Phishing Attack Simulation
Phishing threats have evolved from simple scams into sophisticated, AI-powered campaigns targeting corporate networks with unprecedented precision. In 2024, 73% of all reported cyber incidents were Business Email Compromise (BEC) attacks, with the FBI reporting $2.77 billion in BEC-related losses in the United States alone. The landscape has fundamentally changed: phishing attacks have surged 1,265% since the advent of generative AI tools, with attackers now crafting grammatically perfect, highly personalized campaigns at scale.

Historical phishing attack trends showing the escalation Q4 2024 through Q2 2025 (Source)
Modern attackers leverage multiple sophisticated techniques simultaneously:
- AI-Generated Content: 82.6% of phishing emails now use AI-generated content, creating messages indistinguishable from legitimate communications
- Deepfake Attacks: Voice cloning and video deepfakes enable real-time impersonation of executives (such as the February 2024 Arup incident resulting in $25 million in losses)
- Multi-Channel Campaigns: 41% of phishing incidents now involve attacks beyond email, combining SMS, voice calls, and collaboration tools
- Voice Phishing (Vishing): Surged 442% in 2024, with 37% of large corporations reporting deepfake voice impersonations
- QR Code Phishing: Increased 25% year-over-year, bypassing traditional email security filters
These sophisticated threats bypass traditional security measures including multi-factor authentication through adversary-in-the-middle (AitM) attacks, making proactive defense training more critical than ever.
This article guides you through executing effective phishing attack simulations and showcases how IRONSCALES platform facilitates not only realistic simulations but also integrates security awareness training to keep organizations ahead of rapidly evolving threats.
Summary of core phishing attack simulation concepts
| Concept |
Description |
|
Defining the scope
|
Establishing the parameters, objectives, and success metrics of the simulation to ensure aligned outcomes.
|
| Template preparation |
Designing realistic phishing templates based on real-world data to emulate authentic phishing threats. |
| Target selection |
Identifying and grouping the employees to be tested to ensure a comprehensive assessment of phishing awareness. |
| Campaign setup |
Finalizing the phishing simulation setup by selecting appropriate email templates based on participants' awareness levels, choosing a landing page, and integrating a relevant training module. |
| Campaign test |
Testing out the campaign with a small group to assess the functionality and delivery of the phishing messages. |
| Campaign execution |
Utilizing the IRONSCALES one-click campaign feature to launch the phishing simulation seamlessly and monitor it in real-time for immediate insights. |
| Training integration |
Incorporating security awareness training modules for immediate feedback and reinforcement upon detecting phishing test failures. |
| Analysis and reporting |
Evaluating the simulation results to identify areas of improvement, plan targeted training campaigns, and derive actionable insights for enhancing organizational phishing resilience. |
Understanding phishing simulation
Phishing simulation is a critical exercise that sends fake phishing attacks to your team in a controlled setting to test their alertness to hacker tactics. This proactive measure prepares them to spot and stop actual threats and meets various regulatory requirements, like those of GDPR and HIPAA, that mandate regular security awareness testing. These simulations transform your staff into an informed frontline defense system.
In the coming sections, we’ll detail how to integrate phishing simulations into your security strategy, enhancing your organization’s defensive capabilities with each drill.
Setting the stage for simulation
Integrating IRONSCALES
The integration process is refreshingly straightforward and accomplished in about 3-clicks: Minimal configuration is required, and there’s no need for a complete system overhaul. Compared to other solutions, IRONSCALES does not require updating inbound policies or adding exceptions because it integrates with Microsoft 365 and Google Workspace via API to ensure a smooth adoption for phishing simulation.
Defining the Scope
To help ensure that your phishing simulation delivers actionable insights, let’s dissect the pivotal steps in defining its scope.
