Anti-Phishing Policies In Microsoft 365
The phishing problem has been around for a long time, and it isn’t going to go away anytime soon. Phishing attacks are getting exponentially more sophisticated and getting better at delivering ransomware, causing companies significant damage.
Fortunately, the cybersecurity industry is also changing, constantly researching new ways to combat ever-evolving cybersecurity risks, including phishing. One of the most popular products that many companies are implementing is Microsoft Defender, an endpoint detection and response (EDR) product that aims to be an “all-in-one” tool.
Formerly known as Advanced Threat Protection (ATP), Microsoft Defender has come a long way since its early days. It is now a central place for handling security threats in the M365 environment, with tools such as Microsoft Defender AV, Microsoft Defender for Endpoint (MDE), Microsoft Defender for Identity (MDI), Microsoft Defender for Office (MDO), etc., all under one umbrella.
While having all these tools in one product has many obvious benefits, it has a major drawback: It is often hard to find a specific policy that might be hidden deep in the platform. Additionally, Microsoft constantly evolves Microsoft Defender UI, often changing the location or the interface of its many functionalities. In this article, we will shed some light on anti-phishing policies in Microsoft Defender, including their roles, locations, and configuration possibilities.
Summary of anti-phishing policies in M365
The table below lists six different anti-phishing policies and features that can be found and configured in Microsoft Defender.
| Anti-phishing feature |
Description |
|
Anti-phishing policy
|
This policy allows you to configure or instruct Microsoft Defender when, on top of its usual checks, to consider an email malicious. This can be the check for unusual characters or whether DMARC is honored or not, to only mention a few.
|
| Anti-spam policy |
In this policy, you can specify whether an inbound or outbound email should be categorized as spam based on certain thresholds. |
| Anti-malware policy |
Configure what kinds of attachments are explicitly blocked or allowed. |
| Safe links |
Scan email links in real time before allowing them to reach the mailbox. |
| Safe attachments |
Scan email attachments in real time before allowing them to reach the mailbox. |
| Phishing simulation and security awareness training (SAT) |
Improve phishing protection by conducting phishing simulations and complementing them with SAT. |
In this article, we will explore in detail the six anti-phishing features in M365 that can help your company increase its phishing defense and configure how to handle malicious emails. Five of these features can be found at the same place, under Email & collaboration → Policies & rules:
Microsoft Defender: anti-phishing policies

Anti-phishing policy
“The” anti-phishing policy, as the name states, is one of the main anti-phishing security mechanisms in Microsoft Defender. It provides many configuration possibilities to control how emails are handled, and what exactly should be considered or labeled as phishing based on the company’s risk appetite:
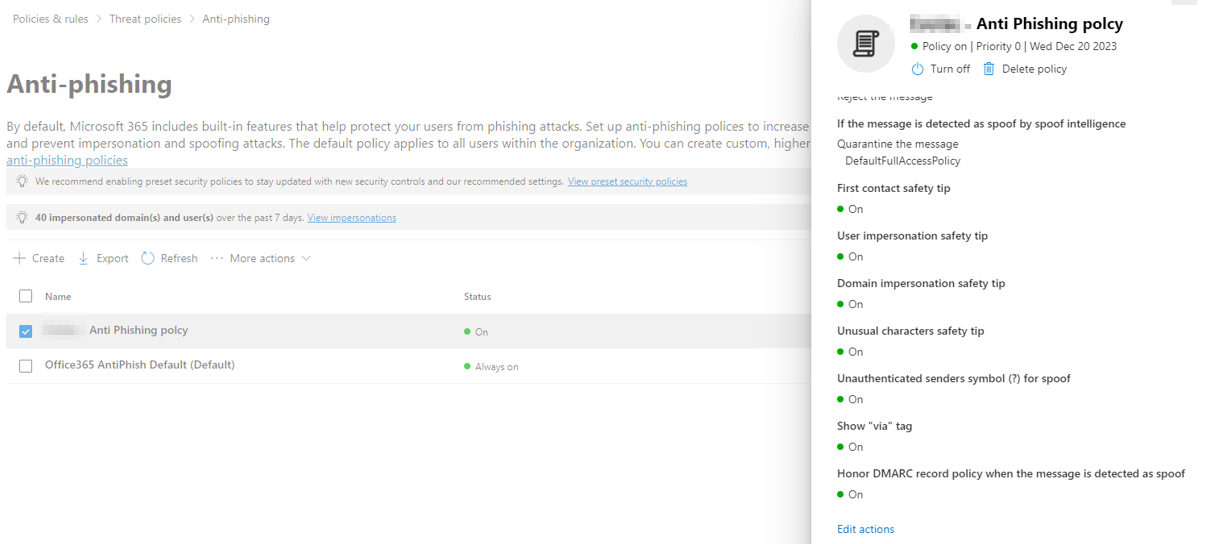
Microsoft Defender: anti-phishing policy
Let’s look at each of these elements:
- First contact safety tip: If the recipient is receiving an email for the first time from this sender, Microsoft will add a banner at the top of the email to notify the recipient so they can exercise extra caution with emails from unknown senders.
