of interest with Explorer
While you cannot view or download the original email itself (with standard permissions), the amount of information provided is often enough to decide whether the email is malicious or safe.
Once malicious emails are identified, the real work begins. Armed with the appropriate permissions, you can take several different actions as part of the incident response, such as deleting the email, reporting it to Microsoft, moving it to the junk folder, etc.
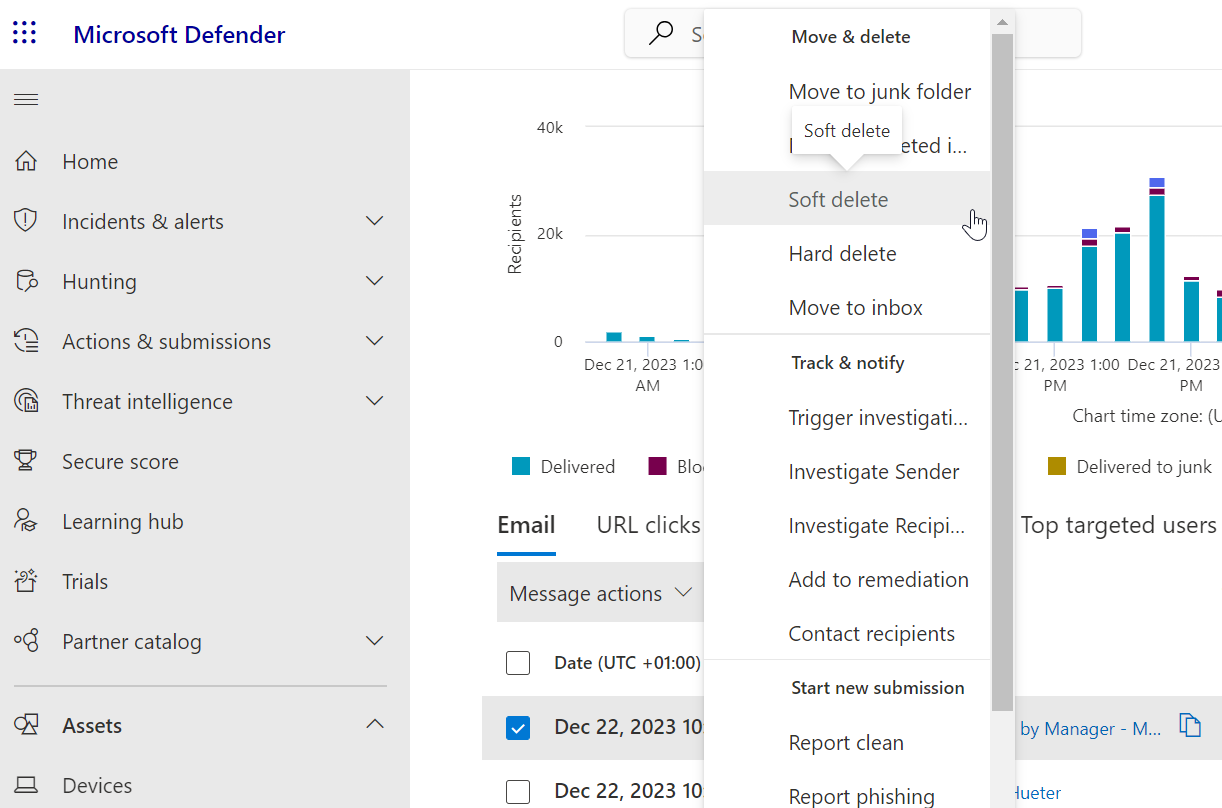
MDO: taking action against suspicious/malicious emails
Explorer also provides statistics about emails that might be relevant for an overview of the phishing landscape. While we will not dive deep into each of these features, we can mention statistics such as the number of users clicking on phishing emails, graphics based on filtering/search in the UI, potential phishing campaigns, top targeted users (based on the number of emails they receive), etc.
Additionally, MDO equips you with other IR capabilities—such as blocking sender domains, specific sender email addresses, URLs, and file hashes (i.e., email attachments)—to prevent future malicious emails that might target your company.
