Anti phishing training best practices
Phishing remains one of the most persistent and effective attack vectors putting organizations at risk daily. According to IBM's 2024 Cost of a Data Breach Report, phishing-related breaches now cost organizations an average of $4.88 million, making it one of the most expensive initial attack vectors. The threat continues to escalate: phishing attacks have surged 180% in 2025 compared to 2023, with AI-powered tools enabling attackers to craft more convincing and personalized campaigns at scale.
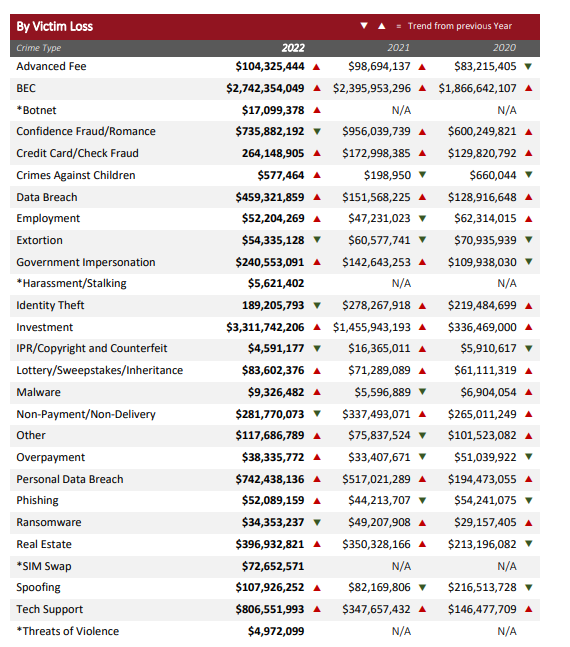
FBI report 2024: Increasing rate of phishing attacks and associated costs (source)
According to the FBI's 2024 Internet Crime Complaint Center Report, phishing accounts for 16% of all data breaches and remains a primary entry point for more severe attacks including ransomware and business email compromise.
While most companies conduct anti-phishing training for employees, it often becomes a tick-the-box, annual exercise that does not create lasting behavioral change. A high-quality, continuous training program is essential to prevent employees from falling victim to increasingly sophisticated phishing tactics. This article discusses seven best practices to make anti-phishing training more effective, along with common training mistakes and tips to avoid them.
Anti-phishing training best practices
The table below summarizes seven best practices to remember when organizing anti-phishing training.
| Best practice |
Description |
|
Conduct the training periodically
|
Regular anti-phishing training increases employees' understanding and keeps phishing awareness high.
|
| Use real-life examples |
Up-to-date examples reflect recent phishing trends and ensure employees are not learning outdated content. |
| Include third-party entities |
Apart from employees, contractors or service providers with access to your company's systems are a security risk and require training. |
| Organize interactive training |
Hands-on modules that engage students in answering quizzes, dragging & dropping answers, etc., increase knowledge retention. |
| Include tailored examples |
Industry-specific examples help against targeted phishing emails. |
| Emphasize compliance and accountability |
Compulsory anti-phishing training increases employee accountability if they continuously fall victim to phishing attacks.
|
| Gather feedback and improve |
Continuous improvement based on participant feedback ensures training remains effective and relevant.
|
In the following sections, we cover the best practices and their importance for anti-phishing training success in detail, helping reduce the risk of successful phishing attacks.
Conduct the training periodically
Humans are forgetful by nature, and only by frequent repetition can we increase the chance that information remains in memory. It is also important to consider new employees who might join the company after training sessions. If anti-phishing training happens once every few years, new employees risk becoming victims of phishing attacks. Finally, phishing tactics change rapidly—especially with AI-powered attacks evolving at unprecedented speed—making re-training with updated content essential.
Organizing frequent phishing tests and training can be resource-intensive and demanding for your organization. Consider service providers that specialize in such training and reduce the workload of your internal IT staff.
Use real-life examples
While the concept of phishing remains consistent, attackers continuously develop new techniques and leverage emerging technologies. In the past 2 years, the phishing landscape has fundamentally changed with the weaponization of artificial intelligence:
AI-Generated Phishing: Attacks have surged 1,265% since 2023, with AI tools enabling attackers to craft grammatically perfect, highly personalized messages at scale. AI can now generate convincing phishing campaigns in minutes that previously took human attackers 16 hours to create.
Deepfake Attacks: In February 2024, a finance worker at multinational engineering firm Arup transferred $25 million to fraudsters after attending a video conference call where the CFO and senior executives were all AI-generated deepfakes. Voice cloning technology now requires only 3 seconds of audio from earnings calls or podcasts to replicate executive voices with chilling accuracy.
Multi-Channel Campaigns: Modern attacks combine email, SMS, voice calls, and video to create layered deceptions. An initial phishing email establishes context, followed by a deepfake voice call from a "CFO" referencing that email to authorize wire transfers.