- User impersonation safety tip: If the sender was faked, Microsoft Defender will add the following text to the email to warn the recipient: “This sender appears similar to someone who previously sent you an email but may not be that person.”
- Domain impersonation safety tip: If the domain was faked, Microsoft Defender will add the following text to the email to warn the recipient: “This sender might be impersonating a domain that’s associated with your organization.”
- Unusual character safety tip: If the sender’s email address contains special, unusual characters (e.g., math symbols), Microsoft Defender will add the following text to the email to warn the recipient: “The email address <email address> includes unexpected letters or numbers. We recommend you don’t interact with this message.”
- Unauthenticated senders symbol (?) for spoof: Adds a question mark to the sender’s photo in the “From” box if the message doesn’t pass SPF or DKIM checks and the message doesn’t pass DMARC.
- Show “via” tag: Activating this protection mechanism causes Microsoft Defender to add the “via” tag (test@test.com via attacker.com) in the “From” box if the domain in the “From” address is different from the domain in the DKIM signature or the “MAIL FROM” address found in the email headers.
- Honor DMARC record policy when the message is detected as spoof: If the sender was spoofed, the company could decide to honor the DMARC policy of the domain being spoofed, i.e., to quarantine or reject the email:

Microsoft Defender: Honor DMARC feature configuration (source)
