Protecting against executive phishing
Executive phishing is a type of spear phishing attack that explicitly targets high-level executives within an organization. Because executives have access to sensitive data and systems, they are high-value targets for attackers seeking to steal valuable information or disrupt operations. Executive phishing attacks use social engineering tactics to create convincing emails that appear to come from a trusted source, such as the CEO or CFO, to trick the recipient into divulging sensitive information or providing access to critical systems. This might sound similar to whaling, but whaling is a broader term that encompasses all spear-phishing attacks targeting high-value individuals within an organization, regardless of their specific role.
While phishing attacks are a well-known threat in the cybersecurity world, executive phishing attacks are particularly dangerous because they are highly targeted and use sophisticated socially engineered techniques to create convincing emails that can be difficult to detect. Threat actors may use these attacks to access sensitive data, compromise systems or steal financial information.
According to a report by the Anti-Phishing Working Group (APWG), in the third quarter of 2022, there were 1,270,883 total phishing attacks observed, a new record and the worst quarter for phishing that APWG has ever observed. The report indicates that phishing attacks are becoming more common and more advanced as attackers develop new tactics to evade detection and successfully target high-value individuals such as executives.
This article will take a closer look at executive phishing, including the five key security weaknesses that make it such a risk and mitigation techniques for those weaknesses.
Summary of key security weaknesses that enable executive phishing
C-level executives are high-value targets for phishing attacks due to their access to sensitive data and systems. The table below summarizes the key security weaknesses that enable executive phishing.
| Security weakness |
Description |
|
High-value targets
|
As high-level executives, they have access to sensitive data and systems, making them attractive targets for attackers.
|
| Targeted attacks |
Phishing attacks aimed at executives at the C-level are often highly targeted and may use sophisticated techniques, such as spear-phishing, to create convincing emails that are more difficult to detect. |
| Busy schedules |
C-level executives are often busy and may not have time to review emails thoroughly or verify requests, making them more susceptible to social engineering tactics. |
| Lack of awareness |
While executives may be highly experienced in their field, they may not be as familiar with cybersecurity risks or the latest phishing tactics, making them more vulnerable to attacks. |
| Trust in authority |
Phishing attacks often use social engineering tactics to create a sense of urgency or authority, such as posing as a CEO or government official. |
What is executive phishing?
Executive phishing is a form of phishing focused on compromising high-level employees within an organization.
In an executive phishing attack, the attacker sends a spoofed email that appears to come from a trusted source, such as the CEO or CFO, to another high-level executive within an organization. The email is carefully crafted to create a sense of urgency or importance, using social engineering tactics to trick the recipient into taking action, such as clicking on a link, performing a malicious action, or divulging sensitive information.
Suppose the victim falls for the phishing email and takes action. In that case, they may unwittingly provide the attacker access to their account or sensitive information, which can then be used to steal data or initiate fraudulent transactions.
An example of an executive phishing email can be seen in the following image:
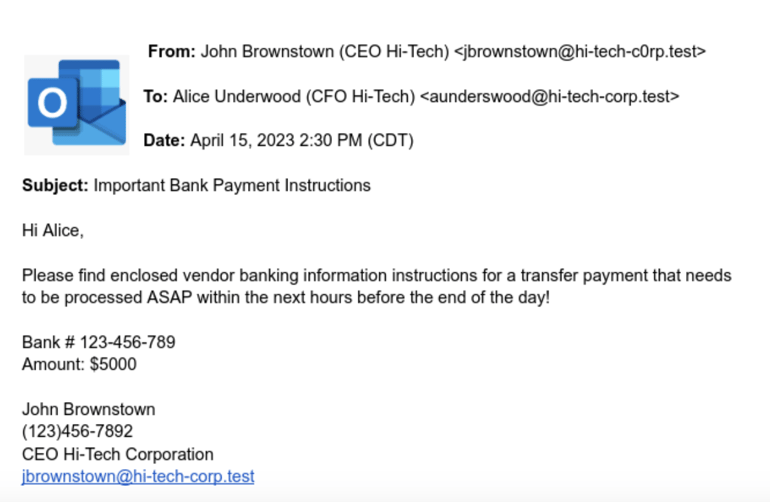