Clarifying objectives
Start with a clear statement of what you want to achieve. Here’s a table showing what objectives might look like.
| Objective |
Description of related activity |
Expected Impact |
| Awareness assessment |
Determine the percentage of employees who can identify phishing emails |
Reduced susceptibility to phishing attacks |
| Response evaluation |
Measure the percentage of employees that report or escalate a suspected phishing attack |
Quicker threat identification and mitigation |
| Protocol effectiveness |
Test the efficiency of new security measures against phishing attempts |
Validation and improvement of security defenses |
Choosing metrics
Once objectives are set, select the right metrics to measure success. Key metrics could include the following:
- Click-through rate (CTR): Tracks the percentage of recipients clicking phishing links, indicating susceptibility
- Reporting rate: Measures how many recipients report phishing emails before and after interaction, showing alertness
- Time to report: The average time taken to report a phishing email, which gauges response speed
- Failure rate by department: Identifies departmental vulnerability based on the percentage that fell for the simulation
- Repeat clickers: Monitors users who repeatedly click on phishing links, signaling ongoing risk
These metrics must align with your objectives, such as using CTR and reporting rate for gauging awareness.
Envisioning expected outcomes
Define clear, measurable outcomes linked to objectives, so you can gauge success. For example:
- A CTR below 5% may reflect effective awareness campaigns.
- A reporting rate over 75% suggests a well-informed team.
- Reporting in under 30 minutes indicates swift incident response.
Creating realistic phishing templates
Crafting realistic phishing templates is crucial for effective simulation, and IRONSCALES provides the tools to mirror actual threats. Here’s a streamlined guide.
Creating templates from scratch
Customize your phishing templates within IRONSCALES:
- Start a new template in the Templates section under Content Management.
- Specify the template details, such as name, type, and user awareness level.
- Personalize the sender information using the permitted domains.
- Create the email content with formatting options and attach files or select pages for call to action (CTA) prompts.
- Insert educational tooltips and set custom URLs for a realistic experience.
This approach equips your team to recognize and counter real threats.
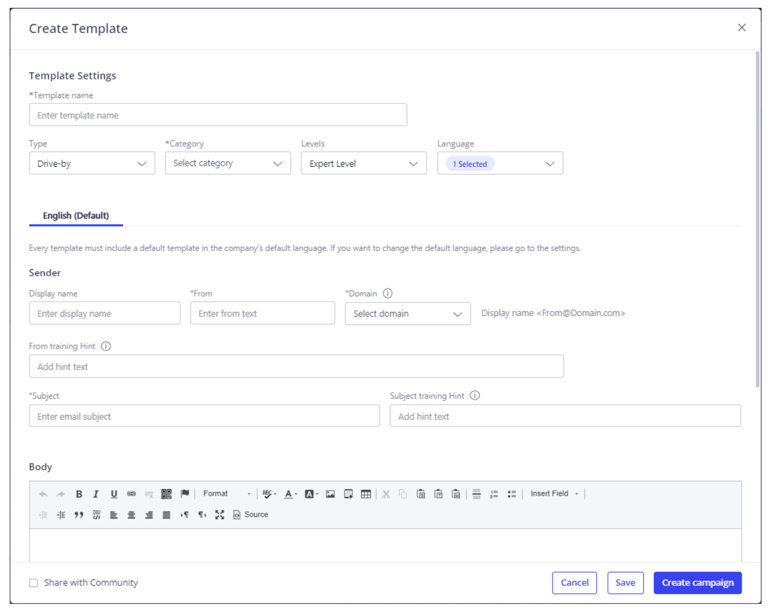
The Create Template dialog box
Using real incidents
IRONSCALES phishing simulator also allows template creation from real or historical incidents:
- Choose to create a template from an incident’s details.
- Modify the sender information and email content to simulate specific scenarios.
- Safely replace harmful content with placeholders.
The platform’s mix of simplicity and customization prepares your team to tackle actual phishing attempts effectively.
Creating an incident template
Target selection
When orchestrating a phishing simulation campaign, one of the initial steps is the meticulous selection of targets. Here, we delve into the segmentation strategy and the frequency and variety settings for the tests.
