M365 Phishing Simulation
In 2021, a staggering 1 billion emails were compromised, impacting one in five internet users, and last year saw a 47.2% jump in phishing attacks. This data reveals an alarming trend: These threats are growing not only in volume but also in sophistication—outsmarting even the most robust defense techniques—like multi-factor authentication.
To combat this, Microsoft 365 Defender for Endpoint features an attack simulation tool that uses Microsoft’s attack scenarios database to help security teams identify [human] vulnerabilities and improve their defenses against prevalent cyber threats. Although it is a powerful tool for phishing simulations, it has many features that can be quite complex and confusing when you use it for the first time.
That is why, in this article, we analyze M365’s phishing simulation in detail. We’ll start by examining the tool’s capabilities and then look at how to integrate additional strategies for a more robust defense against advanced email threats. Our goal is to provide insights for a comprehensive cybersecurity defense strategy by improving email security tooling.
Summary of core M365 phishing simulation concepts
| Concept |
Description |
|
M365 phishing simulation overview
|
The fundamentals of using M365 phishing simulation include how to access simulations, selecting a social engineering technique, naming the simulation, selecting the payload and login page, targeting users, assigning training, selecting a landing page, configuring end-user notifications, and launching the simulation.
|
| Walkthrough of M365 phishing attack simulation features |
We look at attack simulations, like automation for simulations and payloads, phishing messages in Teams, insights, reporting, and customizing payloads. |
| Enhancing M365 phishing simulations with advanced features |
Advanced features include autonomous simulations, reporting and analytics, and security awareness training. |
| Best practices in phishing simulation with M365 |
Expert practices include effective planning, simulation design, payload customization, target selection, simulation timing, automation, realistic elements, analysis and adaptation, training integration, iterative improvement, and handling regulatory compliance. |
M365 phishing simulation overview
Microsoft Defender for Endpoint (MDE) offers a useful tool for conducting phishing simulations, which is crucial for testing organizational defenses against cyber threats. For interested IT/Security administrators, understanding the practical steps and nuances of setting up and running a simulation is a fundamental element of an organization’s security strategy.
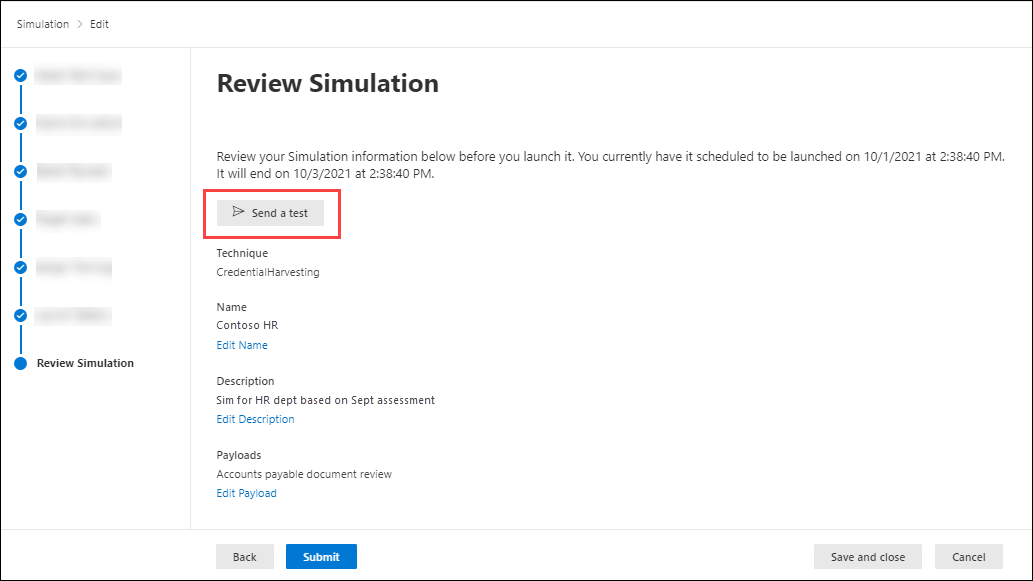
Reviewing a completed simulation (source)
To demonstrate this, we’ll break down the fundamentals of using M365 phishing simulation into the following nine steps.
- Access the simulations: Go to the Microsoft Defender portal, navigate to Email & collaboration, and select Attack simulation training. Choose Launch a simulation on the Simulations tab to start the wizard (as seen in the figure above).
