Microsoft Defender Licenses
In its latest Digital Defense Report, Microsoft’s telemetry data reveals a staggering surge in ransomware attacks which have increased by over 200% since September 2022. Notably, 40% of ransomware encounters are now attributed to human-driven assaults, often orchestrated by ransomware-as-a-service affiliates, whose numbers have grown by 12% in the past year. A significant shift in attack tactics has been observed, with a sharp rise in remote encryption during human-operated ransomware incidents, emphasizing attackers’ efforts to minimize their digital footprints.
To counter these hacking techniques, which are growing in variety and complexity, Microsoft made significant investments in its extended detection and response (XDR) solution, Microsoft Defender XDR (formerly known as Microsoft Advanced Threat Protection). Defender XDR has evolved a lot from its beginnings and is now a centralized platform for many security products that Microsoft provides, including:
- Microsoft Defender for Endpoint (MDE)
- Microsoft Defender for Office (MDO)
- Microsoft Defender for Identity (MDI)
- Microsoft Defender for Cloud Apps (MDCA; formerly Microsoft Cloud App Security or MCAS)
As the platform expands, its licensing schemes become increasingly complicated. To help make sense of Microsoft’s licensing models, in this article, we walk you through Defender XDR and its components, emphasizing the differences among them and how their additional security features can enhance your company’s overall security.
Summary of Microsoft 365 Defender components and licensing
| Component/concept |
Description |
|
Microsoft Defender for Endpoint (MDE)
|
MDE enhances endpoint protection against threats and enables security teams to perform incident response centrally.
|
| Microsoft Defender for Identity (MDI) |
MDI enables monitoring and protection of the Active Directory environment. |
| Microsoft Defender for Cloud Apps (MDCA) |
MDCA helps detect Shadow IT as well as protect and monitor all cloud traffic. |
| Microsoft Defender for Office 365 (MDO) |
MDO protects and monitors Exchange Online traffic and user interaction with suspicious emails. |
| Complementary solutions for enhancing security |
While Microsoft Defender provides a solid solution, most of its products can be enhanced with other solutions on the market. |
What is Microsoft Defender XDR, and how is it licensed?
Microsoft Defender XDR is Microsoft’s attempt to create a unified platform for the security of an organization that allows control over everything from a single place. By integrating several Defender products, such as MDE, MDO, MDI, and MDCA, Microsoft Defender XDR provides a single portal that gathers, filters, analyzes, and reacts to threats all across the organization’s digital estate.
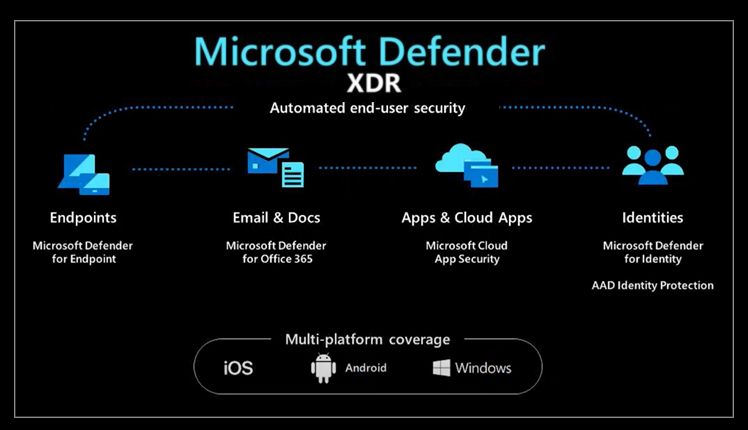
Microsoft Defender XDR functionality (source)
In the sections below, we look at what these products provide and how they are licensed.

Microsoft Defender for Endpoint (MDE)
MDE is a product that helps detect, prevent, and respond to advanced threats on endpoint devices in Windows, Linux, or MacOS. Split into two different plans, it offers different security features to ensure that devices are protected from any threat within the network or from outside.
MDE Plan 1
The figure below provides an overview of MDE Plan 1.