Anti-spam policy
The anti-spam policy is one of the most complex policies in Microsoft Defender and is divided into three sub-policies.
Connection filter policy
Given the sophistication of modern emails and robust phishing defenses, it's possible for some safe emails to be mistakenly identified as spam or blocked. If such emails come from specific email servers, you can use this policy to establish a whitelist of IP addresses of sending email servers to stop emails from these IPs from being blocked. Additionally, this policy gives you the ability to block the IPs of malicious servers that are known to send phishing campaigns or to be abused by hackers:
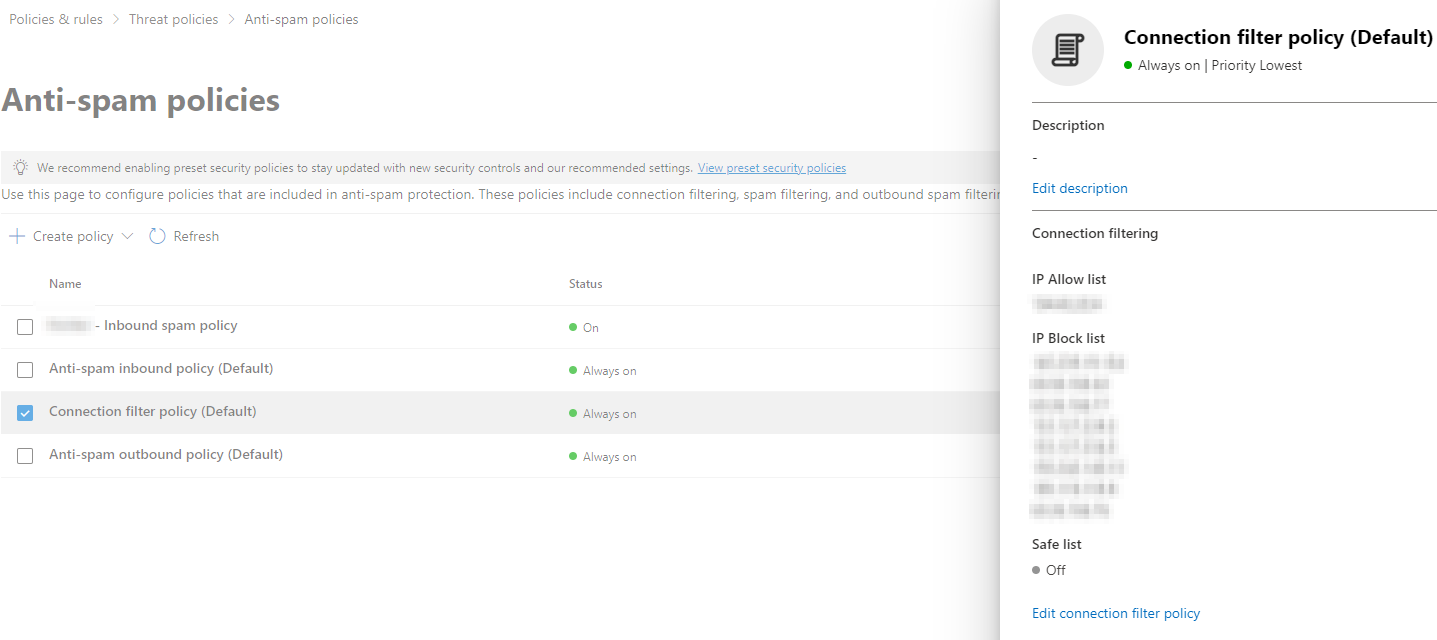
Microsoft Defender: connection filter policy
Anti-spam inbound policy
Use this policy to configure what constitutes a spam email based on the number of emails from the same sender (default: 5 emails) or other email elements:
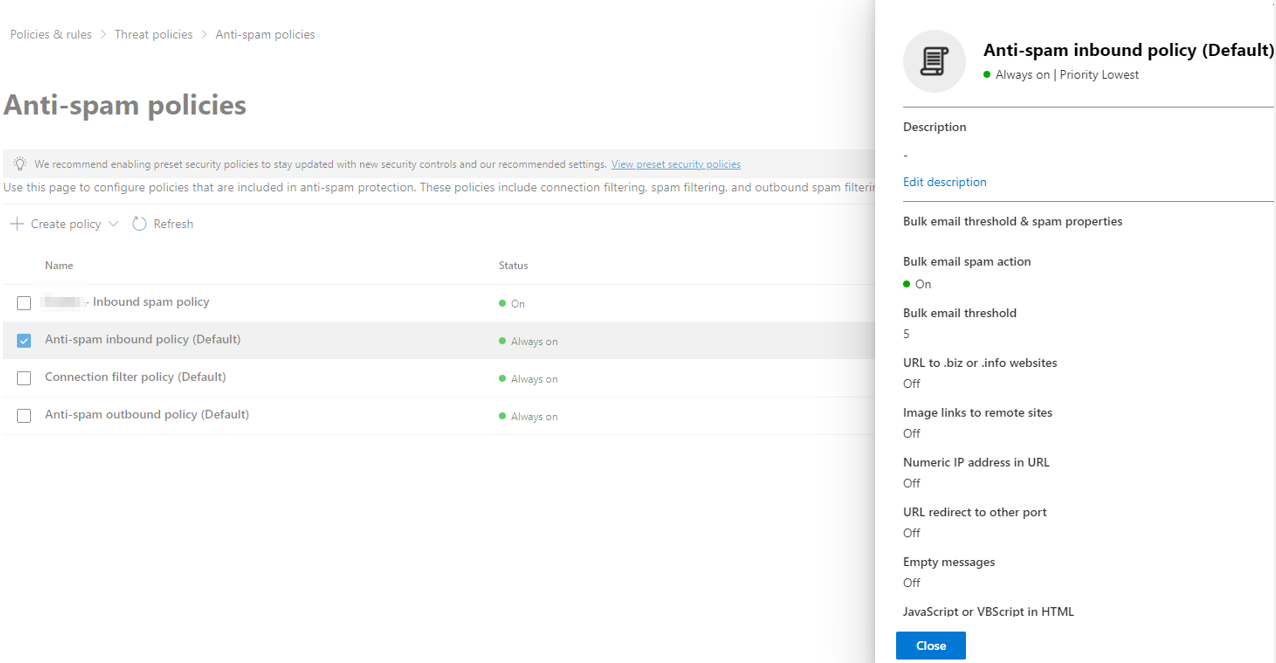
Microsoft Defender: anti-spam inbound policy
Anti-spam outbound policy
While we usually expect spam campaigns to originate from bad actors outside the company (domain), but companies can unknowingly or accidentally send spam or spam-like campaigns themselves. This might happen with marketing activities such as the distribution of a newsletter or by sending a large amount of emails in a short period of time (e.g., in an hour). This is important since it might affect the company’s domain reputation, leading to other normal business emails being dropped or blocked due to poor domain reputation.

