Best Practices to Defend Against Barrel Phishing
Barrel phishing or “double-barreled phishing” is a form of spear phishing where the attacker sends several (benign) emails to the victim to gain the victim’s trust before making a malicious request. Unlike traditional spear phishing or whaling attacks, which send a single email to the victim, the attacker first “invests” in establishing a relationship with the victim to build trust and lower his or her guard before sending the actual malicious email. This requires patience from the attacker’s side and research on the victim before making an approach.
What makes this attack particularly dangerous is its conversational nature, which might lead it to fool traditional email security solutions. These solutions scan each email as a separate unit and will not have a sense of the overall email conversation between the attacker and the target, thus missing the barrel phishing attack.
In this article, we will look into some of the best practices to detect and protect against this specific type of phishing attack. Additionally, we will cover some common pitfalls to consider when implementing these defenses and how to avoid them.
Summary of best practices to defend against barrel phishing
| Best practices |
Description and benefits |
|
Implement Integrated Cloud Email Security (ICES).
|
Rely on ICES for enhanced detection and automatic removal of malicious emails with less implementation complexity than SEG.
|
| Deploy NLP-based AI/ML models. |
Increase the chance of detecting barrel phishing by deploying AI/ML models that are specialized in natural language processing (NLP) and can "understand" email conversations. |
| Make use of human intelligence. |
Improve the detection rate of your systems by employing experts who manually analyze barrel phishing trends. |
| Enforce two-factor authentication (2FA). |
Use 2FA to potentially prevent a successful credential compromise from being abused and causing even more damage. |
| Deploy the SPF, DKIM, and DMARC protocols. |
Detect and block emails with spoofed senders before they reach the victim. |
| Invest in an anti-typosquatting service provider. |
Detect newly registered typosquatting domains that might make the email sender look legitimate. |
| Conduct user awareness sessions and phishing simulations. |
Educate employees on this less-known type of phishing and how to detect it. Measure the effectiveness of these sessions and your defenses by conducting phishing simulations. |
Understanding barrel phishing
Before we look into the best practices, let’s first improve our understanding of barrel phishing. The simplest way to illustrate this phishing attack is to think of the notorious Nigerian Letter Scam.
In this scam, the attacker aims to impersonate a member of the royal family, e.g., a prince of a foreign country. In the first email, the attacker explains how his country (e.g., Nigeria) is now unstable and for that reason he must transfer his massive fortune outside his country but needs the victim’s assistance. As a reward, he promises a share of his fortune to the victim for helping him. Once the victim replies with intent to help (thus confirming to the attacker that he has fallen victim to the scam), the attacker sends a second email requesting sensitive information from the victim, such as bank account details, login information, etc.
Barrel phishing is similar to the “Nigerian Prince” scam in the sense that the attacker first tries to establish a sense of trust with the victim before demanding something. The slight difference is that, instead of impersonating a foreign prince, the attacker impersonates work colleagues, trusted entities like the bank or the police, friends, etc. The rest of the process mimics the “Nigerian Prince” scam scheme.
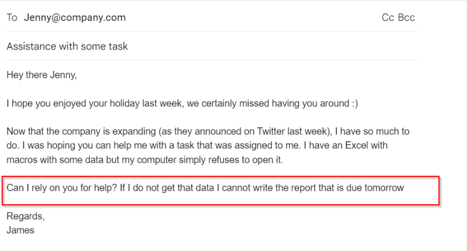
Example of the first email during barrel phishing
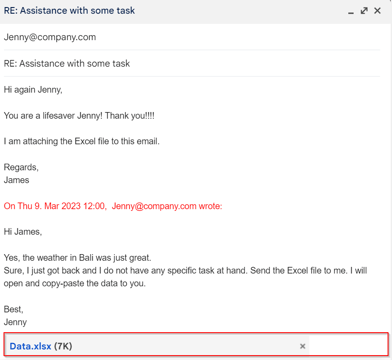
Example of victim’s reply and the second malicious email from attacker
Best practices to defend against barrel phishing
In the rest of this article, we will cover some best practices that can be implemented to detect and stop barrel phishing attacks.

Deploy NLP-based AI/ML models
As we discussed above, in barrel phishing, the attacker sends more than one email to the victim (unlike other types of phishing). They try to have an email conversation with the victim by sending benign emails while trying to earn the victim’s trust. Traditional email security systems aren’t designed to detect this conversational phishing style since they do not “understand” words, context, or conversation and are mostly signature-based.
Artificial intelligence (AI) and machine learning (ML) models are more suitable for this task. More specifically, natural language processing (NLP) is a subfield of ML that is focused on developing ML models and algorithms to enable a machine to understand natural/human language. It breaks down texts into words, sentences, and phrases and tries to extract the meaning or context behind these components. This makes NLP a powerful weapon against barrel phishing. “Understanding” and analyzing the conversation between the victim and the attacker makes it possible to detect the attack the moment the attacker sends the malicious request during the email conversation with the victim.
One way of looking at this is to think of NLP as a third person that is only hearing the conversation between two people without participating in it and then noticing that one of them starts asking for unexpected things from the other. NLP has already been deployed in email security products and is showing promising results.
Implement ICES on top of or in place of SEG
One of the first email security systems, which has been around for years, is the Secure Email Gateway (SEG), which is placed between the Internet and your company’s mail servers. It is designed to scan emails and attachments, perform content filtering, and block malicious emails before they reach potential victims. This is called “pre-filtering” because it filters and blocks emails before they even reach the email server.
This method will fail to detect barrel phishing since SEG scans emails one by one, looking for “matches” to rules and policies, and can’t detect the “intent” of the content of a specific message or across a string of messages sent to a victim. Additionally, it only scans emails coming from the Internet and not emails that employees within the company might exchange with one another. What if one employee is compromised and used to initiate barrel phishing within the company?
Finally, this approach is more complex, tedious, and risky to implement: It requires your company to change the DNS MX record to point to the SEG system and configure it to send the email to it along with requiring that your company buy and maintain the hardware upon which the SEG will run. If the SEG, or supporting service, experiences an outage, emails will fail to be delivered.
Due to these SEG disadvantages, another solution is growing in popularity: Integrated Cloud Email Security (ICES). This relatively new solution is becoming quite popular now that more and more companies are migrating to the cloud, leveraging the benefits of the cloud, such as scalability, ease of management, universal accessibility, and lower hardware maintenance costs.
Unlike SEG, ICES solutions do not require any hardware or changes to the DNS MX record; instead, they use an API to plug right into cloud hosted email services such as Microsoft 365 and Google Workspace . Additionally, it can view both emails from the Internet and those exchanged between employees within the company. Furthermore, some ICES solutions provide advanced features such as data loss prevention (DLP), AI-based heuristics, behavior analysis on the victim, etc., to ensure they stay up to date, adjusting to ever-changing phishing attacks.