- Select a social engineering technique: Select from various social engineering techniques (curated from the MITRE ATT&CK® framework) to simulate real-world phishing attacks, like the following:
- Credential Harvest: For deceptive websites attempting credential theft
- Malware Attachment: Malicious code in attachments
- Link in Attachment and Link to Malware: Arbitrary code execution via links
- Drive-by URL: Silent code run/installation from websites
- OAuth Consent Grant: Permission requests by a malicious Azure App.
- Name and describe the simulation: Provide a unique name and optional description for the simulation.
- Select the payload and login page: You can select or create a payload (discussed in the next section) with options to view or modify the associated login page, particularly for Credential Harvest or Link in Attachment techniques. The platform offers extensive filtering capabilities to choose payloads based on criteria like complexity, language, theme, brand, and industry. This comprehensive process allows for tailored phishing scenarios based on your needs.
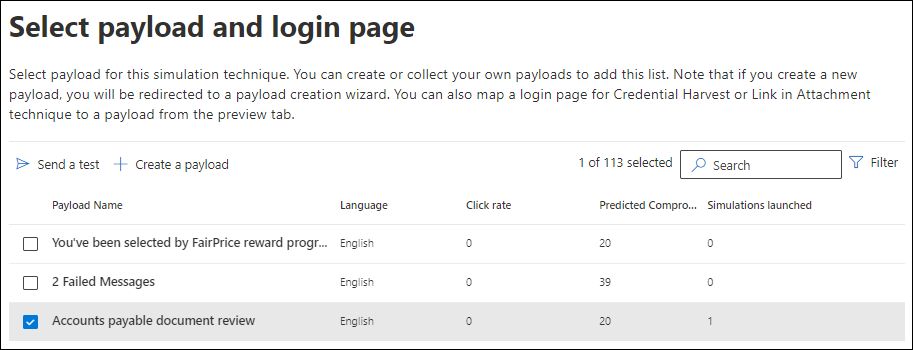
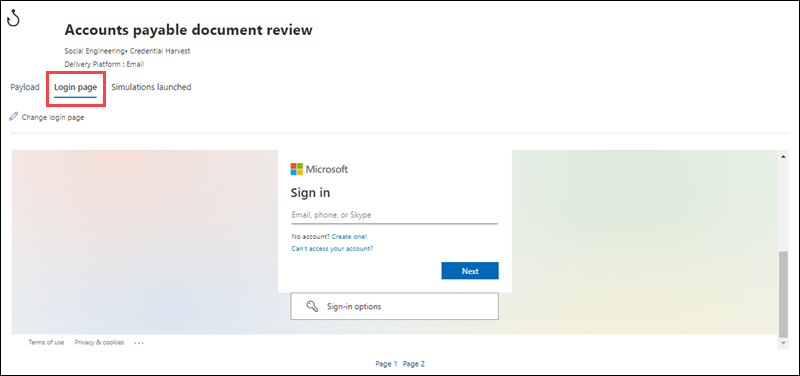
Selecting a payload and login page (source)
- Target users: Target selection is flexible, allowing for the inclusion or exclusion of specific user groups, ensuring that the simulation accurately reflects the organization’s structure and risk profile.
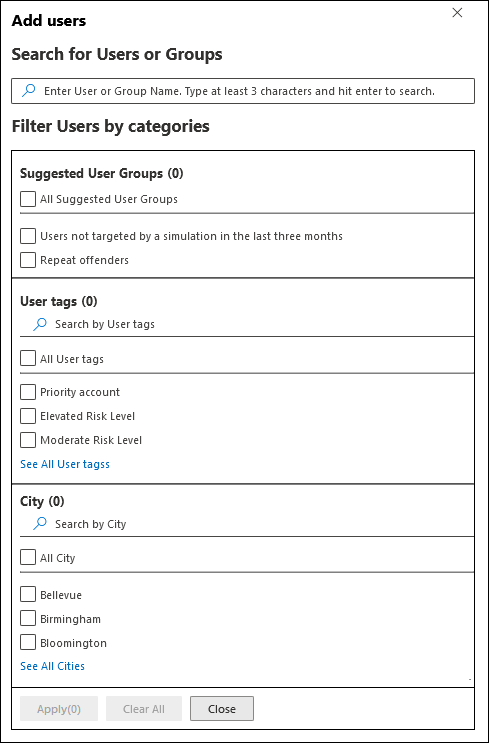
Adding users to the simulation (source)
- Assign training: A standout feature is the integration of training modules within the simulation. Targeted educational content is offered after the interaction, turning a potential security breach into a learning opportunity. Microsoft also allows assigning custom training via user-defined URLs.