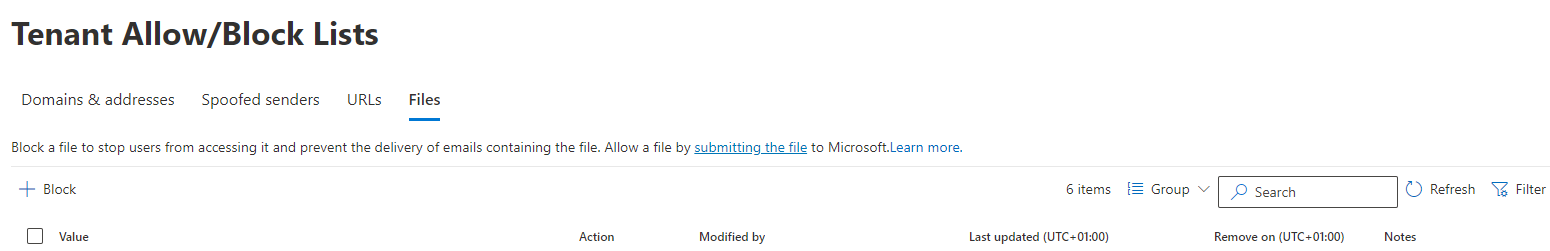
MDO: blocking capabilities to empower IR staff
Note that Microsoft doesn’t provide you with the option of adding specific senders to an allowlist. Instead, you need to submit false positive emails (i.e., considered malicious when actually benign) to Microsoft directly. Only then will Microsoft manually analyze them and decide whether MDO incorrectly labeled the email as malicious and add it to your allowlist.

Alert policies
Under Email & collaboration → Policies & rules → Alert policy, you can find a list of built-in email security-related policies. If any inbound or outbound emails match what these security policies control, an alert is generated in Microsoft Defender for the security team to analyze.
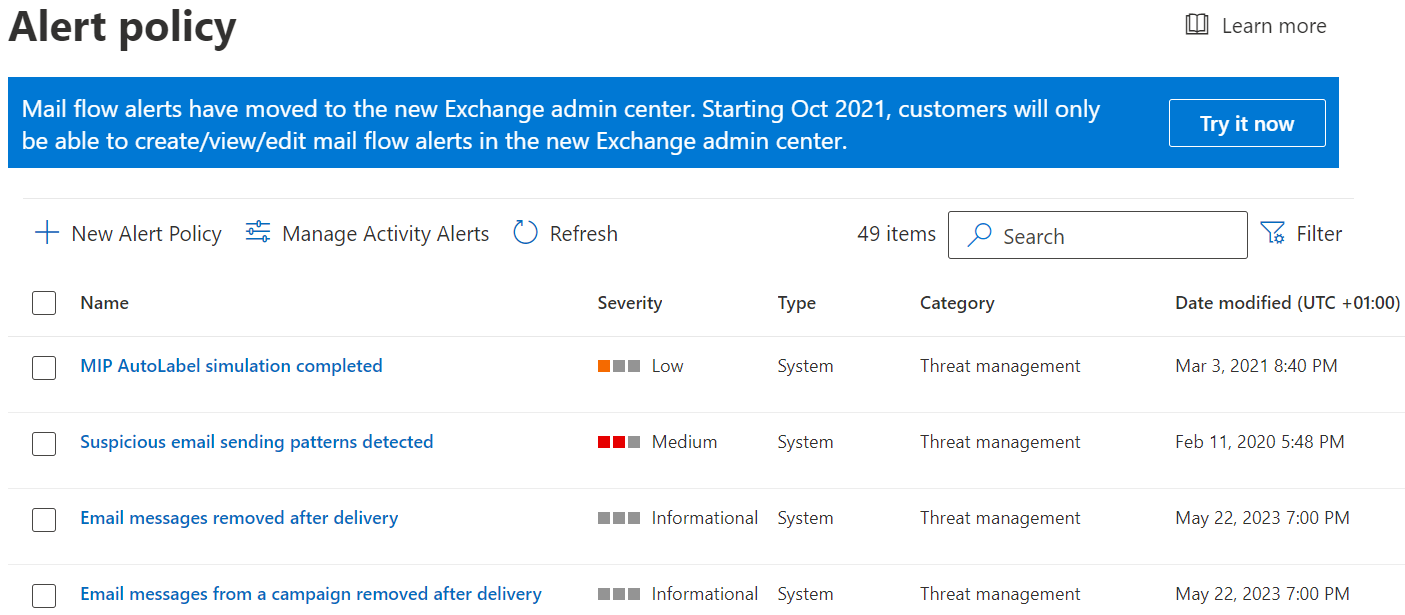
MDO alert policies
As you can see from the screenshot above, there are many built-in email security policies (currently 49) that would trigger email-related alerts, including:
- Email messages removed after delivery: This happens when MDO originally allows a malicious email (i.e., false negative) but later recognizes its mistake and deletes it from the mailbox of the recipient.