Make use of human intelligence
Although email security solutions and AI/ML can detect and prevent a great deal of malicious emails, no system is perfect, and some emerging and creative phishing attacks can still make it to the intended inbox. This is especially the case for barrel phishing, where the attacker converses with the victim over time instead of sending a single email.
It might be difficult for systems to understand irony, slang, or other language specifics, but a human expert will most certainly comprehend a normal conversation followed by a malicious demand. By making use of these human insights and their analysis of real-life barrel phishing emails, makes it possible to constantly improve and “train” the AI/ML models to “smarter” in terms of understanding complex language structures. Such solutions should make use of human insights and ensure that systems remain up to date with the latest barrel phishing developments.
Enforce two-factor authentication
Even long and strong passwords can “fall” due to data breaches, keyloggers, and information-stealing malware, so it is important to implement two-factor authentication (2FA) to help with defending against phishing attacks. Any method of 2FA is helpful, but the current “gold standard” for 2FA uses FIDO2 authentication, a method that is near impossible for attackers to intercept.
In the context of barrel phishing, a compromised account might be used to send barrel phishing emails to other colleagues. What makes this dangerous is that the attacker will have access to past emails between the victim and other colleagues to learn more about the target, helping them craft seemingly trustworthy emails. By enabling and enforcing 2FA across your organization you reduce the impact that a credential leak has on the security of your organization.
Deploy the SPF, DKIM, and DMARC protocols
Barrel phishing, like many other types of phishing, tries to garner trust in the email by attempting to fake the sender of the email in a variety of ways. Over the years, different email security protocols have been developed to prevent attackers from impersonating and sending emails on behalf of domains that they do not own. Sender Policy Framework (SPF) and Domain Keys Identified Emails (DKIM) are two such protocols. Domain-based Message Authentication, Reporting and Conformance (DMARC) takes it one step further and ensures that the attacker does not fake the “From” field that is shown to the user.
Invest in an anti-typosquatting service provider
By deploying the email security protocols described above, you ensure that attackers are not impersonating domains. However, attackers now rely on typosquatting by registering domains with typos (which are, of course, valid domains). For example, if your domain was google.com, you might not notice the difference if the attacker sends an email from goggle.com (notice the double “g” instead of double “o”).
While an attentive recipient will be able to detect such a difference, research has shown that, due to our current world of information overload, readers tend to skim through words and not attentively read 100% of the content. Therefore, it is important to consider purchasing a security product that detects typosquatting domains on phishing emails or similar products that send alerts when such domains are newly registered on the Internet.
Conduct user awareness sessions and phishing simulations
Last but not least, your organization needs to provide regular security awareness training and phishing simulation testing exercises for every employee. Barrel phishing, like other types of phishing, exploits human carelessness, making the employee the weakest chain in your defense. You can reduce the risk of employees falling victim to phishing emails by constantly training them on security concepts, phishing patterns and styles, and the various dangers that phishing presents to the company.
It is also important to measure the results of these training sessions and spot weaknesses in your security defenses by conducting phishing simulations. These simulations will help you identify possible holes in your defenses or gaps in your user training materials. While not every company is big enough to organize periodic user sessions and/or phishing simulations, your organization can consider outsourcing these important tasks to specialized service providers.
Recommendations
While implementing the best practices above, keep in mind some common pitfalls:
- Be aware of marketing terms. A fancy SEG implementation is still SEG, even if it advertises itself as being cloud-based or similar to an ICES setup.
- Before deploying SPF/DKIM/DMARC checks for emails, make sure you run the checks in audit mode to observe if any legitimate email is being blocked. While these email security protocols are being embraced by more and more companies, there are still (small) companies that are not aware of them and either do not use them or have them improperly implemented.
- Do not forget that attackers can send barrel phishing emails to the private email accounts of employees. Since these emails are outside your infrastructure, you cannot see the email interaction with the attacker, thus leaving you with a blind spot. Make sure to include this important fact in user awareness sessions.
- Try to keep user awareness sessions interactive and simple for employees. Keep in mind that most employees are not IT employees and might not understand technical terms the same way as you. Use interactive videos, simplified examples, and animations to make the learning process smoother.

Summary
In this article, we looked into barrel phishing, how it works, and its differences from the traditional phishing attacks that use a single email. We discussed seven best practices that can be used to detect and mitigate barrel phishing attacks. Finally, we presented some common pitfalls and how to avoid them. One key takeaway from this article is that the phishing attack landscape is constantly changing, and traditional email security solutions no longer seem to keep up with these changes.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)