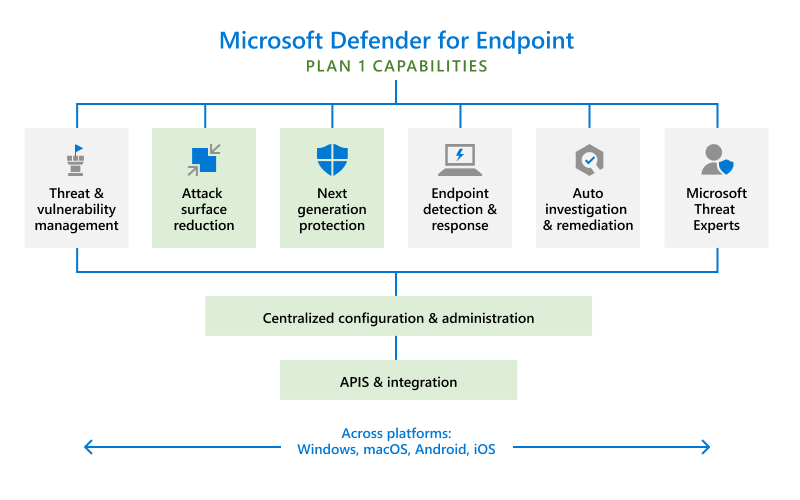
Microsoft Defender for Endpoint Plan 1 capabilities highlighted in green (source)
Notable functionality:
- Attack surface reduction: Presents various rules and security recommendations including:
- Blocking abuse of exploited vulnerable signed drivers
- Blocking Adobe Reader from creating child processes
- Blocking all Office applications from creating child processes
- Stopping credential stealing from the Windows local security authority subsystem (lsass.exe)
- Next-generation protection: Offers enhancements to Microsoft Defender Antivirus by enabling the cloud to use distributed resources as well as various machine learning capabilities (like metadata-based ML, behavior-based ML, and AMSI-paired ML) to deliver protection on endpoints.
Licensing model: MDE Plan 1 is available in the following subscription bundles:
- Microsoft 365 Enterprise 3 (E3) / Education 3 (A3) / Government 3 (G3)
- Microsoft 365 E5/A5/G5/F5 Security Add-on
- Microsoft Defender for Endpoint Plan 1 standalone license

MDE Plan 2
MDE Plan 2 is an enhanced alternative to MDE Plan 1 that provides additional security functions. Its AI-driven capabilities, together with the cloud infrastructure that analyzes trillions of security signals monthly, create a shield around your endpoints.
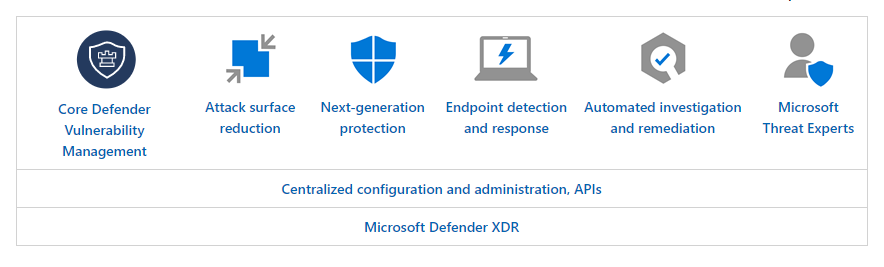
Defender for Endpoint Plan 2 capabilities (source)
Upgrades from Plan 1:
- Endpoint detection and response: While Defender for Endpoint Plan 1 provides some generic EDR features—such as antivirus scans, quarantining files, and device isolation—Plan 2 enables Live Response for remote connections to the device(s) and advanced threat hunting queries for thorough log investigations.
- Vulnerability management: Enables continuous monitoring of the infrastructure in search of any vulnerabilities or weaknesses that can cause compromise.
- Automated investigation and remediation (AIR): Allows Defender to take actions automatically instead of waiting for an operator to respond. It generally works on the principle of “What would a security operator do?”
- Defender for Endpoint deception licensing: Creates fake devices, usernames, or even fake cached credentials specifically to lure attackers and alert the security team of the attacker’s presence on the network.