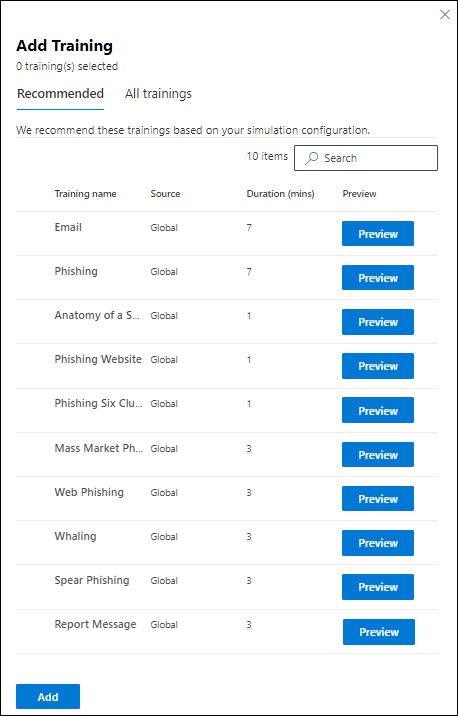
Assigning post-simulation training (source)
- Select the landing page: Choose from a library of landing pages or use a custom URL as the theme of the phishing site.
- Configure end-user notifications: Decide on the type of notifications for users participating in the simulation.
- Launch the simulation: Configure the details of the simulation’s launch to customize it for immediate or scheduled delivery.
A benefit of M365’s phishing simulation lies in its integration with the broader Microsoft ecosystem, supporting interaction with existing organizational email structures. Its ability to simulate a variety of attacks—from basic deceptive emails to spear-phishing attacks—makes it a versatile tool for security training.

Walkthrough of M365 phishing attack simulation features
The M365 phishing attack simulation tool can be complex to set up and maintain. In this section, we’ll dive into the features that fuel its capabilities and how to use them.
Payloads and customization
“Payloads” in M365 phishing attack simulation are essentially links or attachments in phishing emails and are crucial for simulating real-world phishing threats. Their tool allows administrators to choose from a list of predefined (global) payloads or the ability to create custom (tenant) payloads. Global payloads cover a broad set of phishing techniques, while custom payloads can be tailored to specific organizational threats.
You can follow these steps to create a custom payload:
- Access the payload options: Using the Microsoft Defender portal, navigate to Email & Collaboration > Attack simulation training > Content library tab > Payloads.
- Choose payload types and techniques: Select from types like Credential Harvest, Malware Attachment, and others (see the bullet list above). Each type offers unique customization options.
- Customize the sender details: Set sender names and emails, including internal addresses, to simulate insider threats.
- Design the email content: Craft realistic content for phishing emails, paying attention to subject lines, body content, and attachments.
- Create a login page for supported payloads: For certain social engineering techniques, such as Credential Harvest and Link in Attachment, the simulation includes selecting a fake login page. This login page is critical for capturing how users interact with phishing attempts and can either be picked from one of the global login pages—Github, Linkedin, Microsoft, and non-branded external sites—or the tenant login pages, which can be modifiable clones of the global or custom pages created with the wizard.
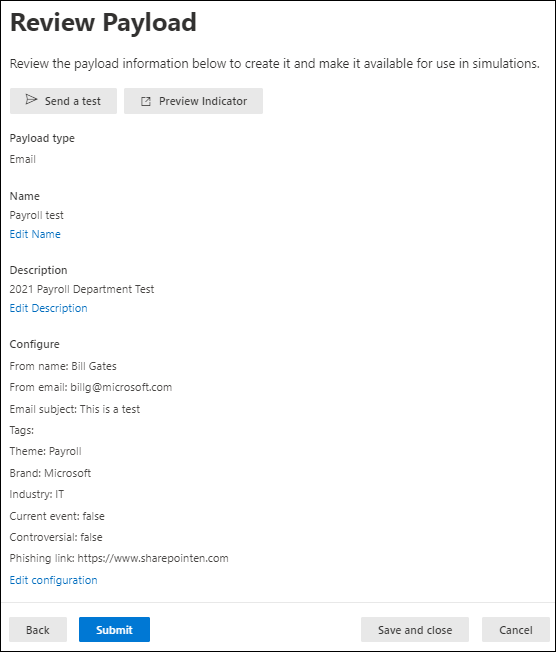
Reviewing a completed custom payload (source)
Automating payloads for phishing defense training
Payload automation in the M365 phishing attack simulation tool provides the ability to replicate real-world phishing attacks. By monitoring received emails for indicators of phishing—also called payload harvesting—organizations can mimic real attacks and simulate phishing scenarios that mirror actual threats, enhancing the effectiveness of defense training.
