Benefits of phishing education for employees
Email filters and security tools block most phishing attempts, but some always get through. When that happens, employees become the last line of defense. Organizations that invest in phishing education see measurable improvements: Verizon's 2025 Data Breach Investigations Report found that 20% of users successfully recognize and report phishing simulations after training, with 11% reporting even after initially clicking—demonstrating that education builds resilience even when mistakes happen.
The benefits extend beyond detection rates. Effective phishing education reduces incident response costs, accelerates threat containment, improves security culture, and transforms employees from vulnerabilities into active defenders. With the human element involved in 60% of data breaches, employee education delivers one of the highest ROI security investments organizations can make.
This chapter outlines the key benefits of phishing education for employees and provides a framework for implementing an effective program that drives measurable behavioral change and risk reduction.
Summary of key concepts in phishing education for employees
| Key Concept |
Description |
|
Benefits of phishing education.
|
- Identification skills
- Critical thinking
- Risk mitigation
- Cultural transformation
|
| Elements of an effective phishing education program. |
- Comprehensive training modules
- Phishing simulation tests
- Real-world examples and case studies
- Continuous updates and testing
- Tailoring for your organization
|
| Critical topics in phishing education. |
Employee phishing education should include URL phishing, attachment phishing, and spear phishing. |
| Measuring the success of your phishing education program. |
Measure the effectiveness of your phishing training program by tracking key performance indicators such as
- The failure rate in phishing simulation tests.
- Amount of phishing reports.
- Phishing incident rates.
- Employee feedback and surveys.
|
| Promote a cybersecurity culture. |
Encourage employees to take cybersecurity personally. Emphasize the importance of detecting and reporting phishing emails in time. |
Critical topics in phishing education for employees
Although phishing attacks come in various forms, your phishing education program must cover the top three most concerning types of attacks.
#1 URL Phishing
URL phishing, or link phishing, is an attack where cybercriminals send victims deceptive emails, messages, or social media posts containing malicious links. Once on these fraudulent sites, victims may be prompted to enter sensitive information such as usernames, passwords, credit card numbers, or other personal data—all under the deception that the fraudulent site is legitimate.
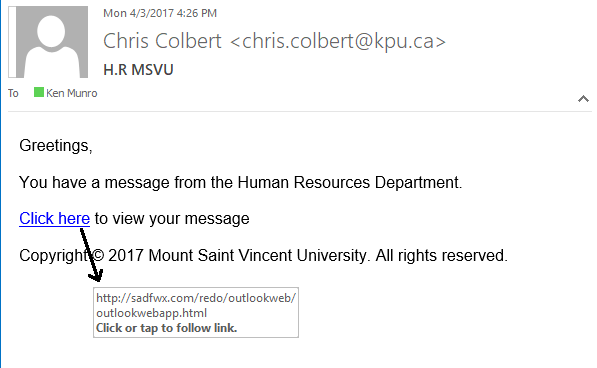
Example of a URL Phishing email (source)
#2 Attachment phishing
In this type of attack, malicious actors attach harmful or infected files, such as infected documents or ransomware, to seemingly innocent-looking emails. The malicious actor aims to get the victim to open the attachment. Often, these emails are crafted to create a sense of urgency or importance, luring the recipient into opening the attachment without thinking twice.
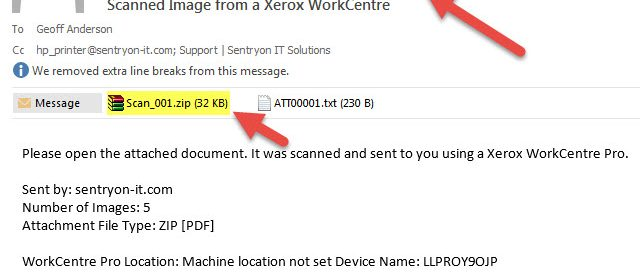
Example of a Spear Phishing email (source)
#3 Spear phishing
Unlike broader phishing attempts, spear phishing is a highly targeted attack focusing on a specific individual or organization. The attackers invest time in researching their targets. Armed with this knowledge, they craft compelling emails, often with the aid of AI tools like ChatGPT, that appear to come from trusted sources, like colleagues, superiors, or reputable companies.
Business Email Compromise (BEC) attacks take the concept of spear phishing a step further. BEC attacks focus on crafting emails that appear to come from trusted sources—going so far as to imitate their communication styles and patterns. The goal is no longer to get the victim to click on a link or open an attachment but to have the victim complete tasks such as fund transfers, changes to payment details, or providing confidential information.