- Suspicious email sending patterns detected: While we only expect phishing to come from outside the company, employee mailboxes can get compromised (a.k.a. Account Takeover) and be used by attackers to launch phishing campaigns to other employees, clients, or business partners, exploiting the trust they put in an email coming from your company.
- A user clicked through a potentially malicious URL: This is one of the most common alerts in Microsoft Defender. This policy will trigger an alert if MDO sees that a URL with a poor reputation was clicked in an email in Outlook and the browser was opened. This helps the security team identify potential phishing victims.
Note that these built-in policies can also be modified to your needs. However, it is advisable to create new policies and test them thoroughly before activating them in your production environment since each new policy can potentially be a recipe for disaster and might block or drop normal business emails.
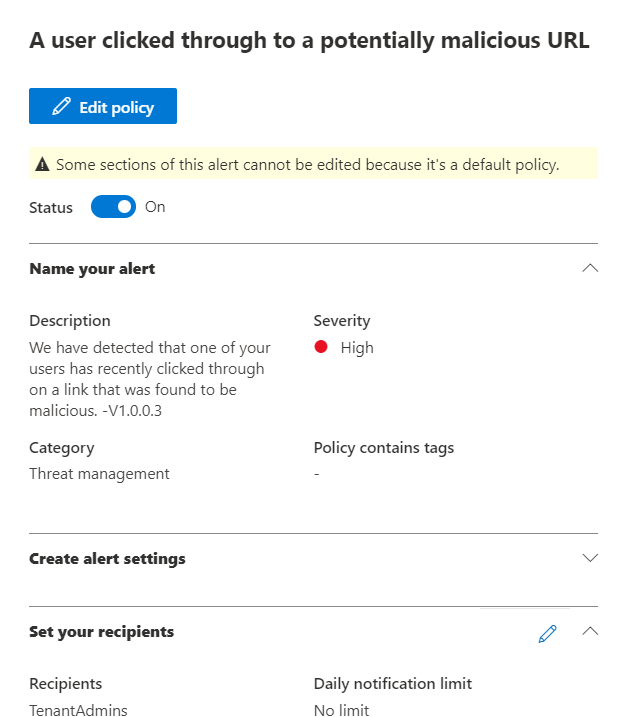
MDO: Viewing and modifying an alert policy
Report phishing button
Microsoft has added a reporting button in Outlook for phishing emails. Clicking this button deletes the email and triggers an “Email reported by user as malware or phishing” alert. However, this feature lacks the option for employees/reporters to categorize the email (e.g., spam, phishing, malware, or advertisement), leading to an increased workload for security teams who must treat all reported emails as potentially malicious and analyze them uniformly. IRONSCALES offers an alternative to the standard Outlook phishing report button. This integrated feature in Outlook allows users to specify their reason for reporting an email, with a customizable dropdown menu for different categories like spam, phishing, or malware. Additionally, it includes an open dialog box for reporters to add further context, enhancing the precision of the reporting process and aiding the security team's analysis.