Note that in M365’s phishing attack simulation, simulations refer to the mock phishing scenarios used for training purposes, while payloads denote the actual malicious content or techniques used in these scenarios to mimic real-world cyber threats. This section focuses on automating payloads, while the next one sheds light on automating simulations.
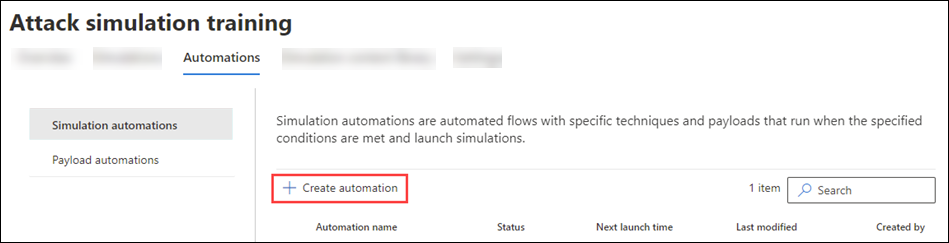
Create an automation (Source)
Follow these steps to implement payload automations:
- Create a custom simulation: In the Microsoft Defender portal, navigate to the Automations tab under Attack simulation training, where you can initiate the creation of a new payload automation. This process involves naming the automation, providing a description, and saving it as a draft if needed. The idea is to mimic real payloads based on reported phishing attacks within your organization.
- Configure run conditions: The detailed configuration of run conditions is crucial to the setup. This includes specifying the number of users targeted, identifying particular phishing techniques (like Credential Harvest or Malware Attachment), and defining sender information (domain, name, and email). You can combine multiple conditions using “AND” logic (“<Condition1> and <Condition2>”) for precise targeting, ensuring that harvesting can be triggered accurately when M365 detects a real phishing attack under the specified conditions.

Simulation automations
Simulation automations offer a way to enhance cybersecurity training by scheduling and executing multiple benign cyberattack simulations. This feature is key for organizations aiming to boost their phishing readiness over time. It is similar to individual simulations but with the additional ability to select multiple techniques and payloads.
Here’s how to effectively implement and utilize simulation automations:
- Choose scheduling options: Decide between a randomized or fixed schedule. A randomized schedule allows simulations to launch at unpredictable times within a set period, enhancing the element of surprise. For a fixed schedule, specify exact start and end dates and choose whether simulations occur weekly or monthly; the choice should align with your organization’s training calendar and workload.
- Customize the target audience: Tailor simulations to specific groups, such as “repeat offenders,” to ensure focused training for those needing it most. This is crucial for reinforcing cybersecurity awareness regularly without manual intervention.
- Decide on technique and payload variety: Incorporate diverse social engineering tactics into your simulations to prepare employees for different phishing scenarios, increasing their resilience. You can choose to use unique payloads across simulations or maintain a consistent approach, depending on your training goals.
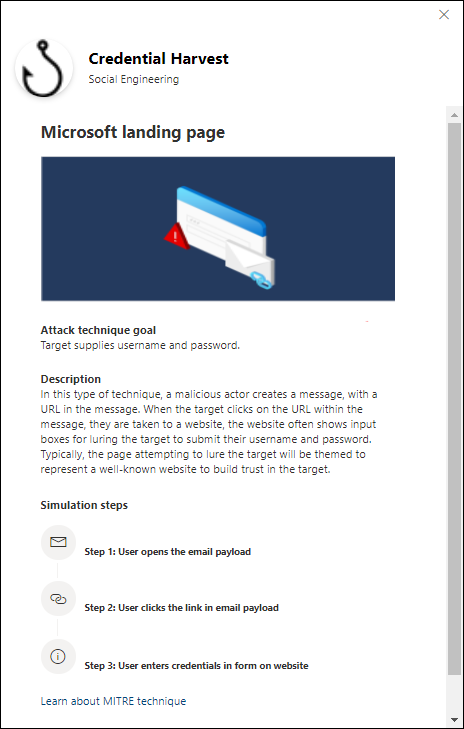
Sample simulation with the Credential Harvesting technique (source)
Additionally, consider settings like region-aware delivery to align simulations with the user’s time zone.