QR Code Phishing (Quishing): QR code-based attacks surged 25% year-over-year in 2024, with attackers embedding malicious QR codes in emails that bypass traditional email security filters.
Cryptocurrency Scams: "Pig butchering" investment scams increased 183%, with losses reaching $2.57 billion in 2024 as attackers build trust over weeks before directing victims to fraudulent cryptocurrency platforms.
Real-life examples and current trends improve employees' ability to identify attacks in context. It is crucial that anti-phishing training covers the latest attack vectors including AI-generated content, deepfake impersonations, multi-channel attacks, and cryptocurrency scams to ensure employees can recognize modern threats.
Include third-party entities
Although often forgotten, third-party entities such as contractors or service providers are essential to your anti-phishing strategy. Since such entities often have access to your company's data or manage your systems, a successful phishing attack against them can devastate your organization.
For example, consider an IT service provider that manages your IT infrastructure. Its employees have administrative access to your IT infrastructure, including critical servers, as part of their job. If one of these employees falls victim to credential phishing, an attacker gains administrative privileges in your infrastructure, giving them the keys to the kingdom. That is why including third-party entities (and demanding it) in your anti-phishing training is vital for the success of anti-phishing defense.

Organize interactive training
Interactivity includes training modules that ask users to actively participate via clicking, answer quizzes, drag & drop answers, ask questions, and so on. While it might sound unnecessary, making anti-phishing training more interactive has several benefits:
- Participants must be attentive and actively interact with the content instead of passively listening.
- Increases the chance that employees read and understand the content and not only attend because it is mandatory.
- It makes the training session more enjoyable.
Studies show that higher interactivity in content increases recognition and memory recall of the interactive content. It helps participants remember the content long after the training session. This is especially critical for recognizing AI-generated phishing and deepfake attacks, where employees must actively question seemingly authentic communications rather than passively accepting them.
Include tailored examples
Aside from general phishing examples, anti-phishing training should include phishing examples that relate to the industry in which your company operates. Such attacks are less common but more dangerous. They are tailored to your company, and attackers spend more time and effort crafting them, increasing the likelihood of success. For example, assuming your company operates in the pharmaceutical industry, attackers might craft phishing emails that aim for research & development plans, secret formulas, and customer data instead of standard PayPal credentials.
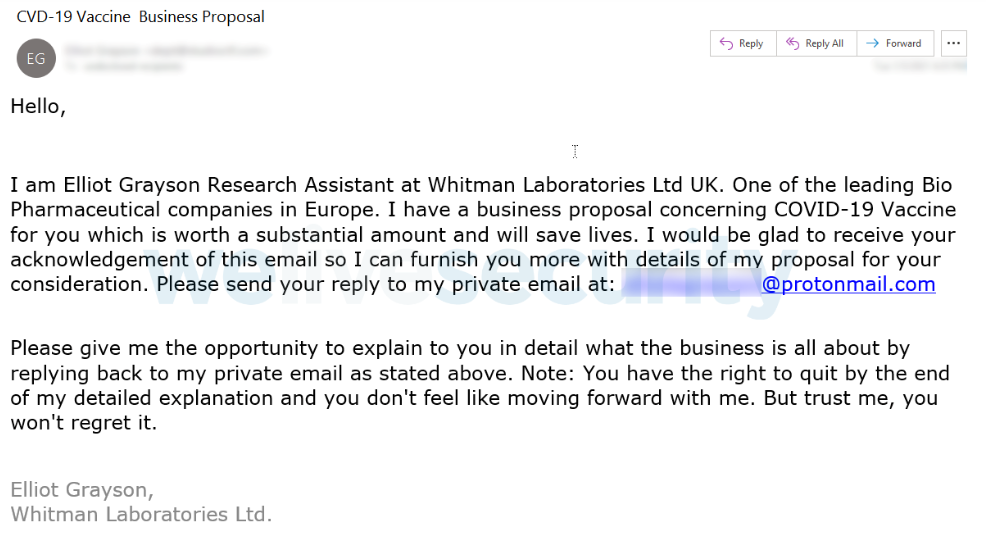
Example of a phishing email tailored to the pharmaceutical industry (source)
Additionally, include phishing examples for different departments that attend the anti-phishing training. For example, the type of email employees in the finance department receive often differs from phishing emails that Human Resources (HR) receives. Attackers trick the finance team into making large money transfers while they impersonate job applicants for the HR team.
Attackers are increasingly use AI to conduct reconnaissance on specific roles, scraping LinkedIn profiles and company websites to craft highly personalized attacks. Finance teams now face deepfake CFO calls, while HR teams encounter AI-generated candidate profiles with fabricated credentials.
While it is impossible to cover every scenario, try to cover and test examples tailored to the business your company does and your company's most important departments.