Licensing model: Defender for Endpoint can be found in several subscriptions, such as:
- Microsoft 365 E5/A5/G5
- Microsoft 365 E5/A5/G5/F5 Security Add-on
- Microsoft 365 F5 Security & Compliance
- Microsoft Defender for Endpoint Plan 2 standalone license
Microsoft Defender for Identity (MDI)
Formerly known as Azure Advanced Threat Protection, MDI is the Microsoft solution for monitoring and reacting to threats within your Active Directory environment. By analyzing the traffic, you can detect and respond to various attack scenarios, like Kerberoasting, pass-the-hash attacks, lateral movements, and password sprays. It also creates a baseline of normal user behaviors to then spot anomalies in users’ activities and alert security teams.
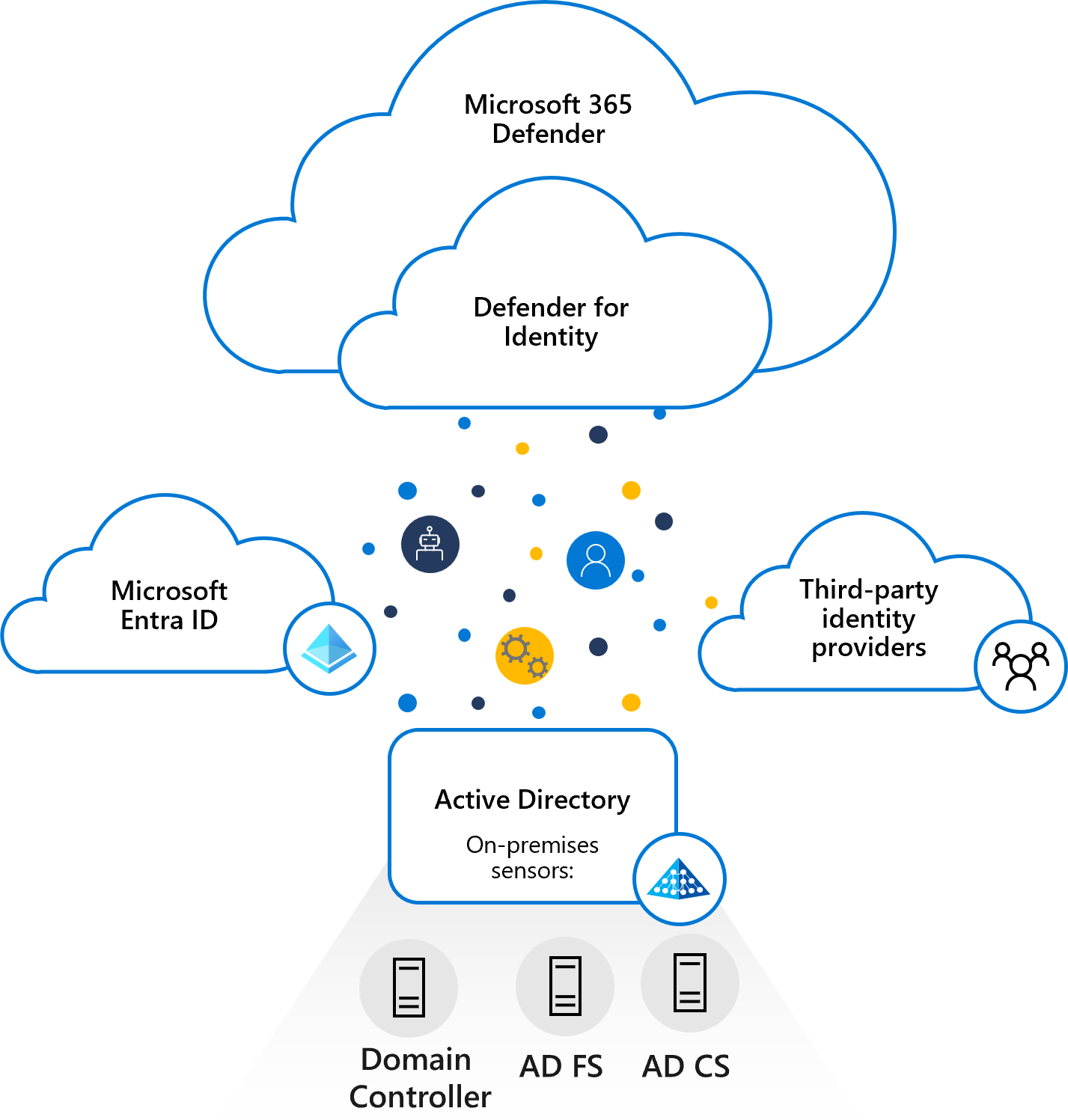
Microsoft Defender for Identity Architecture (source)
Notable functionality:
- Security posture assessment: This feature identifies and alerts you about various misconfigurations of your Active Directory environment(s) based on the group policies established, such as clear password usage.