Insights and reports
This feature is an effective tool for evaluating the effectiveness of attack simulation training. This section dives deep into its implementation, highlighting the range of functionalities available to maximize cybersecurity training outcomes.
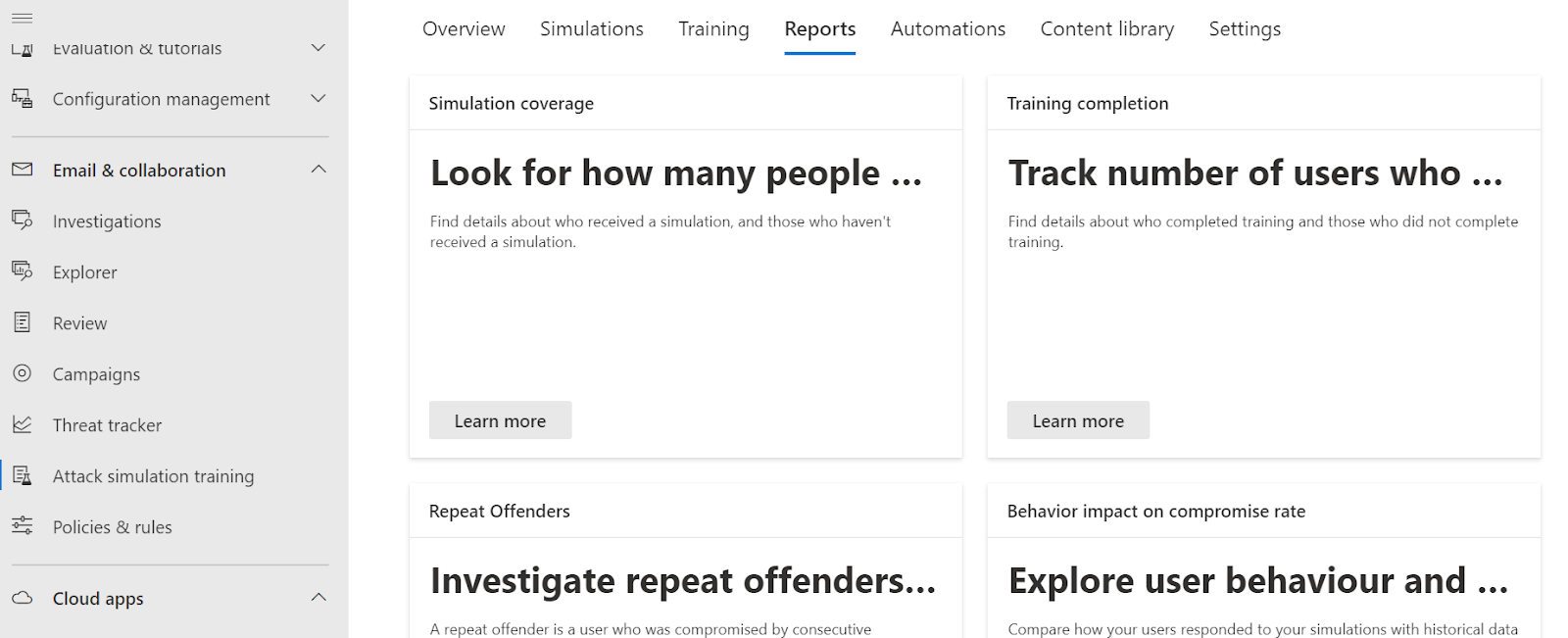
M365 Phishing attack simulation reports
Located on the attack simulation training page, the overview provides a complete look at team readiness for cyber threats.
- Key components and their functions:
- Recent simulations: Shows the last three simulations.
- Recommendations: Suggests simulations tailored to organizational needs.
- Simulation coverage: Displays user simulation status for targeted training.
- Training completion: Tracks user training status, showing progress.