Microsoft Defender: anti-spam outbound policy
Anti-malware policy
Phishing emails with attachments are the second most common type of phishing email after URL phishing. That is why Microsoft Defender has a dedicated anti-phishing policy to protect against emails with malicious attachments:
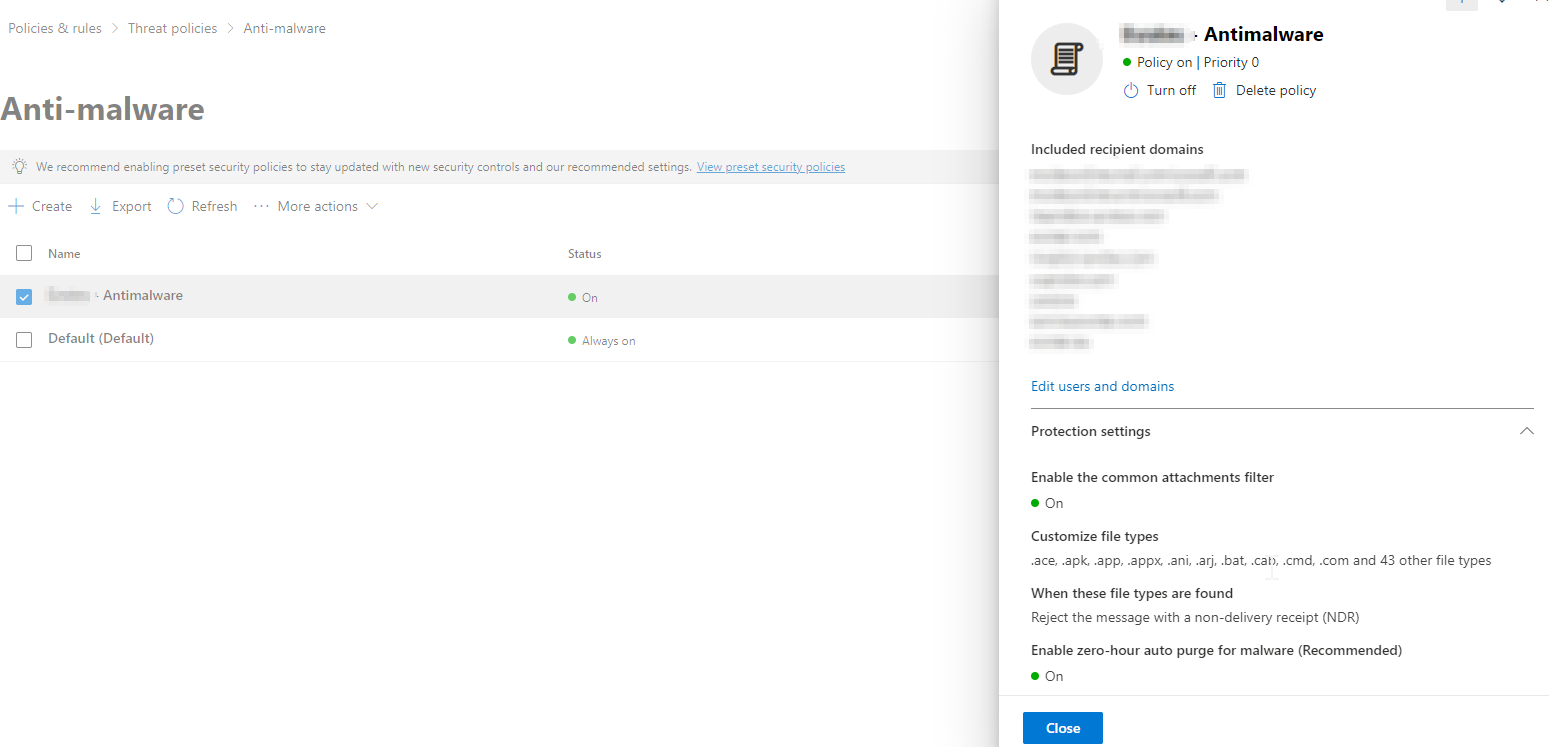
Microsoft Defender: anti-malware policy
If the default built-in policy provided by Microsoft is not enough, you can create a custom policy and configure the following elements:
- Included recipient domains: List all domains in use by your company within the same Office 365 tenant.