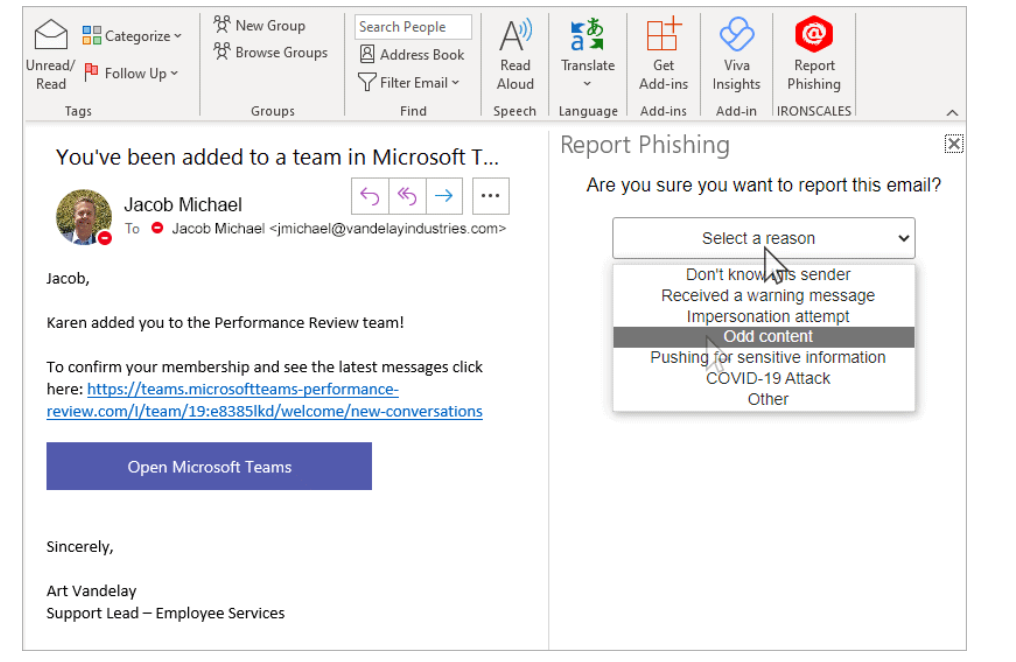
IRONSCALES phishing button for the Outlook email client. (Source)
Email quarantine
If the Microsoft anti-phishing mechanisms recognize an email as malicious, the email will be quarantined and will not reach the recipient’s mailbox. The recipient might then request that the email be released, which creates an informational alert in Microsoft Defender for the security team to act.
Your company can configure the quarantine policy under Email & collaboration → Policies & rules → Threat policies → Quarantine policy. This includes the notification email (and text) that is sent to the recipient to notify them that an email that was sent to them was quarantined.
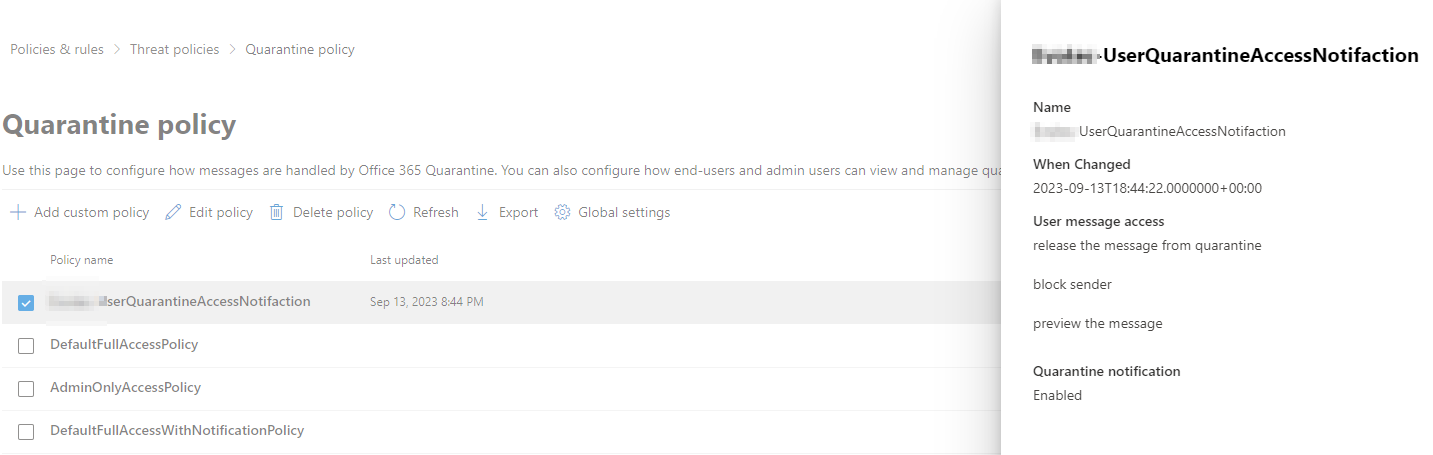
MDO: viewing and/or configuring the quarantine policy
Additionally, the email administrator can specify who is allowed to release such emails from the quarantine. For example, the default policy allows not only the security administrator but also recipients to release certain quarantine emails addressed to them without waiting for the security team to analyze the email. Fortunately, this doesn’t happen for all quarantined emails, but rather only for emails blocked with a confidence lower than “High.” Nevertheless, letting improperly trained users decide whether an email was indeed malicious or not might lead to dire consequences, and your company should consider adjusting this policy to only allow the security team to make such decisions after properly investigating the quarantined email.