- Repeat offenders: Identifies users who frequently fail simulations for focused training.
- Behavior impact: Compares predicted and actual compromise rates.
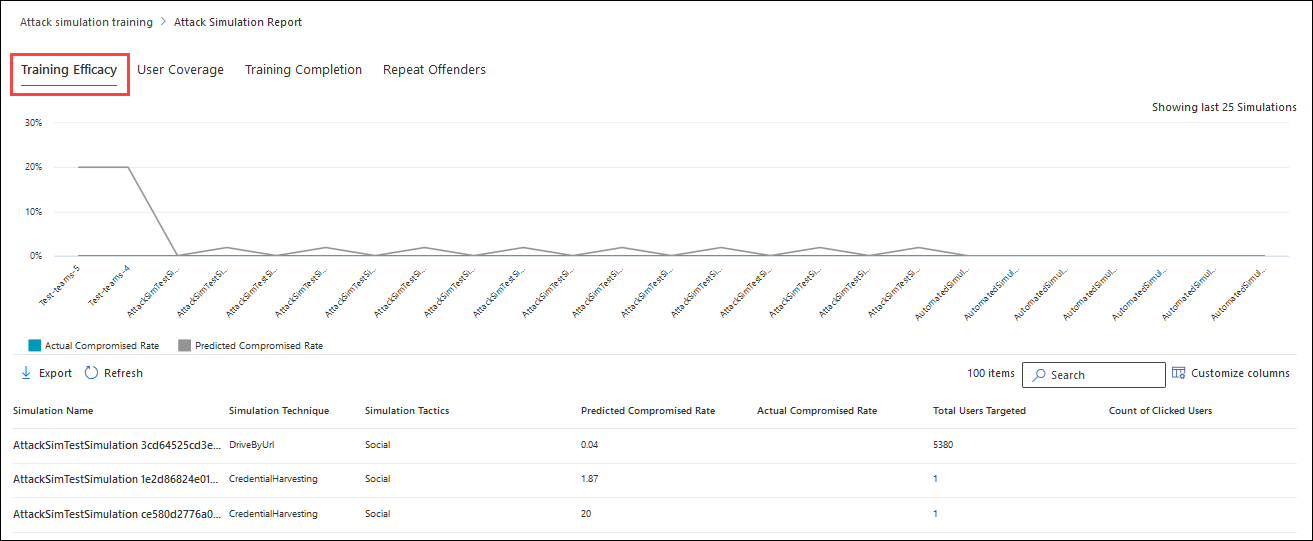
Training efficacy for the attack simulation report (source)
- Reporting:
- Attack simulation report: Details user coverage, training completion, and repeat offenders from the overview tab.
- Simulation impact: Shows responses to simulations (links, attachments).
- User activity: Monitors actions like email reporting or link clicking.
- Training completion: Displays training status and rates.
- Recommended actions: Suggest improvements based on the Microsoft Secure Score.
- Export and customization options: Most sections allow for detailed report exports and customization, including filtering options, column customization, and data export in CSV.
- Practical implementation tips: Use insights to identify vulnerabilities and customize future training. A high compromise rate indicates a need for more intense phishing email training. Regularly review repeat offenders and training completion sections to optimize effectiveness. Note that managing M365 phishing attack simulation becomes more challenging with more tenants, as cross-tenant simulations aren’t supported.
Microsoft Teams integration for simulations
The integration of Microsoft Teams for delivering simulated phishing messages in organizations with M365 phishing attack simulation training is a notable feature. It expands the training environment beyond email, reflecting the diversified communication tools used in organizations.
Enhancing M365 Phishing simulations with advanced features
While M365 provides a good starting foundation for simulating phishing attacks, integrating advanced AI-based solutions significantly enhances realism and effectiveness. One such platform is IRONSCALES, which harnesses GenAI and Large Language Models (LLM) to create personalized spear phishing attacks that mimic real-world attacks. This type of platform goes far beyond M365’s basic templates and prepares teams for sophisticated cyber-attacks.
Autonomous simulations
The IRONSCALES autonomous simulations feature provides fully automated monthly campaigns based on the latest real-world attack methods, continuously testing organizations while saving IT teams significant time compared to M365’s manually configured payload automation. IRONSCALES uses GenAI to create full simulations, allowing IT teams to set the frequency of simulations and leaving the rest to IRONSCALES.