- Customize file types: Add high-risk file extensions, such as .cmd, .bat, .ps1, etc., to instruct Microsoft Defender and MDO to reject emails containing attachments with these file extensions.
- When these file types are found: Choose how you want MDO to handle high-risk file extensions (defined above). For example, you can decide to reject emails with this kind of attachment.
- Enable zero-hour auto purge (ZAP) for malware: If MDO initially misses a malicious attachment and delivers the email but subsequently updates its analysis to classify the attachment as harmful, ZAP ensures that all emails with such attachments are automatically deleted or quarantined.

Safe links
Phishing emails often use malicious URLs, and Microsoft addresses this with the “Safe Links” feature. This policy, once enabled, rewrites URLs in emails to include the original URL as a parameter in a new link. When a recipient clicks on this link, Microsoft performs real-time analysis, using Microsoft SmartScreen and threat intelligence resources, to evaluate the URL's safety at the time of the click. This process recognizes that URLs and domains can change in reputation over time. Additionally, this mechanism allows Microsoft to track URL clicks in emails and generate alerts for suspicious links.
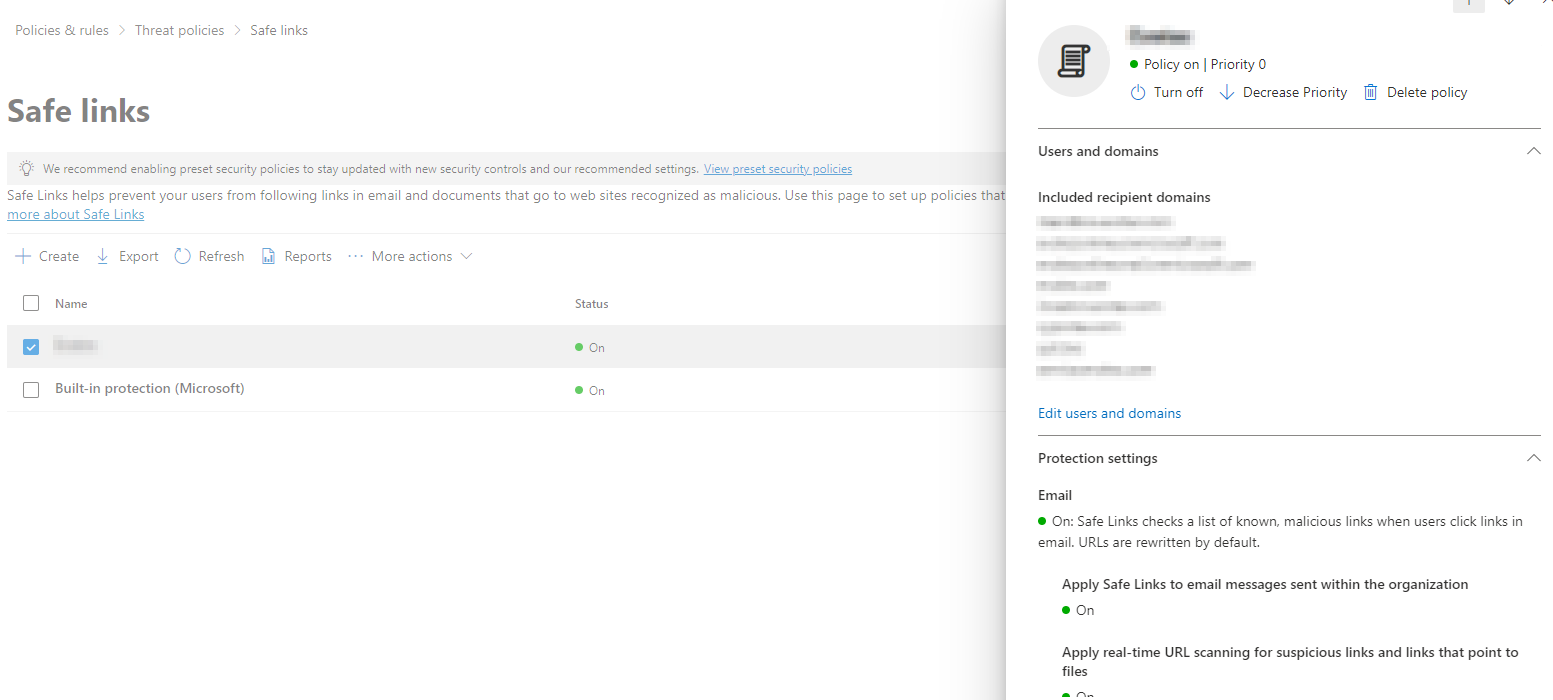
Microsoft Defender: safe links policy
As can be seen in the screenshot above, you can use the built-in policy provided by Microsoft or create your own policy and configure it based on your needs:
- Included recipient domains: List all domains in use by your company within the same Office 365 tenant.
- Apply Safe Links to email messages sent within the organization: Allows you to apply this policy for internal emails. This adds a layer of protection in the event of an employee account takeover where their email accounts can be used to send further phishing emails internally.
- Apply real-time URL scanning for suspicious links and links that point to files: Decide whether, as explained above, your company would like to scan URLs not only when the email is received but also when the URL is clicked by the recipient.