Segmentation strategy
Segmentation is crucial in creating targeted simulations that yield actionable insights. The following steps outline strategic options for segmenting your workforce:
- By department: Different departments have diverse exposure and susceptibility to phishing attempts.
| Department |
Rationale for targeting |
| Finance |
Financial data |
| Human Resources |
Sensitive employee data management |
| IT |
Access to administrative privileges |
| Operations |
May not be as vigilant as IT-focused teams. |
| Customer Service |
Frequent engagement with external emails |
- By role: Employees’ department roles can affect their risk profiles; for instance, executives may be prime targets for BEC scams.
- Based on previous performance: Past interaction with phishing simulations can offer valuable insights into specific training needs. Employees who have previously fallen for simulations represent a critical area of focus for retesting and education.
Frequency and variety
The frequency and variety of tests are also pivotal. Here’s a guideline to help set an effective schedule:
-
- Frequency:
| Employee segment |
Suggested frequency |
| High-risk groups |
Monthly |
| Medium-risk groups |
Quarterly |
| Low-risk groups |
Biannually |
- Variety:
| Type of Phishing Test |
Delivery Method |
Purpose |
| General Phishing |
Email/SMS (Smishing) |
Awareness for all Employees |
| Spear Phishing |
Email/SMS (Smishing) |
Targeting high-risk roles |

Launching the phishing simulation
Streamlining simulations with the IRONSCALES Quick Launch feature
This feature streamlines the deployment of phishing simulations, enabling security teams to quickly set up and execute campaigns. Here’s how to utilize this efficient tool.
- Choose Quick Launch from the Simulation & Training menu.
- Set the campaign timing for immediate or future deployment.
- Specify target groups based on risk assessment findings.
- Confirm the auto-generated settings, including language, templates, and landing pages.
- Run a test with a select user group for quality assurance.
- Launch the campaign, adjusting any elements as necessary.
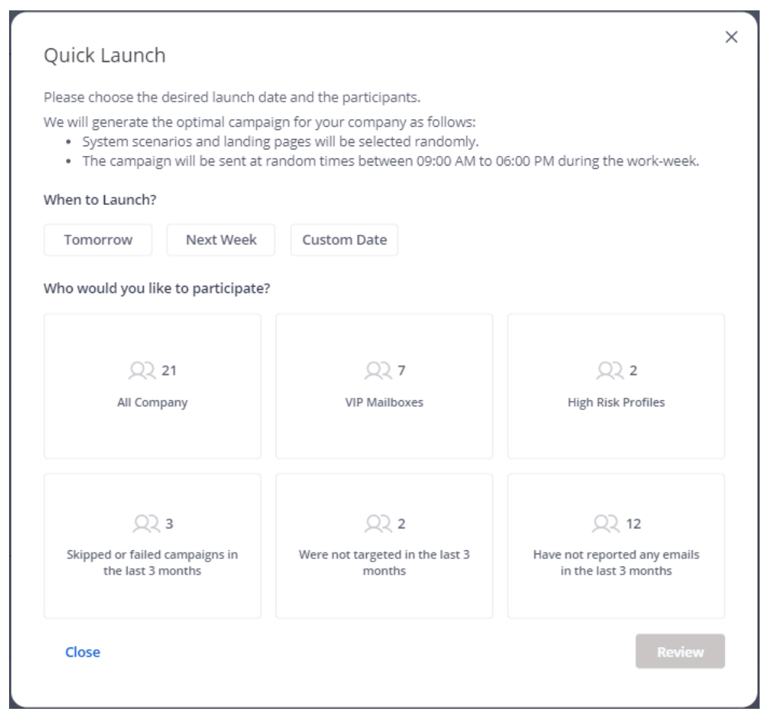
The Quick Launch menu
Quick Launch is designed for ease, flexibility, and targeted simulations, allowing for frequent and varied phishing tests with just a few clicks.
Setting up a campaign
Organizations that want finer control over their phishing simulation campaigns can configure them by clicking Simulation & Training > My Campaigns > Simulation. Fill in the information required in this screen with the results from the “Setting the stage” section above.