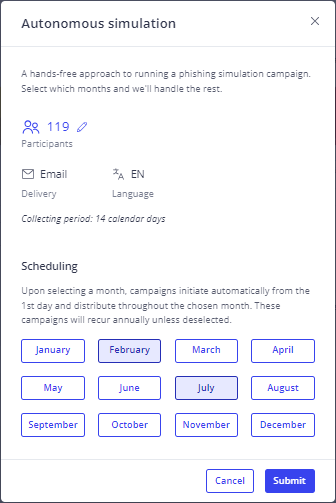
Autonomous campaign simulation in IRONSCALES
Reporting and analytics
When it comes to reporting and analysis, IRONSCALES surpasses Microsoft’s basic CSV exports by providing a comprehensive analytics dashboard, including more graphics and granular data about results than what Microsoft offers, as well as more export options. This advanced reporting feature provides deeper insights, including detailed user behavior analysis, which is crucial for understanding and improving the team’s response to phishing threats and for satisfying many compliance framework requirements.
In addition, IRONSCALES Themis CoPilot, seamlessly integrated with Outlook, serves as a real-time educational tool for users. This AI-powered “Security Guide” not only assists employees in understanding and identifying phishing emails but also educates them on the nuances of spotting such threats. This interactive feature significantly reduces the volume of reports and false positives that the IT security team needs to review. It simplifies the process for users to report genuine suspicions, empowering them with the knowledge to discern potential threats and only escalate genuine concerns, thereby streamlining the overall security process.
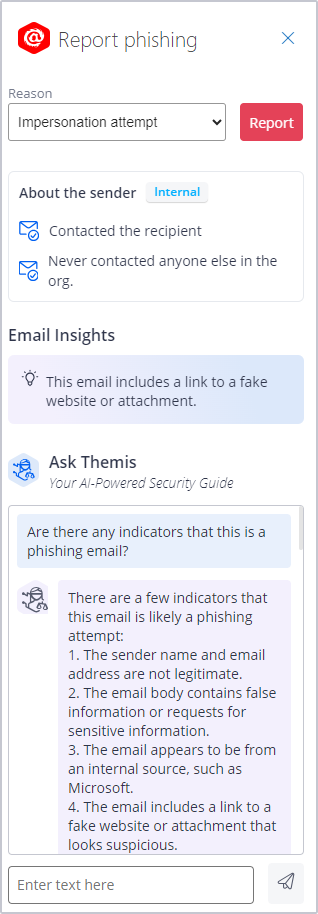
IRONSCALES Report Phishing Button with Themis CoPilot
Security awareness training
The M365 training modules are enhanced by the diverse IRONSCALES library of engaging video and interactive content, covering a broad spectrum of topics related to the latest phishing tactics and prevention strategies.
IRONSCALES stands out by providing customizable training modules that offer immediate, targeted education when an employee falls for a simulation. This data-driven approach transforms vulnerabilities into learning opportunities, facilitating tailored and ongoing training experiences rather than being a one-size-fits-all process.
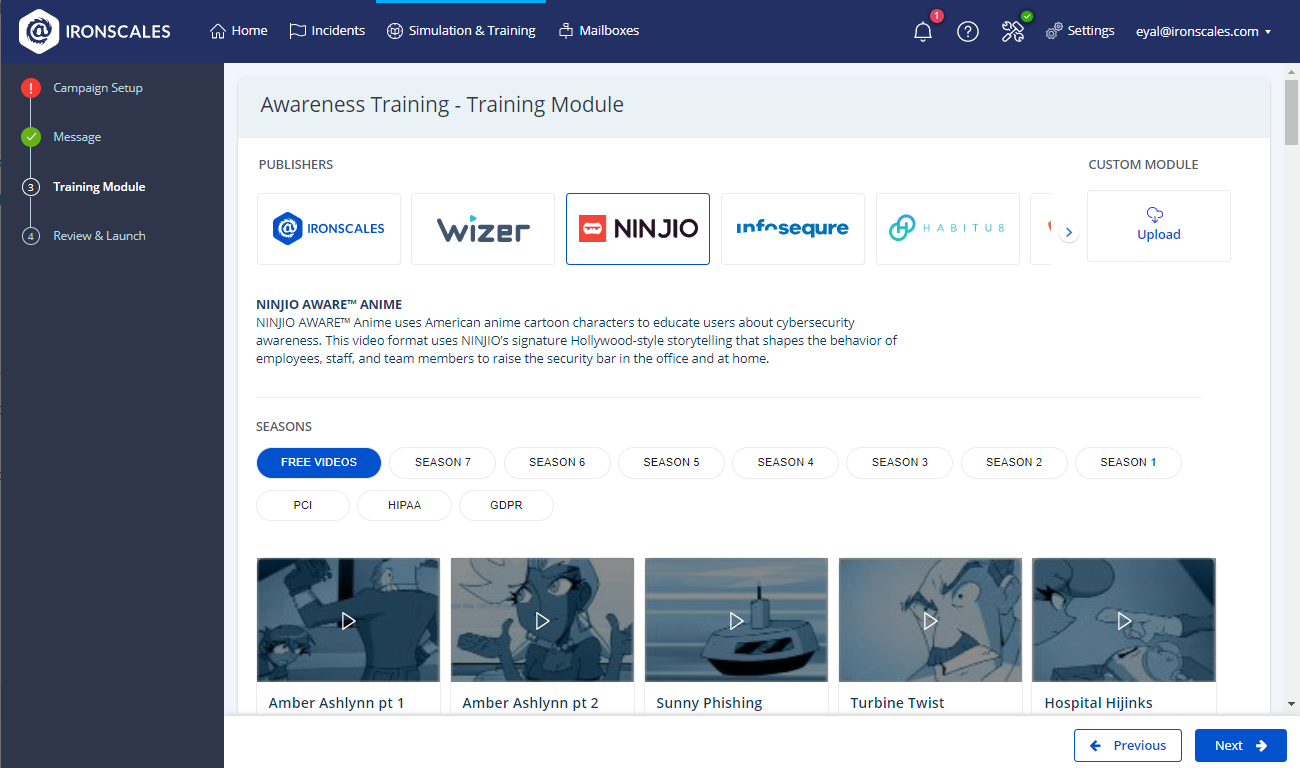
IRONSCALES training modules
A distinctive feature of IRONSCALES is its adaptive learning capability. Unlike M365’s static training modules, IRONSCALES tailors the training content based on how employees interact with the simulations (pass, fail, no-attempt). This dynamic approach ensures the continuous evolution and personalization of the training, making it more effective for each team member.