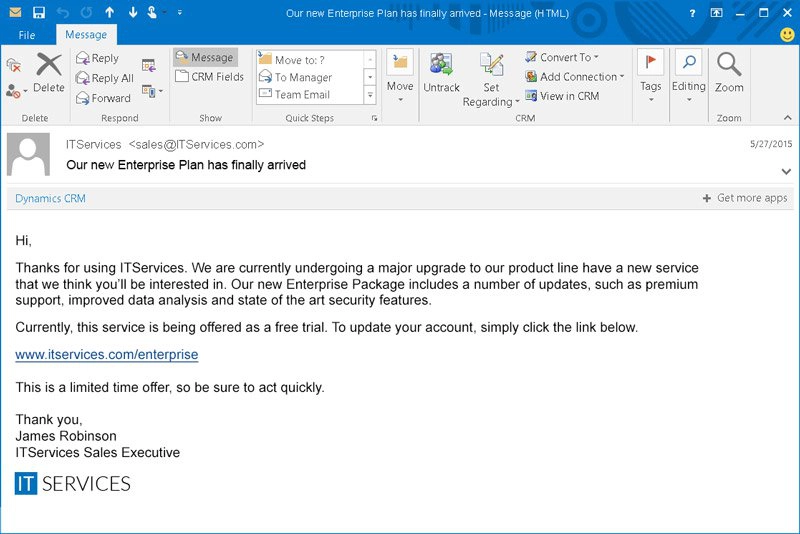
Example of a Spear Phishing email (source)
Key considerations for implementing effective phishing education for employees
Successful phishing education programs share five common elements that drive measurable behavior change.
#1 Comprehensive training modules
The foundation of any successful phishing education program lies in comprehensive training modules. The modules should provide insights into the psychology behind various phishing attacks. You should prioritize explaining how cybercriminals manipulate human behavior to gain access to sensitive information and how employees can detect and thwart the attacks. By delving into the nuances of phishing tactics, participants gain a holistic understanding of the threat landscape.
An alternative to creating your own phishing education program is to use a service that can provide one for your organization and update it as the landscape changes. Using a service enables your organization to leverage top-tier phishing education without creating and maintaining it yourself.
#2 Customized programs for different teams
Remember that not all participants have the same level of familiarity with cybersecurity concepts. Tailor your program to accommodate different roles and levels of technical expertise within the organization. While technical teams benefit from deeper dives into the technical aspects of phishing, non-technical employees require more straightforward explanations and practical tips.

#3 Phishing simulation tests
Engagement is critical to effective learning. Incorporating interactive elements into your training program keeps participants actively involved. Simulated phishing tests should present participants with real-world examples, allowing them to apply their knowledge in a controlled environment. These experiences enhance retention and ensure participants use the theory in practice.
While phishing simulation testing takes time and effort to organize, some companies provide phishing simulation services. These services enable your organization to run phishing simulation tests without having to spend the time crafting the emails, adding exceptions to your upstream SEG, or tabulating the results yourself.
#4 Real-world examples and case studies
Real-world examples and case studies provide context to the theoretical concepts covered in the training. Sharing actual phishing emails, websites, and scenarios that organizations have encountered helps participants recognize the subtleties of phishing attempts. By dissecting these examples, participants gain practical insights into how attackers craft convincing messages and manipulate recipients.
Example of the variety of training material provided by IRONSCALES (source)
#5 Continuous updates and testing
The digital landscape is constantly evolving, and so are phishing tactics. An effective phishing education program for employees is not a one-time event; it's an ongoing process that evolves alongside the threat landscape.
Regularly update the training modules to reflect the latest phishing trends, new attack vectors, and emerging best practices. Engage participants through ongoing communication channels, newsletters, and workshops to reinforce the importance of vigilance.
Common mistakes when implementing a phishing education program
Unfortunately, there are common pitfalls that organizations often need help with when implementing a phishing education initiative. Steering clear of these missteps is crucial for ensuring your program's effectiveness and long-term impact. Here are five common mistakes to avoid,
Failure to obtain management support
The success of a phishing education starts with buy-in and endorsement from top-level management. It's difficult to achieve success without leadership helping to foster a culture of cybersecurity and projecting support when encountering bumps in the road.
Generic and irrelevant training content
One size does not fit all when it comes to phishing education. You can reduce effectiveness and create disinterest and a false sense of security if you use generic training content that does not:
- Resonate with your staff
- Address specific job roles
- Mirror evolving tactics of cybercriminals
Tailor the training content for different departments and roles and regularly update your training material to reflect the latest phishing trends and attacks.