- User behavior modeling: Used together with Defender for Cloud Apps, this function allows you to investigate users based on their normal actions/activities and alert if their activity deviates from the baseline.
Licensing model: Microsoft Defender for Identity is available via:
- Microsoft 365 E5
- Enterprise Mobility + Security E5
- Microsoft Defender for Identity standalone license
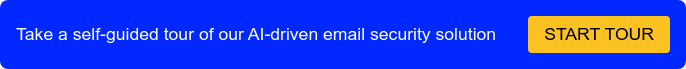
Microsoft Defender for Cloud Apps (MDCA)
MDCA is a rather unique security product with plays several roles in your cloud security, such as discovering shadow IT, protecting information in M365 cloud apps (Sharepoint, Teams, etc.), blocking or allowing other cloud providers, and analyzing how users interact with these cloud apps.
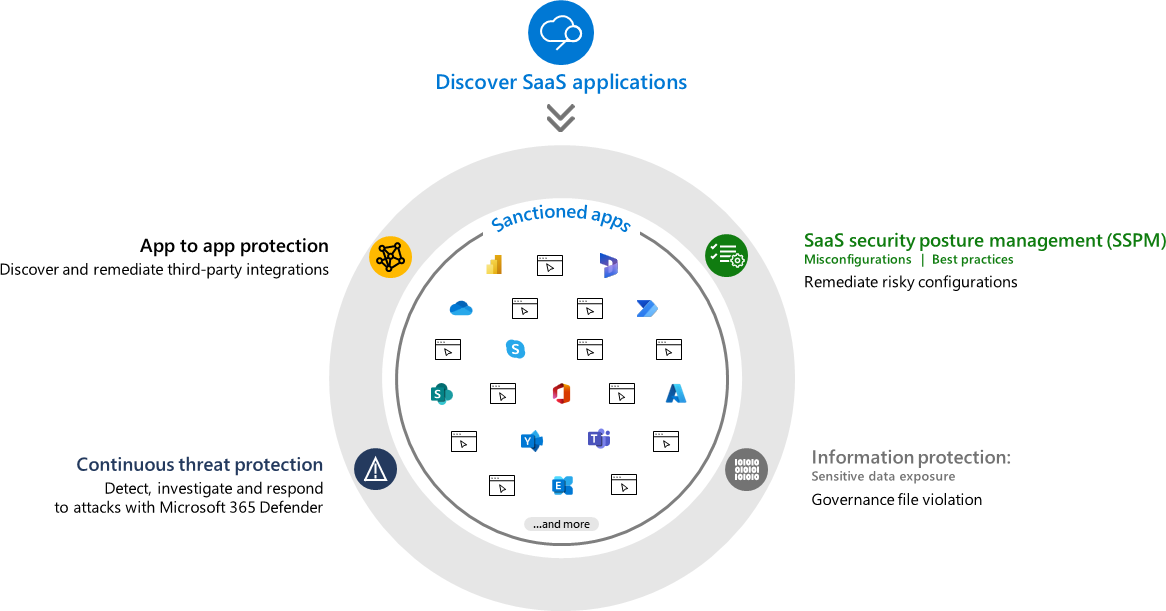
Microsoft Defender for Cloud Apps capabilities (source)
Notable functionality:
- Detect suspicious user activity: Using MDCA with Defender for Identity, you can monitor user activity in cloud apps for unusual or suspicious behavior (e.g., a user logs in from an unusual location). This can be followed up with automated actions such as blocking a user or considerably increasing the risk score for that user.