Incorporating an advanced phishing simulation platform like IRONSCALES into your M365 environment transcends routine training. It creates a more formidable, adaptive defense strategy against phishing, equipping a team to be responsive and well-prepared to handle the ever-changing landscape of cyber threats.
Best practices for phishing simulations with M365
Phishing simulations in a Microsoft 365 (M365) environment is a process that demands meticulous planning and execution. Here’s an enhanced guide to conducting effective simulations in a variety of areas:
- Planning: Set clear objectives for the phishing simulation, targeting employee vulnerability and skill improvement.
- Simulation design: Customize scenarios to match employee tech-savviness using M365’s template library for realistic threats.
- Payload customization: Design payloads specific to your organization using internal addresses and varied types for realism.
- Target selection: Segment targets by role or phishing history, using M365 for targeted simulations.
- Simulation Timing: Schedule irregular simulations with diverse social engineering techniques to maintain alertness.
- Automation: Use automation for consistent, regular testing, balancing frequency and operational impact.
- Realistic elements: Craft convincing phishing emails with detailed, interactive landing pages for immediate feedback.
- Analysis and adaptation: Analyze simulations to identify weaknesses, using M365 analytics for tailored training.
- Training integration: Connect simulations to training modules to promote continuous education.
- Iterative improvement: Evolve simulations based on feedback and trends, aligning with organizational needs.
- Regulatory compliance: Ensure that simulations meet legal standards like GDPR or HIPAA, balancing training and ethics.
By adopting this comprehensive approach, organizations can create a robust defense against phishing threats. This methodology educates employees and equips the organization to counter real-world phishing challenges using M365 effectively.

Conclusion
Mastering phishing simulations is an art that blends precision, creativity, and strategy. It’s about strengthening minds, not just defenses. Using Microsoft 365’s features with advanced tools empowers organizations to thwart attacks and foster a resilient cybersecurity culture. Remember, the aim goes beyond defense: The goal is to create a mindful environment where every click contributes to collective cyber resilience. Your technical expertise guides your team to a safer digital future.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