Safe attachments
Safe Attachments is a feature/policy in Microsoft Defender; it scans attachments in Sharepoint, Outlook, OneDrive, Teams, and more before they reach the recipient. When activated, recipients initially get the email with the attachment stripped and replaced with a notice of ongoing scanning. Microsoft Defender assesses the attachment in a separate virtual environment. If deemed safe, the original email is re-sent with the attachment included.
Conversely, if an attachment is flagged as risky or not compliant with your company’s attachment policies, Microsoft Defender attaches a TXT file to the email, detailing the original attachment's name and size, noting its removal for security reasons. This mode of operation is called "dynamic delivery," and its process minimizes email delivery delays while ensuring thorough scanning.
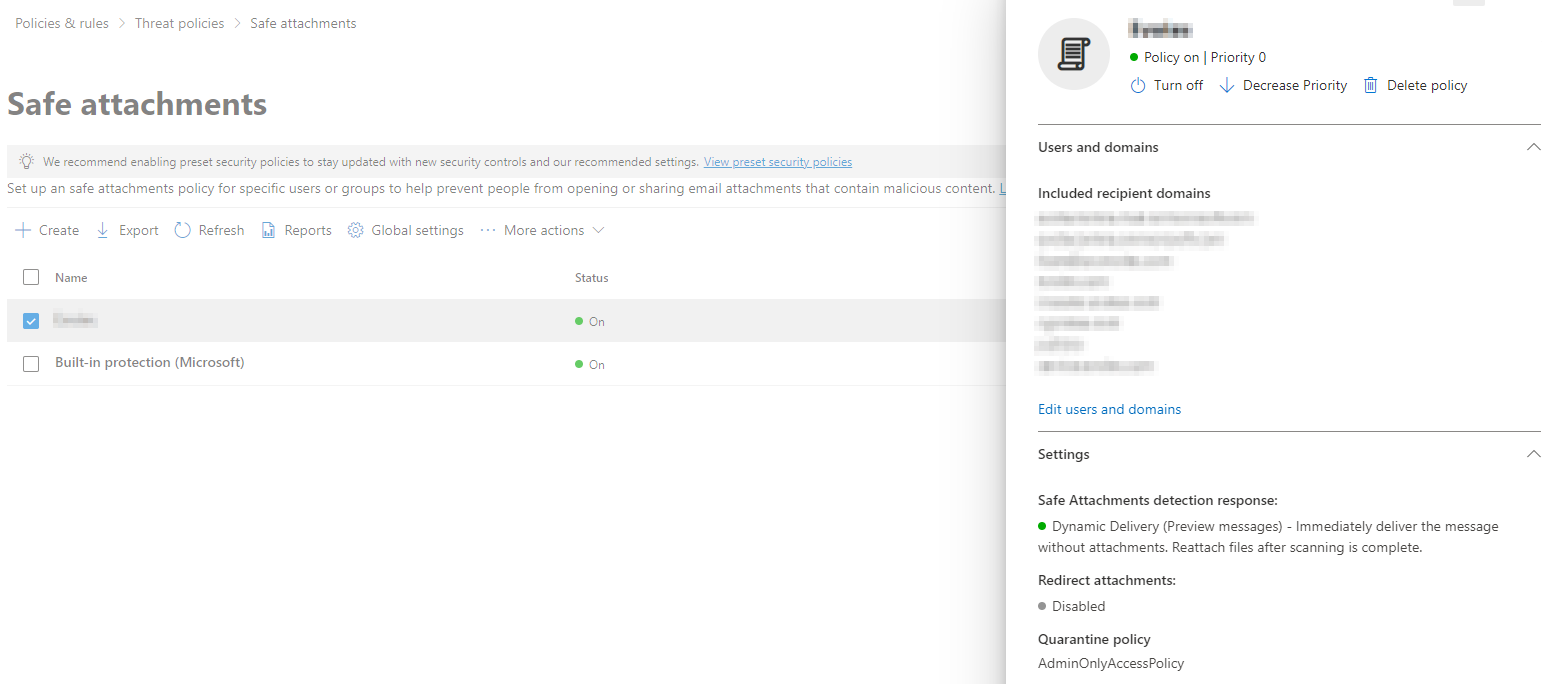
Microsoft Defender: safe attachments email policy
It is also important to note that Microsoft also provides a default policy for safe attachments that will be operational if you activate it (no configuration needed). If the built-in protection is not what you are looking for, you can create a policy by clicking on the “Create” button and configure it to fit your needs. The main items to configure are:
- Included recipient domains: List all domains in use by your company within the same Office 365 tenant.
- Safe Attachment detection response: Here, you can specify if you would like to use dynamic delivery (as explained above), disable the attachment scan, or only monitor attachments (scan and report malicious emails but don’t block them).
Phishing simulation and security awareness training (SAT)
Phishing simulation and SAT, while not direct anti-phishing policies, play a crucial role in mitigating phishing risks. They educate employees about phishing tactics and test their knowledge through simulations. Microsoft Defender offers these capabilities under "Email & collaboration → Attack simulation training," with several tabs for different functions:
Microsoft Defender: Phishing Simulation and SAT
Each of the tabs has a different purpose:
- Overview: Provides instructions and videos on how to get started and how to organize a phishing simulation or training.
- Simulations: This lets you create and configure new simulations or check the status of already created simulations.
- Training: This lets you create a training campaign to train employees on topics such as cybersecurity, social engineering, compliance, etc.
- Reports: Shows statistics from the phishing simulations, including “repeat offenders” (i.e., those that repeatedly fall victim to phishing), users who didn’t complete the training, etc. Unfortunately, there is no place for customization or generating custom reports, as might be done with other solutions.
- Automation: In this tab, you can configure automated campaigns where you can specify the payload, simulation schedule, assign training, etc., and Microsoft Defender will periodically conduct the phishing simulations automatically.
- Content library: Make use of built-in phishing templates, payloads, and training modules that Microsoft Defender already contains and are ready to be used. While Microsoft Defender contains a rich library with training modules, it is generic in nature. Therefore, consider enhancing this library with up-to-date training tailored to your company that IronScale provides.
- Settings: Configure thresholds for how often training modules should be assigned to users (default: 90 days) or how many times a user needs to fail the phishing simulation to be considered a “repeat offender” (default: twice).
Due to the number of features and configuration possibilities, we will cover each of these tabs in a separate article.

Conclusion
Navigating the extensive and intricate Microsoft 365 suite can be challenging. This article has detailed six key anti-phishing features within Microsoft Defender, outlining their roles and configuration processes. While these tools can enhance your company's security, it's vital to configure them carefully and monitor them regularly to prevent potential disruptions in email delivery and business operations.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