- Discover shadow IT: This allows you to see how your users interact with various cloud apps that you don’t necessarily control. You can block these apps or move them into a monitored category. For example, blocking Dropbox or other unauthorized cloud providers might help protect your company against a potential data leak.
- Discover and protect sensitive information: Since MDCA is integrated with your cloud services, such as SharePoint Online, it can also be used to safeguard sensitive information using Azure Information Protection labels that you configure to secure cloud data.
- Protect cloud apps: By using the MDCA application proxy, you can protect apps from data exfiltration by malicious insiders or other threat actors. This includes actions such as downloading, copying, or uploading various information.
Licensing model: MDCA is only available through:
- Microsoft M365 E5
- Microsoft Defender for Cloud Apps standalone license
Microsoft Defender for Office 365 (MDO)
MDO safeguards your organization’s email through preset email security policies, email logs, email quarantine, real-time reports, and phishing simulation functionality. It also includes incident response capabilities, such as blocking email senders or malicious URLs. The features of Microsoft Defender for Office (MDO) vary by subscription level, with distinct offerings in Plan 1 and Plan 2. Let's delve into the specifics of what each plan includes.
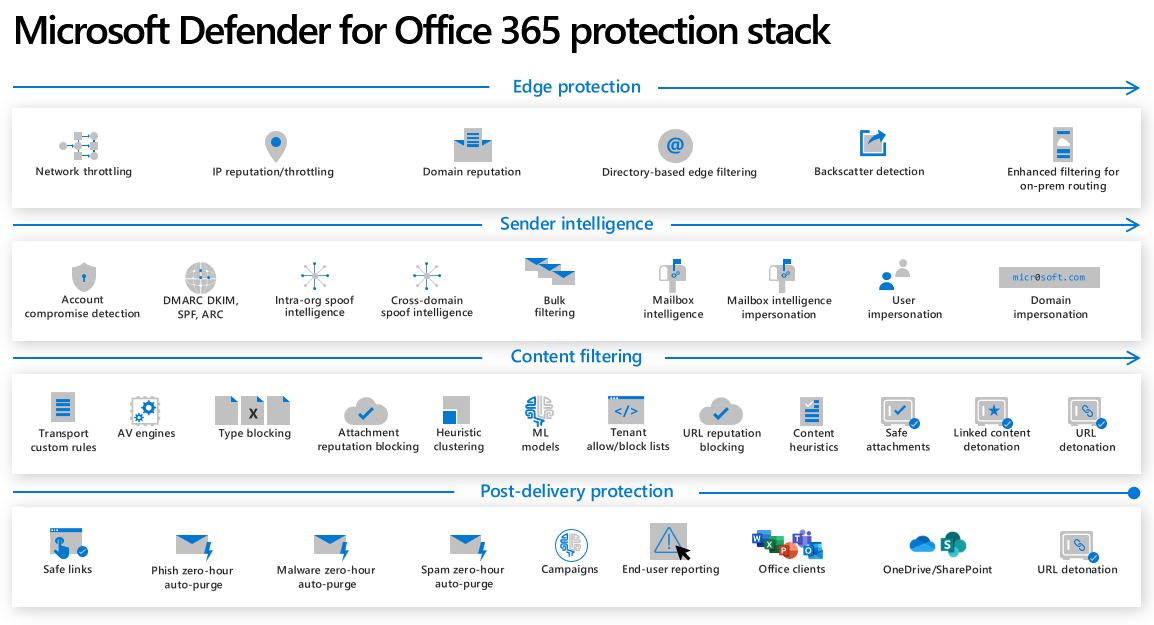
Microsoft Defender for Office 365 capabilities (source)
MDO Plan 1
Upgrading from Exchange Online Protection to MDO Plan 1 elevates your security from a prevention-focused approach to a detection-focused approach. This means that we start looking into possible threat actors that might come with links or zero-day attacks.
Notable functionality:
- Safe Links: Tracks links that you receive via the Exchange service and verifies them against an existing threat list. If the link is unknown, Safe Links will open it in a sandbox to ensure that the destination does not contain a malicious threat.