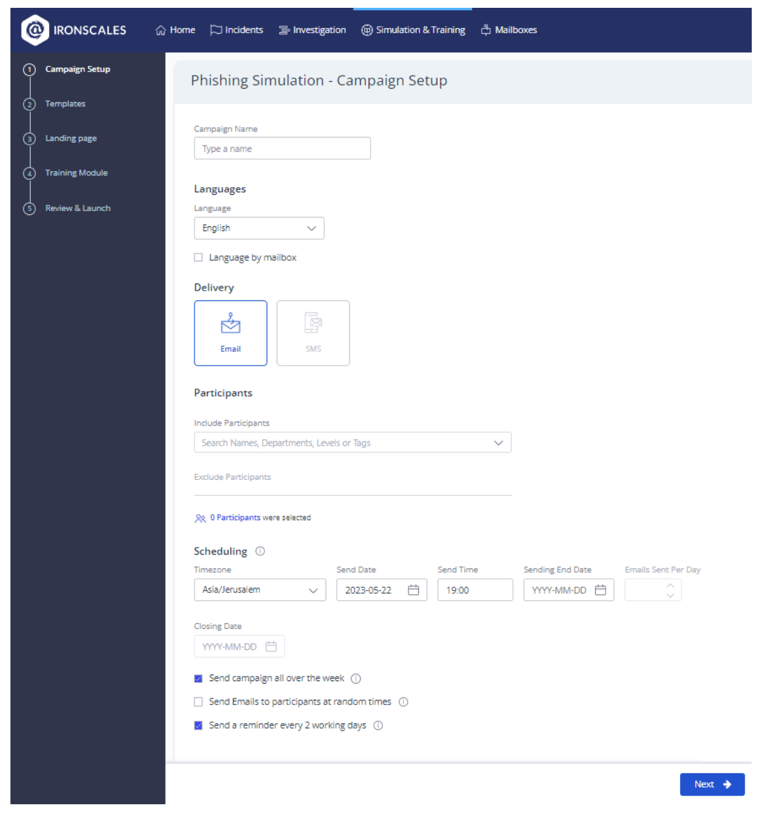
Setting up a phishing simulation with Ironscales
Selecting phishing email templates
The IRONSCALES platform provides phishing email templates across various difficulty levels—beginner, intermediate, and advanced—to match employee awareness. Beginners start with basic, common phishing scenarios; intermediates progress to more complex social engineering techniques; and advanced users tackle targeted spear-phishing and BEC simulations. Select templates that align with your organization’s security posture to ensure an appropriate level of challenge.
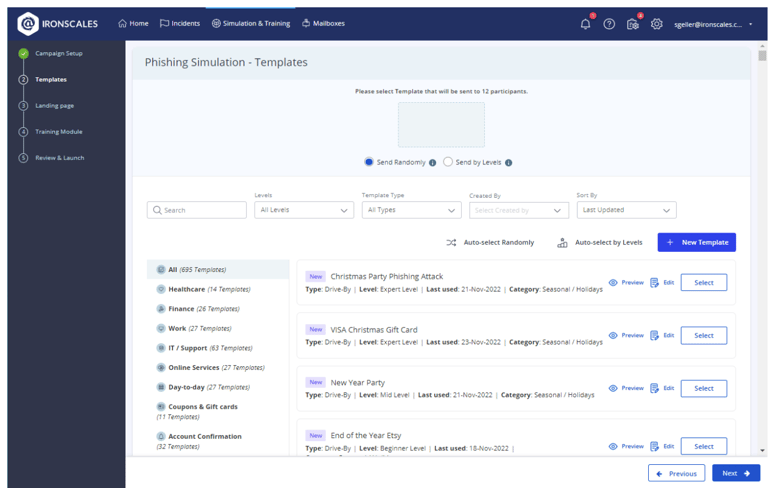
Template selection
Choosing a landing page
Selecting the right landing page for a phishing simulation is key. It not only gives instant feedback to users about clicking on a mock phishing link but also educates them on the warning signs they overlooked. Additionally, it can present further learning materials. Tailoring this page to the simulation’s context amplifies its educational impact.