The CEO's email address and the domain name have been spoofed, simulating the real domain name of the organization's email domain name. The email has been sent to the CFO, who is being instructed to perform a monetary transaction immediately.
Executive phishing risks and mitigations
Executive phishing is such a prevalent threat because of the combination of weaknesses associated with the attack. The sections below explain five executive phishing weaknesses and mitigations that can help enterprises protect themselves.
Executive phishing weakness #1: High-value targets
C-level executives are often responsible for making strategic decisions that can significantly impact the organization. They have access to financial data, intellectual property, and other confidential information that can be highly valuable to attackers. This makes them a prime target for phishing attacks, as attackers seek to gain access to this information for financial gain, corporate espionage, or other malicious purposes.
Moreover, executives at the C-level are often in positions of authority within an organization, which can increase their susceptibility to social engineering and raise their risk of being targeted by phishing attacks. Attackers may use tactics such as impersonating a CEO or other VIP to create a sense of urgency or importance in their phishing emails, increasing the likelihood that the victim will fall for the attack.
How to mitigate the risks associated with high-value targets
To reduce the risk of high-value targets falling victim to executive phishing attacks, enterprises should take extra care to ensure executives follow email security best practices. For example, all executive accounts should be protected with multi-factor authentication (MFA)/two-factor authentication (2FA). Security awareness training (SAT) is especially important for high-value targets, it isn’t uncommon for VIPs to be excluded from SAT excercises because they are assumed to be too busy or not susceptical to falling victim to phishing attacks .
Executive phishing weakness #2: Busy schedules
C-level executives often have demanding schedules, with a high volume of emails, meetings, and other responsibilities that can make it difficult to thoroughly review each message or verify the authenticity of a request before taking action. C-level executives may be more susceptible to these types of requests, as they may not have the time to carefully review the email or to follow up on the authenticity of the request. In some cases, they might even have fewer security controls implemented on their accounts, like easy-to-remember passwords, making them easy targets.
How to mitigate the risks associated with busy schedules
To prevent busy schedules from being a security weakness, organizations should provide regular security awareness training to help executives and other employees recognize and avoid phishing emails that use urgency or time pressure as a tactic. Additionally, organizations should encourage employees to take the time to verify the authenticity of requests by contacting the sender using different communication channels like phone or in person, particularly those that require sensitive information or financial transactions.

Executive phishing weakness #3: Trust in authority
Trust in authority refers to the fact that an executive phishing attack involves impersonating or spoofing an executive in the C-level hierarchy of the organization and targeting low-level hierarchy employees or, in some cases, other employees at the same C-level to take action divulging sensitive information or performing a malicious action like a financial transaction or transfer of money.
Like any other phishing attack, it often uses social engineering tactics to create a sense of urgency or importance, making other executives more likely to trust such requests due to the attacker's position of authority impersonating a C-level executive or the urgency of the matter at hand.
How to mitigate the risks associated with trust in authority
To prevent trust in authority from being a security weakness, organizations should provide recommendations in their security awareness training to always verify the source and check if these requests are valid, checking with the source and using out-of-band methods. Employees should be encouraged to verify the authenticity of requests that appear to come from a trusted source and not be afraid of checking even though the sender is at a higher authority level.
Executive phishing risk #4: Lack of awareness
While C-level executives may be highly experienced in their field, they may not be as familiar with cybersecurity risks or the latest phishing tactics, making them more vulnerable to phishing emails.
Phishing attacks are constantly evolving, and attackers are using increasingly sophisticated techniques to bypass security measures and create convincing emails that can be difficult to detect. Executives at the C-level may not be aware of these new tactics or underestimate the risks posed by phishing attacks, making them more likely to fall for a phishing email.
How to mitigate the risks associated with lack of awareness
To prevent lack of awareness from being a security weakness, organizations should provide regular security awareness training to all employees, including executives, to help them recognize and avoid phishing emails. Phishing Simulation Testing should use the latest real-world phishing tactics, common characteristics of phishing emails, and promote best practices for identifying and reporting suspicious emails. Executives at the C-level should ot skip training and be part of Phishing simulation exercises as every other email user in the organization, regardless of their role.
Executive phishing risk #5: Targeted attacks
Phishing attacks aimed at executives at the C-level are often highly targeted. They may use sophisticated techniques, such as spear-phishing or whaling, to create convincing emails that are more difficult to detect.
Attackers may use information gathered through reconnaissance from social media sites like LinkedIn and Twitter, where the executives post business information like goals and objectives of the organization, and using search engines to find the online presence of the executive to create convincing emails that are tailored to the interests, job roles, or other characteristics of them. These emails may use personal details, such as the recipient's name, job title, or recent activities, to create a sense of legitimacy and trust.
How to mitigate the risks associated with targeted attacks
To prevent targeted attacks against company VIPs from being a security weakness, organizations should implement security measures to protect against executive-phishing attacks, such as special monitoring of email spoofing of their accounts, stricter security configuration like 2FA, email security rules like data loss prevention (DLP), email encryption for sending sensitive information and email filtering solutions.

Summary
Executive phishing attacks are a significant threat that organizations must take seriously. C-level executives are high-value targets for attackers. Phishing attacks can exploit various security weaknesses, including trust in authority, weak passwords, busy schedules, lack of awareness, and targeted attacks. Organizations should implement a comprehensive cybersecurity strategy to prevent executive phishing attacks, including cutting-edge security solutions such as AI/ML-based solutions, regular security awareness training, strong password policies, regular phishing simulations, and regular security audits.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