- Safe Attachments in Exchange, Sharepoint, OneDrive, and Teams: Monitors attachments received in Exchange or Office cloud apps to ensure that the files are not malicious by verifying them in a sandbox environment. Real-time scanning and file availability can be configured to ensure that users don’t feel that their productivity is impacted.
- Advanced anti-phishing policies: Additional functionalities for Exchange Online policies will also verify that your user or domain was not spoofed or impersonated.
Licensing model: MDO Plan 1 is only available as a standalone license. Microsoft 365 E3 does not contain this license.
Prerequisite: Exchange Online Protection license (contained in Exchange Online Plan 1 and Plan 2).
MDO Plan 2
MDO Plan 2 builds upon Plan 1 to bring you investigation and response capabilities on top of what you have enabled using EOP and MDO. By enabling automated investigation and response (AIR) and Threat Explorer, you get a comprehensive view of the threats your organization faces.
Differences from Plan 1:
- Threat Explorer: This feature brings an improved experience by verifying specific attacks, such as specific attack campaigns, as well as allowing the triggering of an automated investigation.
- Automated investigation and response: This capability helps enhance security operations efficiency by initiating automated investigations in response to alerts or requests from Threat Explorer. It provides detailed findings and recommended actions for security teams to review, approve, and execute remediation actions.
Licensing model: You can find this license in the following bundles:
- Microsoft 365 E 5
- Microsoft 365 E5 Security
- Office 365 E5
- Microsoft Defender for Office 365 Plan 2 standalone license
Complementary solutions for enhancing security
If your current subscription choices don’t meet all your needs and you're looking to extend protection to email traffic without incurring high costs for additional features, consider leveraging a comprehensive solution like IRONSCALES. This platform enhances cybersecurity awareness among your employees through targeted security awareness training campaigns, phishing simulations, and in-depth reporting, all customized to your organization's specific requirements.
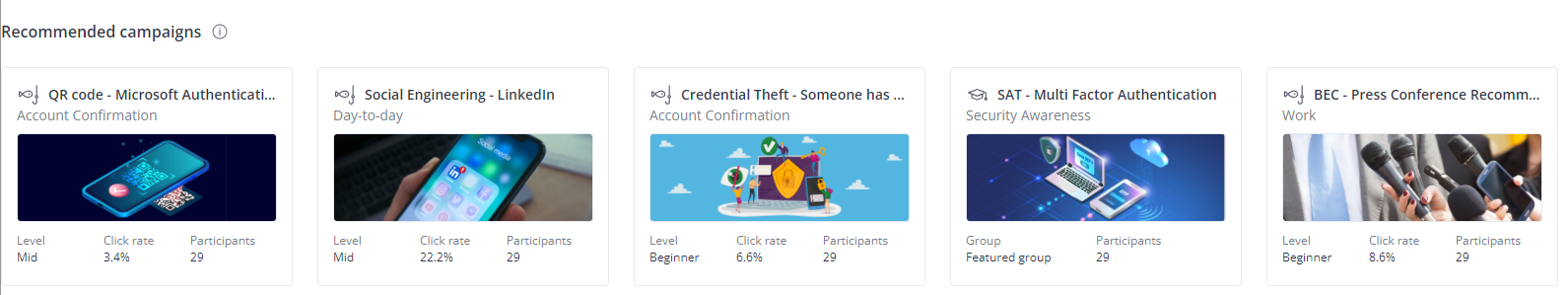
Recommended training campaigns in the Ironscales portal (source)
Together with its Crowdsourced Threat Intelligence capabilities that connect you with a network of over 30,000 security experts, you can ensure that your organization is protected from advanced and never-seen-before email threats.

Conclusion
Microsoft Defender XDR is a unified platform for securing an organization’s digital estate. It includes several Defender products, each with its own licensing model and security functionalities. By controlling everything from a single platform, organizations can ensure the safety of their digital assets.
To bring email security to the next level, companies can also benefit from additional security solutions such as IRONSCALES, an AI-powered anti-phishing and email security solution that integrates effortlessly with M365.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










