Smishing vs Phishing | What’s the difference?
Smishing (SMS phishing) is a phishing variant that occurs over text messages and messaging apps like WhatsApp, Signal, and Telegram. Smishing threats have become so prevalent the Federal Communications Commission (FCC) issued an alert on rising “scam robotexts” threats.
Fortunately, several mitigations and strategies can help organizations reduce the risk of smishing threats and other phishing variants. For example, verifying a phone number using a reliable, primary source and being careful about opening links from unknown senders are two techniques that can reduce smishing risk.
In this article, we’ll explain the differences between smishing vs. phishing (and vishing) and how to reduce the risk of falling victim to one of these attacks.
Summary of key smishing vs. phishing concepts
The table below summarizes the smishing-related concepts this article will explain in more detail.
| Concept |
Description |
|
Understanding smishing vs. phishing vs. vishing
|
All three are social engineering attacks. What differs is the attack medium. Smishing uses text messaging and messaging apps. Vishing uses voice. Phishing attacks use various communication mediums, with email being the most common.
|
| What is phishing? |
A form of social engineering that aims to extract sensitive information or trick individuals into performing an unwanted action. In the context of "smishing vs. phishing," a narrow definition of phishing that considers email the only attack vector is often used. |
| What is smishing? |
A text message-based social engineering attack that usually includes links. |
| What is vishing? |
A phone-based social engineering attack. |
| Techniques for defending against phishing vs. smishing vs. vishing |
While the differences in communication medium will make the specific implementation details different, techniques and practices such as user awareness training, exercising caution with requests to provide information or click a link, and leveraging purpose-built tools can help reduce the risk of phishing, smishing, and vishing. |
Understanding smishing vs. phishing vs. vishing
Phishing, smishing, and vishing are similar types of social engineering threats. The key difference is that smishing attacks occur over text messages, whereas other phishing attacks use different mediums. For example, vishing attacks use voice. The sections below explain each of these attacks in more detail.
What is smishing?
Smishing is a form of social engineering where the attacker uses text messages or messaging apps as the medium to communicate with the victim.
Smishing messages often look like legitimate texts from common auto-texting services and, like phishing, include links or ask for sensitive or delicate information such as your Social Security number, birth date, or mother’s maiden name. The scammers may use similar numbers as some of the standard texting services you have been in touch with and might show up in the same conversation as other legitimate texts from non-scamming entities.
Dissecting a smishing attack
Several key characteristics can help users identify a smishing attack. Like other phishing variants, smishing attacks are likely to attempt to induce a sense of urgency and directly or indirectly prompt you to reveal information or take action.
Common smishing attack characteristics include:
- Unexpected messages- An out-of-context message, such as one from a brand you don’t use or one that arrives at an unusual time, can indicate a smishing attempt.
- Links- Often, smishing messages include links that may perform malicious actions such as redirecting to an attacker-controlled website once clicked.
- Appearing to come from a government agency or financial institution- Attackers frequently send messages that appear to be from institutions such as banks or the IRS to invoke a sense of urgency and compel victims to release sensitive personal or financial information.
If you are not expecting a text and it’s from a crucial or sensitive source, such as your bank or credit card provider, double check by calling the company about the legitimacy of the text.
Sophisticated smishers will even provide logos or other legitimate links to further obfuscate the genuine nature of the scheme and put you at ease, the same way the phishers use similar email subjects and fake domains to trick the victim.
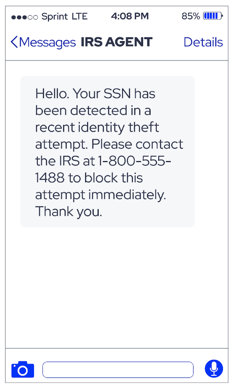 An example of a smishing attempt that utilizes a voice call component.
An example of a smishing attempt that utilizes a voice call component.
What is phishing?
Phishing is a form of social engineering that aims to extract sensitive information or trick targets into taking an unwanted action and can involve multiple communication mediums, with email being the most common.
The definition of phishing is broader than smishing and vishing. In fact, vishing and smishing are considered phishing variants. That’s why the topic of smishing vs. phishing can be confusing. Many definitions of phishing include SMS and messaging apps as possible communication mediums.
However, when comparing phishing to a phishing variant, such smishing vs. phishing, the definition of “phishing” is sometimes constrained to use only email as the attack method / vector.