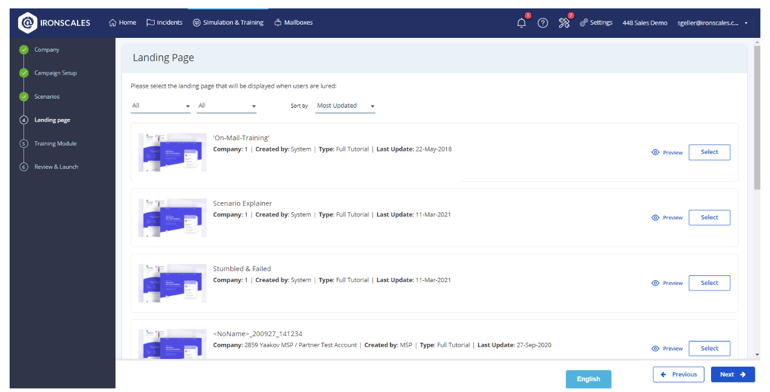
Landing page selection
Integrating training modules
IRONSCALES enhances phishing simulations by including training modules. These can operate immediately, taking users to a training module upon interacting with a simulation email, or as a follow-up, delivering educational content after the simulation for reinforcement. Access to IRONSCALES vast training library ensures that employees learn to identify phishing threats and apply best practices in response.
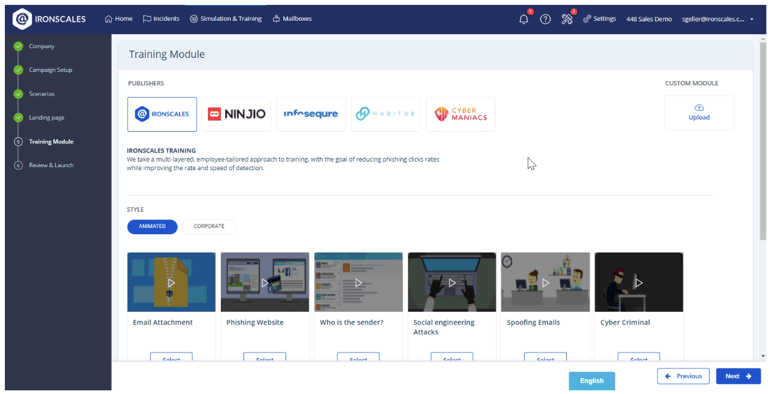
Training module selection
Campaign test: running a pilot simulation
Before deploying a campaign across the organization, it’s prudent to conduct a pilot test with a controlled group. This serves several functions:
- Training verification: It confirms that the linked training modules are functioning and accessible, as intended.
- Metric accuracy: It validates the clarity and accuracy of the campaign’s reporting metrics.
- Adjustments: Based on the feedback and the results, necessary adjustments can be made to improve the campaign’s effectiveness.
Campaign execution
Once the campaign has been set up and tested, it can be executed with the target groups by clicking Launch. IRONSCALES enables real-time monitoring, allowing you to gather immediate insights and metrics on the My Campaigns page. This visibility is crucial for gauging the campaign’s impact and making necessary adjustments.