Emphasize compliance and accountability
While most understand the necessity of security training and comply with it, there will always be employees who are negligent and do not attend such training regularly, if at all. Your company should clarify that failing to participate in anti-phishing training is subject to consequences.
Additionally, employees should be encouraged to report phishing emails or incidents, even if they fall victim to the attack. While mistakes happen, recognizing them and reporting them in due time can help the IT security team respond to the attack faster or contain the damage in time. Otherwise, it should be mentioned that not complying with the security best practices or repeatedly not reporting phishing incidents will make employees accountable for their negligence.
In the era of AI-generated phishing and deepfake attacks, the emphasis should shift from "spotting the fake" to "verifying every request through alternate channels." Even the most authentic-looking video call or voice message should trigger verification protocols, especially for financial transactions or sensitive data requests.

Gather feedback and improve
At the end of each anti-phishing training, ask the participants for their feedback on the training session. While we can ensure that we use real-life examples and explain phishing in detail, the audience should also be considered.
For example, explaining phishing to employees in the financial department at a technical level is more challenging than explaining it to a cybersecurity analyst. Different groups of employees should be considered, and the training material should be understandable to everyone. You can ask participants about elements such as:
- Clarity — was it too complex?
- Length — was it too long?
- Quality of the material — was the material helpful?
- Understanding — do you feel more knowledgeable about phishing after the training?
- Relevance — did the training cover threats you might actually encounter, including AI-generated attacks and deepfakes?
It helps improve future iterations of the phishing training.
Common anti-phishing training mistakes
While the above seven best practices might sound straightforward, practice has shown that mistakes can still happen, reducing the success rate of the anti-phishing training strategy. For example, three popular mistakes that companies usually make when organizing anti-phishing training are:
Outdated content and examples
Although phishing attacks have existed for decades, they constantly evolve across different channels (email, SMS, voice, video) and leverage current events and emerging technologies. Attackers quickly exploit major global developments—from geopolitical conflicts to technological breakthroughs like generative AI—to craft convincing lures.
Threat actors have now weaponized AI tools to generate deepfake videos and voices, create perfect grammar in multiple languages, and personalize attacks at unprecedented scale. The FBI has issued warnings that AI now greatly increases the speed, scale, and automation of phishing schemes. According to recent threat intelligence, 73.8% of phishing emails in 2024 used some form of AI assistance, rising to over 90% for polymorphic attacks that continuously change to evade detection.
Anti-phishing training content must evolve alongside these emerging threats, incorporating examples of:
- AI-generated phishing with perfect grammar and context
- Deepfake voice and video impersonations of executives
- Multi-channel attacks combining email, SMS, voice, and video
- Cryptocurrency investment scams and "pig butchering" schemes
- QR code phishing that bypasses email filters
- Real-time social engineering using AI chatbots
Historical examples (such as the COVID-19 pandemic exploitation or the Ukraine conflict) remain relevant as teaching cases, but must be supplemented with current attack vectors to ensure employees remain up-to-date and less prone to falling victim to modern phishing schemes.
Making anti-phishing training optional
Your company should emphasize that anti-phishing training is important for the company's success and that everyone must attend such training. Managers or C-level staff often claim they need more time for such training, and companies often ignore their absence in security training. This can be dangerous as it takes a single non-security-aware employee to put the entire company at risk, regardless of their position in the company!
Executives are particularly valuable targets for deepfake and AI-powered spear-phishing attacks, making their participation in training even more critical year after year.
Not testing after anti-phishing training
Even if anti-phishing training is mandatory, employees may scroll through the content or stay on the phone without paying attention to the training. By demanding a final test at the end of each training, there is a better chance that employees study and learn the material in depth.
Additionally, you can hold phishing simulations and test the results of the anti-phishing training in real-life attack simulations. Modern simulation platforms should include AI-generated attacks, deepfake scenarios, and multi-channel campaigns to properly prepare employees for current threats. You can then have a clear overview of the employees who fell victim to the test and require follow-up anti-phishing training.
One-click phishing campaign setup with IronScales (source)
Conclusion
With phishing attacks rising in volume and sophistication—particularly AI-powered and deepfake-enabled threats—preparing your employees through comprehensive anti-phishing training is increasingly critical. In this article, we covered best practices when conducting anti-phishing training, such as repeating tests periodically, using current real-life examples including AI-generated attacks, making training interactive, and incorporating modern threat vectors like deepfakes and multi-channel campaigns. We also looked into common mistakes when conducting such training and how to avoid them.
Although there is no perfect solution to the phishing problem, preparing your employees with up-to-date training on evolving attack techniques ensures you raise the bar and make it significantly more difficult for attackers to be successful. The key in today's threat landscape is teaching employees to verify every request through alternate channels, regardless of how authentic it appears—whether it's a perfectly written email, a voice call that sounds like your CEO, or a video conference with executives.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)