What is vishing?
Vishing is a form of social engineering where the attacker uses voice calls as the medium to communicate with the victim.
Vishing scams involve attackers calling victims and posing as a legitimate institution, such as the local sheriff. Vishing attacks can be automated robocalls, a live call from a scammer, or a combination of both where a robocall is transferred to a human. Attackers may call from local numbers that generally make sense to answer.
Attackers often ask for information or payments, threatening grave consequences if the actions are not completed. For example, a visher may threaten to arrest the victim or hold a loved one in jail unless funds are wired to an account. Always double check the origin number of such calls or voice messages.
Usually, institutions such as banks, law enforcement, or other highly regarded entities will publicly list their phone numbers or provide a hotline for assistance. You can cross reference these numbers or use AI and machine learning software to determine the validity of these calls and voice messages.
Six key techniques for defending against smishing, phishing, and vishing
Social engineering is a game of cat and mouse where attackers adapt techniques to bypass security controls, and security controls evolve to address new techniques. As a result, no single technique can eliminate the threat of smishing, vishing, and smishing. However, there are techniques and strategies you can use to reduce smishing risk drastically.
Below are six tips to help individuals and organizations protect against smishing and other phishing variants.
Validate where a message or call comes from
If you get a text, check the sender’s phone number. If it does not match one familiar to you, or you were not expecting it at that moment (such as during two-factor authentication checks), then take caution before clicking on any links or providing any important information. Keep in mind that it is easy to spoof a phone number, so even if the number matches a known trusted number, call a number listed on a statement, receipt, back of debit/credit card, or similar “secondary source” you trust.
Similarly, double check email addresses for validity. Attackers may make subtle changes to a domain, such as swapping the letter “O” for the number “0”. For vishing, double check the phone number calling. Scammers can use “burner” or number “spoofers” to give them an area code anywhere in the world without signing up in that physical location.

Consider requests for sensitive data a red flag
If a text, email, or phone call results in a request for sensitive data, consider it a red flag. When possible, validate legitimacy before proceeding. For example, if someone claims to be from the local sheriff, you can usually call a dispatch number and confirm who you’re talking to if they request money or other information. Do not give money or information to sources you do not trust, even if they claim to be from legitimate organizations.
Conduct user awareness training
Understanding the red flags that indicate a potential social engineering attack makes employees less likely to fall victim to phishing or smishing. That’s why many companies often put employees through regular security awareness training that can help minimize these risks.
Take caution with links
With both text and email, you can often check a hyperlink’s destination before clicking it, simply by copying and pasting it into the notes app or a text message. However, this will not help with links created from URL shorteners or links that have redirects, so it has a limited ability to help uncover scammer activity.
Don’t send sensitive information over text or email
Do not send sensitive information over text or email unless you are 100% sure of the destination. Even when the destination is known, it is often best practice not to share sensitive information over text under any circumstances. If a person calls and demands (over the phone) that you text or email information, it is best practice to confirm their identity before doing so.
Implement software tools to help identify threats
Use apps to help gauge the nature and validity of text messages and emails, especially apps that help filter out the junk from unknown or unwanted senders and callers.
Fortunately, today, software providers utilize AI and Machine Learning to help people avoid phishing, smishing, and vishing. Software can help organizations reduce risk by:
- Determining the reputation of a given email based on “bounce rates” and automatically rejecting senders with low scores (who are often scammers or other unseemly entities)
- Identifying the spam risk of cell phone calls and help advise you before you even pick up the call
- Grading the integrity of texts and the senders to advise you on the validity of the messages and their included links

Conclusion
Smishing has much in common with other phishing variants, with the key difference being the tactics attackers use via SMS and messaging apps. The key takeaway for security-conscious organizations is that they must protect themselves across all the communication mediums attackers use.
Threat actors are constantly working to exploit victims through phishing, smishing, and other social engineering schemes. Fortunately, with the proper precautions, a security-conscious mindset, and the right tools, you can significantly reduce the risk of catastrophic breaches.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