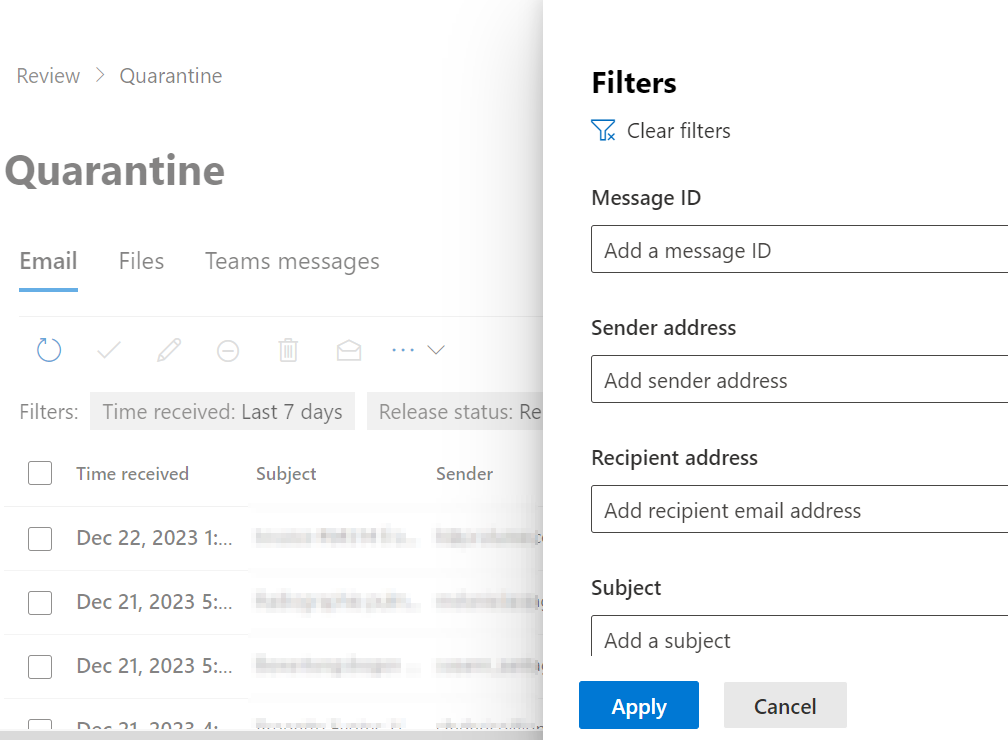
MDO: quarantine emails and filtering
You can see an overview of all the emails in the quarantine using another function of the tool, under Email & collaboration → Review → Quarantine, where you can filter based on different criteria, analyze the emails, and decide whether to release the emails or deny release requests. It is important to note that, by default, quarantined emails can be downloaded and/or fully viewed. In addition to the email’s header and metadata, a security analyst can view the content of the email, which makes it easier to understand its purpose.