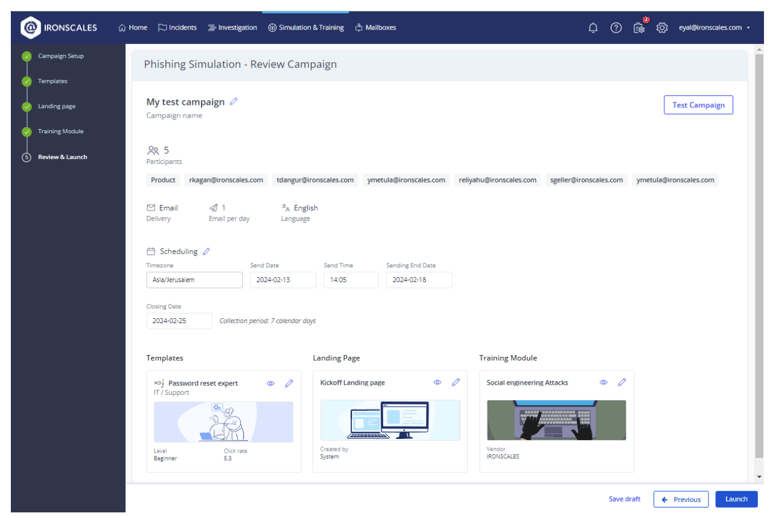
Reviewing and launching a campaign
Enhancing phishing awareness training
As phishing attacks become more complex, ongoing education is essential for a robust defense. IRONSCALES provides a wealth of training materials and structured training schedules to bolster your team’s preparedness against these evolving threats.
Tapping into the IRONSCALES library of training content
The IRONSCALES library is a rich, comprehensive repository tailored to diverse learning needs that extends across various publishers known for their compelling video content. With the library, training becomes an engaging experience, drawing from NINJIO’s anime-style cybersecurity episodes, Infosequre’s behavior-changing narratives, and Wizer’s extensive video collection on security awareness, compliance, and company culture.
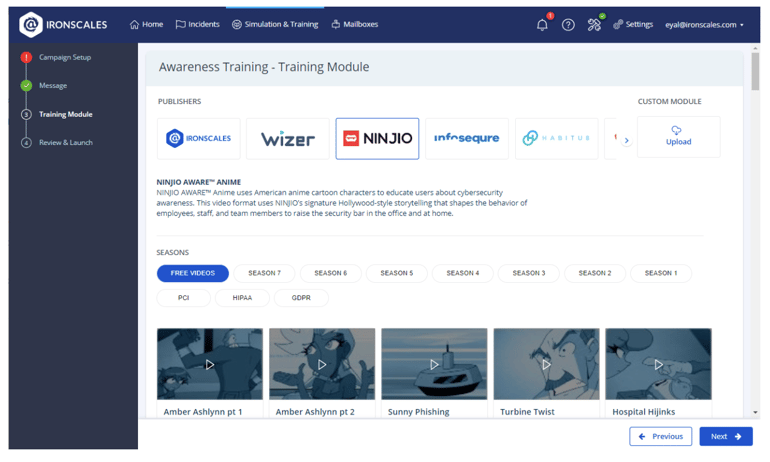
IRONSCALES training modules
Crafting a consistent training schedule
Consistency is the key to building security competence. The IRONSCALES platform streamlines the creation of regular, targeted training that keeps teams alert. For a new security awareness training campaign, follow these steps:
- Setup: Assign a campaign name and language, utilizing auto-translation for diverse teams.
- Participants: Choose your audience by department, location, or security awareness level.
- Timing: Schedule the frequency and timing of campaigns to ensure ongoing vigilance.
- Content: Select impactful video content from IRONSCALES’ libraries or your own material.
- Engagement: Personalize the campaign’s delivery email to boost engagement.
- Follow-up: Implement reminders to encourage consistent training participation.
- Review: Test your campaign before launching to confirm smooth execution.
The platform enables the crafting of phishing awareness training that’s engaging and retentive, turning routine exercises into a resonant learning journey.
Evaluating the phishing attack simulation results
IRONSCALES analytics platform offers a robust mechanism to dissect the results of phishing simulations, revealing critical insights into employee behavior and the effectiveness of prior training.
Analytics to evaluate training effectiveness
Begin evaluating your phishing campaign by accessing the campaign results via Simulation & Training > Campaigns, then clicking View. This section enables a detailed analysis across different organizational segments, providing insights into department-specific performances.
