Table of Contents
One of the exciting updates included in our recent Megalaunch announcement was enhanced account takeover (ATO) detection and remediation. Before we highlight the updates, let’s do a quick overview of account takeover attacks and ATO prevention.
What is Account Takeover?
Account takeover is when an attacker gains access and controls of a user’s account credentials and then uses the compromised credentials to execute a variety of other attacks. They’ll usually start by making account changes to make it harder for the real owner to re-gain control of the account. Once the email account compromise is complete, they can access password managers with login credentials to company bank accounts, resources with the personal data of other employees or customers and move around laterally within the organization’s network to establish additional footholds to launch other types of attacks.
One of the first things attackers often do with stolen credentials is send phishing emails to other employees to widen their account take over within the organization—this type of activity can be difficult to detect since the attacker looks like a real employee to most security tools.
Detection
Detecting an account takeover or a compromised email address isn’t as easy as looking for password changes from a new IP address or device. That type of stuff happens all the time, like when an employee gets a new smartphone. Accurate detection requires advanced analysis of multiple data points across:
- Identity and access management (IAM) event data, such as Microsoft Active Directory events
- Email account-level event data, like new and unusual email handling rules
- Email user behavior and patterns, like emails sent to multiple internal recipients never previously emailed
The number of event combinations across these data sources is massive and finding valid indicators of account takeover is extremely challenging. To avoid false positive alerts, IRONSCALES analyzes multiple types of data, not just Active Directory events, in real-time to identify suspicious user activity and behavioral patterns. For example, multiple failed log on attempts to an application by itself might just mean that the user forgot their password. But combine failed log on attempts + new email forwarding and delete rules + impossible travel activity (where the distance between their last and new login location couldn’t possibly be traveled by an airplane) and you have all the signs of account take over activity.
Remediation
ATO attacks, like Business Email Compromise (BEC), have the potential to spread across an organization like wildfire. One successful attack can lead to data breaches and more compromised accounts, very quickly. As such, IRONSCALES does not auto-classify such incidents but immediately provides SOC analysts with all the necessary information to accurately remediate such incidents themselves to prevent further spread, which is done in two simple clicks.
Updated Incident Views
Megalaunch included several enhancements to Account Takeover (ATO) incident views. A new ATO quick filter provides a view of all ATO incidents during the Last 7 days or Older..png?width=774&name=Enhanced%20ATO%20Ironscales%20-%20Quick%20Filters%20(3).png)
Selecting a user account provides ATO incident details including account details and the suspicious events.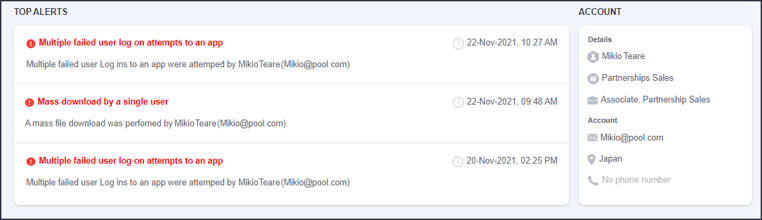
Remediation - each suspected ATO incident displays two buttons – Compromised and Safe.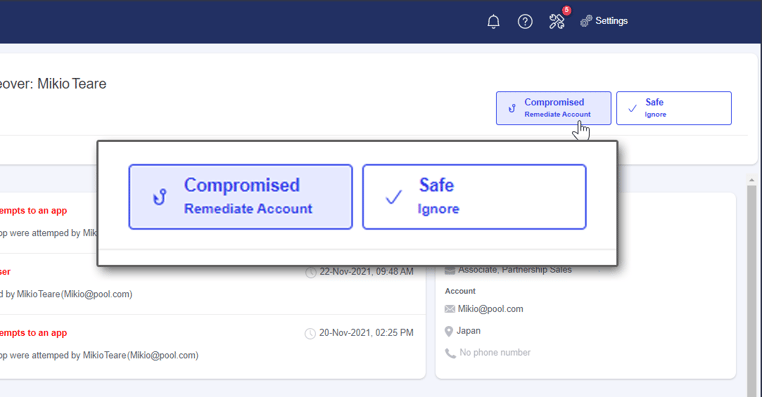
If the SOC analyst classifies the incident as an ATO event, they click "Compromised - Remediate Account" and are prompted to sign the employee out of any active sessions to prevent the attacker from performing any other dangerous actions. 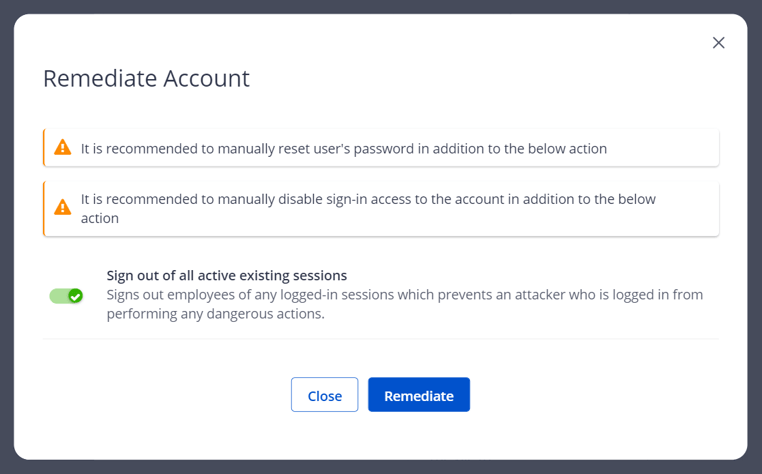
These enhanced views and streamlined remediation workflows add to the unique approaches of Account Takeover Prevention from IRONSCALES, including:
- Real-time analysis of event data for time-sensitive alerts vs processing time-delayed batches of data
- Cross-analysis of multiple data sources instead of Active Directory events alone
- Simple, intuitive 2-Click remediation
And when deploying IRONSCALES™ Complete Protect™ for Microsoft® Office365, you do not need additional licensing for expanded Active Directory capabilities.
Deploy in just a few minutes using our native API integration and you won’t have to make any configuration changes or risk downtime to your operations.
For more information or to request , see our Complete Protect™ page.
Explore More Articles
Say goodbye to Phishing, BEC, and QR code attacks. Our Adaptive AI automatically learns and evolves to keep your employees safe from email attacks.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)







.webp?width=100&height=100&name=PXL_20220517_081122781%20(1).webp)




.png)