Anti-phishing policies
MDO provides many email security policies to enable a company to handle phishing, spam, or malware emails as well as their malicious content (e.g., phishing URLs or attachments) under Email & collaboration → Policies & rules → Threat policies:
- Anti-phishing: Protect users from phishing attacks and configure safety tips on suspicious messages
- Anti-spam: Protect your organization’s email from spam, including specifying what action to take when spam is detected
- Anti-malware: Protect your organization’s email from malware, including dictating what action to take when malware is detected
- Safe Attachments: Protect your organization from malicious content in email attachments in Sharepoint, OneDrive, Teams, and Outlook
- Safe Links: Protect your users from opening and sharing malicious links in email messages and Office apps
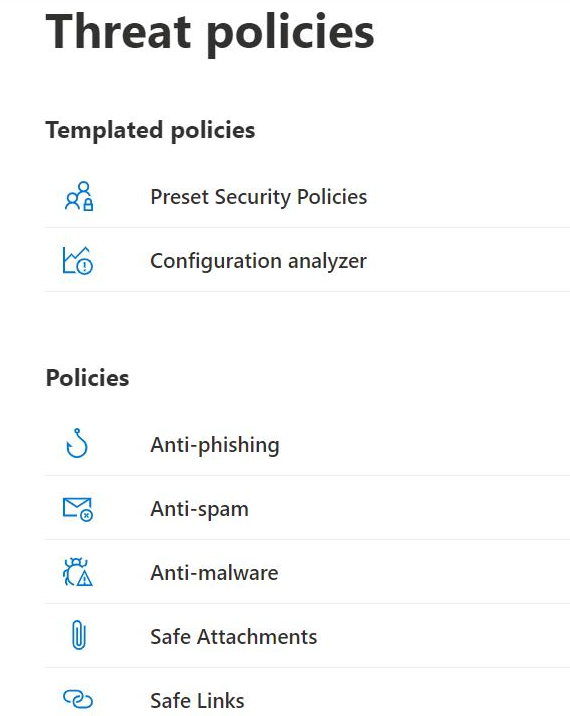
MDO: an overview of the various anti-phishing policies
Due to the number of features and configuration possibilities, we cover these policies in detail in a separate article.
Zero-hour auto purge (ZAP)
ZAP is an interesting automated capability that Microsoft Defender offers for malicious emails. It works like this:
- An email is sent to your company. MDO and its email security policies consider the email benign and allow it to reach the recipient’s mailbox.
- For some reasons—e.g., many of the same emails were delivered to other recipients of the company or recent threat intelligence (TI) updates, the sender domain reputation deteriorated quickly, or the URL’s content changed to something malicious—MDO recognizes this shift in the email’s reputation (be it the sender, its URL/attachment, or both) and removes the email from the recipient’s mailbox.
- Based on several factors, MDO decides how to handle the email, e.g., to move it to the junk folder, completely delete it from all employee mailboxes that received it, or quarantine the email.
Microsoft wrote a detailed article about how ZAP automation operates, how it handles certain emails, and how administrators can configure or handle ZAP operations.
Real-time threat intelligence (TI)
Many of the email security features that MDO provides rely on TI to evaluate the nature of an email (sender, sender domain, URL, attachments, etc.) before deciding how to handle it. Without a doubt, Microsoft has a vast amount of TI because its products operate throughout the world and are constantly targeted by threat actors. While this greatly empowers Microsoft’s email security products, Microsoft is not transparent about the source of its TI or what exactly powers MDO to correctly recognize phishing or its latest trends.
Other providers, such as IRONSCALES, harness real-time TI based on input from thousands of security experts and companies throughout the world, revealing the source of the TI and ensuring the client that its product is keeping track of the latest phishing trends.
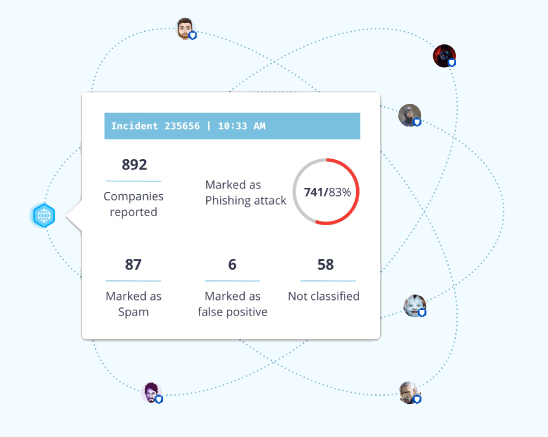
IronScales: crowdsourced TI (source)

Conclusion
In this article, we looked into MDO and its main email security features that aim to protect Office 365 users from phishing attacks, which are often complex and not easy to find or understand. By explaining the seven crucial email security features in MDO, we shed light on this powerful security tool, its strengths and weaknesses, and how to make use of its features.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