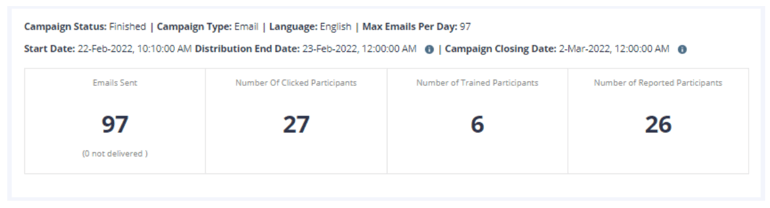
Focus on these crucial metrics:
- Number of Clicked Participants: Measures the propensity to click on suspect links or attachments
- Number of Trained Participants: Gauges interaction with provided training materials
- Number of Reported Participants: Indicates the level of alertness in spotting and reporting phishing attempts
The Attack Readiness Indicators report is crucial for assessing response effectiveness.

It includes the following:
- First Report: The time from the campaign’s start to the first filed report
- Mitigation Time: How long it took to initiate an automated response to a suspected attack
- Lured Before Mitigation: The count of users interacting with the campaign before the automatic response was triggered
- Reports to Mitigate: The number of reports needed to start the automated remediation process
These indicators are instrumental in measuring how prepared an organization is to handle a real phishing threat.
Further targeted training campaigns
By analyzing the Campaign Summary and Simulation Assessment reports, organizations can pinpoint specific areas where employees are most vulnerable. For instance, if the Number of Clicked Participants figure is high, this suggests a need for more focused training on identifying suspicious links and email content.
The Campaign Participants report aids in customizing training by revealing patterns in individual behaviors, highlighting those needing further education. Utilizing the Last 5 Results to identify those needing additional training and the Resend Training feature ensures that employees receive the necessary follow-up training to stay current with security protocols.
Exporting results and reporting
IRONSCALES enables the exporting of campaign data for in-depth review and sharing. With the Export Campaign feature, you can download a zip file containing participant responses, summaries, and detailed reports for documentation or stakeholder review. Utilize the Share function to disseminate campaign analytics directly to relevant parties within the organization.
Additionally, the Campaign Participants report can be exported as a CSV file, providing essential data for in-depth analysis and presentations. This functionality is integral to refining cybersecurity training programs, ensuring that continuous improvement aligns with organizational security goals and equips employees to counter phishing threats effectively.
Continuous improvement
In the rapidly changing cyber-threat landscape, organizations must continuously refine their phishing defense strategies to stay ahead. This means not only responding to current threats but also anticipating and preparing for future ones. IRONSCALES’ Autonomous Campaigns for Complete Protect (Beta) facilitates this by providing monthly campaigns with minimal setup, based on the latest phishing tactics, so teams can focus on up-to-date defense training.
Adapting phishing simulation strategies
Autonomous campaigns ensure that your defenses remain robust by reflecting the latest threats. IRONSCALES Campaign of the Month automatically aligns with the newest phishing patterns, offering the latest insights with no configuration needed.
Implementing autonomous campaigns
- Campaign of the Month: Embrace curated monthly campaigns to test against current threats.
- Review results: Post-campaign, you will receive a detailed analysis to highlight areas for improvement.
- Continuous learning: Use these insights for regular team learning, evolving your defense with each campaign.
For implementation:
- On the Campaign Management page, select Autonomous simulation.
- Set the campaign schedule, and customize the participant list.
- Submit to launch the campaign, which begins at the start of the month for a 14-day period.

Autonomous campaign simulation
Cultivating awareness and learning
A vigilant team is crucial, and a security-conscious culture is fostered through regular updates, training, and discussions. Autonomous campaigns support this by providing a steady flow of simulations that keep your team alert and informed.
Conclusion
Phishing simulations and ongoing training are critical parts of the cyber defense arsenal. This article has highlighted the imperative of proactive strategies, leveraging a comprehensive suite for realistic simulations coupled with robust training, and threat protection.
We encourage you to embrace this iterative approach to keep pace with the ever-evolving phishing threats and further explore how IRONSCALES can fortify your organization’s email security, ensuring that you’re not just preparing for today’s cyber challenges but also future-proofing against tomorrow’s threats.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)



















