Table of Contents
“Large organizations (with 10,000 or more employees) anticipate a 43.3% increase in the threat of BEC attacks in the next 12 months.” That’s just one of the many interesting data points from the new Osterman Research whitepaper, Defending the Enterprise: The Latest Trends and Tactics in BEC Attacks, that we sponsored.
Unsurprisingly, organizations see BEC attacks becoming a more significant threat. Here are two excerpts from the report that illustrate how significant respondents perceive the BEC threat:
How much of a threat do you perceive BEC to be 12 months ago, currently, and in the next 12 months?
-
- For all organizations in general?
- For your organization specifically, based on everything you’ve done to prevent BEC attacks, and based on the threat from BEC attacks that you perceive?
Of course, respondents perceived the threats to be lower for their organization compared to all others, but overall, the trend lines over the 24-month period were very similar.
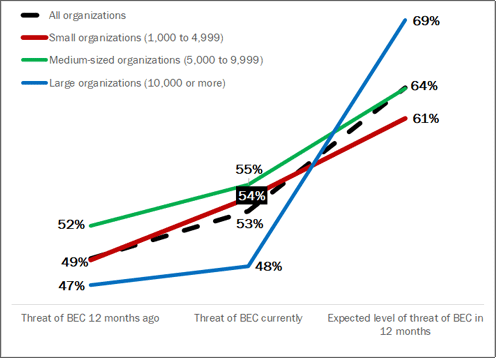 Figure 5 - Perceived Threat of BEC Attacks to Organizations
Figure 5 - Perceived Threat of BEC Attacks to Organizations
Percentage of respondents indicating BEC attacks “a threat” or “an extreme threat”
Threat of BEC Attacks vs Phishing in General
And when we compared this data with responses in our Osterman 2022 Business Cost of Phishing whitepaper, we found that the expected threat level of BEC attacks in 12 months is twice as high as the expected threat level of phishing in general in 12 months.
Here’s what I found curious. Small and medium-sized organizations don’t anticipate the threat of BEC to increase as much as large organizations are anticipating. Why?
It’s safe to assume that larger organizations are better equipped to detect BEC attacks because they have access to:
- Resources: They typically have more resources to allocate to cybersecurity, including more advanced security solutions, dedicated security teams, and more extensive training programs for their employees.
- Experience: They are often targeted more frequently by cybercriminals, which means they should have more experience in responding to BEC attacks and have started implementing new countermeasures (hopefully).
- Network Visibility: Larger organizations typically have more complex networks and monitoring tools to enable them to identify suspicious activity more easily, including unusual email patterns or login attempts from unfamiliar locations.
- Policies and Procedures: They usually have more established policies and procedures around email security, such as guidelines for verifying requests for money transfers or provisioning new vendors in their ERP systems—policies that can help prevent BEC attacks or detect them early on.
While it may seem counterintuitive that larger organizations are more concerned about the threat of BEC attacks than smaller organizations, it's important to remember that cybercriminals tend to target big organizations more frequently because they can potentially yield higher payouts.
In addition, even though larger organizations have more resources and experience in handling cybersecurity threats, cybercriminals are constantly evolving their tactics and finding new ways to breach systems. Therefore, it's critical that organizations of all sizes remain vigilant and continue to invest in advanced security solutions, training, and policies to prevent BEC attacks. As the threat landscape continues to evolve, it's important for organizations to stay up-to-date with the latest trends and tactics in BEC attacks and to work collaboratively to mitigate the risk of such attacks.
BEC Protection Guidance for Smaller Organizations
For smaller organizations, it's essential to recognize that they are not immune to BEC attacks and should take proactive steps to protect themselves. Here are some recommendations that can help smaller organizations protect themselves against BEC attacks:
- Increase Awareness: Delivery training. On a regular basis, use security awareness training (SAT) software and Phishing Simulation Testing solutions to educate and train your employees. They need to learn how to spot spoofing or impersonation attempts, and they need to learn how to verify the authenticity of emails, especially those requesting money transfers or sensitive information. At a minimum, they need to be encouraged to ask for a second set of eyes before they act. BTW – we offer a totally, 100% free Phishing Simulation Testing solution with IRONSCALES™ Starter™.
- Implement Security Policies: It doesn’t require purchasing more software to adopt email security policies and procedures for handling invoice requests and new vendor additions. Some of these best practices, “checks and balance” systems, have been around for a very long time.
- Develop a Response Plan: Develop a response plan in case a BEC attack occurs, outlining the steps to take and the individuals or departments responsible for each step. Make sure that all employees are aware of this plan and know how to respond in case of an attack.
- Add Advanced Email Security: This isn’t just a shameless plug from IRONSCALES, BEC attacks can’t be stopped with secure email gateways or basic security included with Microsoft 365 or Google Workspace—they aren’t built for it. Adding integrated cloud email security (ICES) is the best way to address advanced email BEC, account takeover, and VIP impersonation attacks. You can read more about ICES recommendations in the 2023 Gartner® Market Guide for Email Security.
By taking these steps, smaller organizations can significantly reduce the risk of BEC attacks and protect themselves against potential losses of money, data, and reputation. It's essential to prioritize cybersecurity and invest in the necessary resources to protect against the ever-evolving threat landscape.
Download the latest Osterman Research report, "Defending the Enterprise: The Latest Trends and Tactics in BEC Attacks," to learn more.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)