Lack of continuous training
There must be more than one training session to create a resilient workforce. Cyber threats are dynamic and ever-changing, and education should follow suit. Continuous training reinforces knowledge, adapts to emerging threats, and keeps the topic of cybersecurity at the forefront of employees' minds. To maintain vigilant and informed staff, consider integrating periodic refresher courses, phishing simulations, and awareness campaigns.
Neglecting simulation tests
Simulated phishing exercises provide a hands-on experience that bridges the gap between theory and practice. These simulations allow employees to apply their newfound knowledge in a controlled environment, honing their ability to detect phishing attempts. Simulations also offer valuable insights into areas needing improvement, helping you tailor your training efforts for maximum impact.
Implementing a punitive approach
A punitive approach to phishing failures fosters fear and reluctance among employees. Creating an environment where individuals feel safe reporting potential phishing incidents without fearing negative consequences is essential, especially if you want your security teams to investigate and quickly mitigate any potential harm.
Instead of focusing on punishment, emphasize learning and improvement. Encourage reporting, provide immediate feedback, and offer additional training to reinforce positive behavior rather than punishing negative behavior.
Measure the success of your phishing education program
The number of training sessions conducted doesn't just measure the success of a phishing education program; it's gauged by the tangible impact it has on an organization's cybersecurity posture. To ensure that your program is making a real difference, implement metrics that provide insights into its effectiveness.
By tracking key performance indicators and analyzing incident data, you can identify strengths, weaknesses, and areas for improvement within the program.
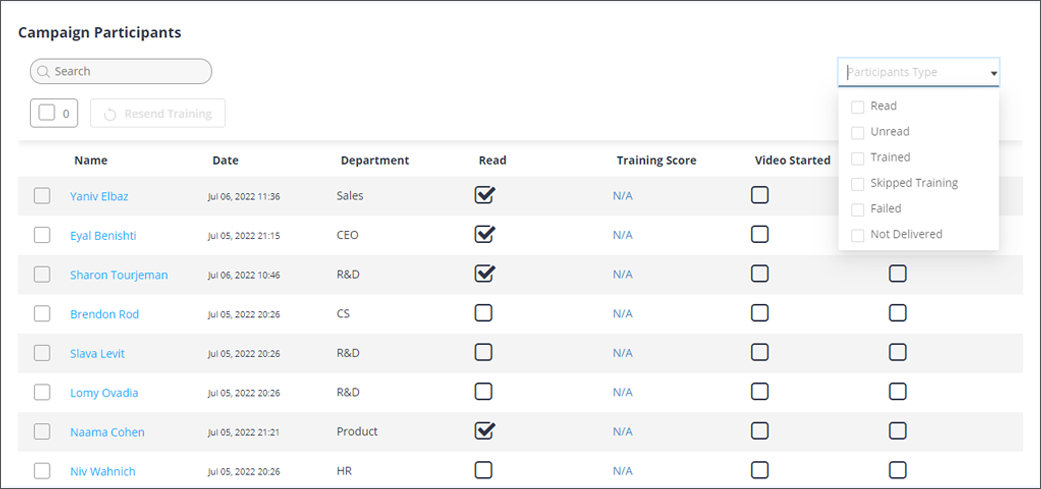
Tracking Phishing Awareness Training Engagement and Results in Ironscales (source)
Key performance indicators
Some key performance indicators to track include:
Rate of failures in phishing simulation tests
One of the most direct indicators of your program's impact is the rate of failures in phishing simulation tests. These tests mimic real-world phishing attempts and evaluate how well employees can identify and respond to them. A declining rate of failures over time signifies that your education efforts effectively enhance participants' ability to recognize phishing attempts.
Amount of phishing reports
Encouraging employees to report suspected phishing incidents is crucial. Track the rate of phishing reports submitted by employees during and after the training. An increase in reports might indicate that employees are becoming more vigilant and proactive in identifying potential threats. This also shows that they feel confident reporting incidents without fear of retribution.

Phishing incident rates
Measure the overall rate of successful phishing incidents over time. As your education program takes effect, you should observe a decrease in successful phishing attempts. This reduction signifies that the program is making a significant impact on minimizing the vulnerability of your organization to actual phishing attacks.
Employee feedback
In addition to quantitative metrics, gather qualitative feedback from participants. Conduct surveys to gauge their perception of the training's value, relevance, and practicality. This feedback provides insights into how participants perceive the training's impact on their daily responsibilities and their confidence in identifying phishing attempts.
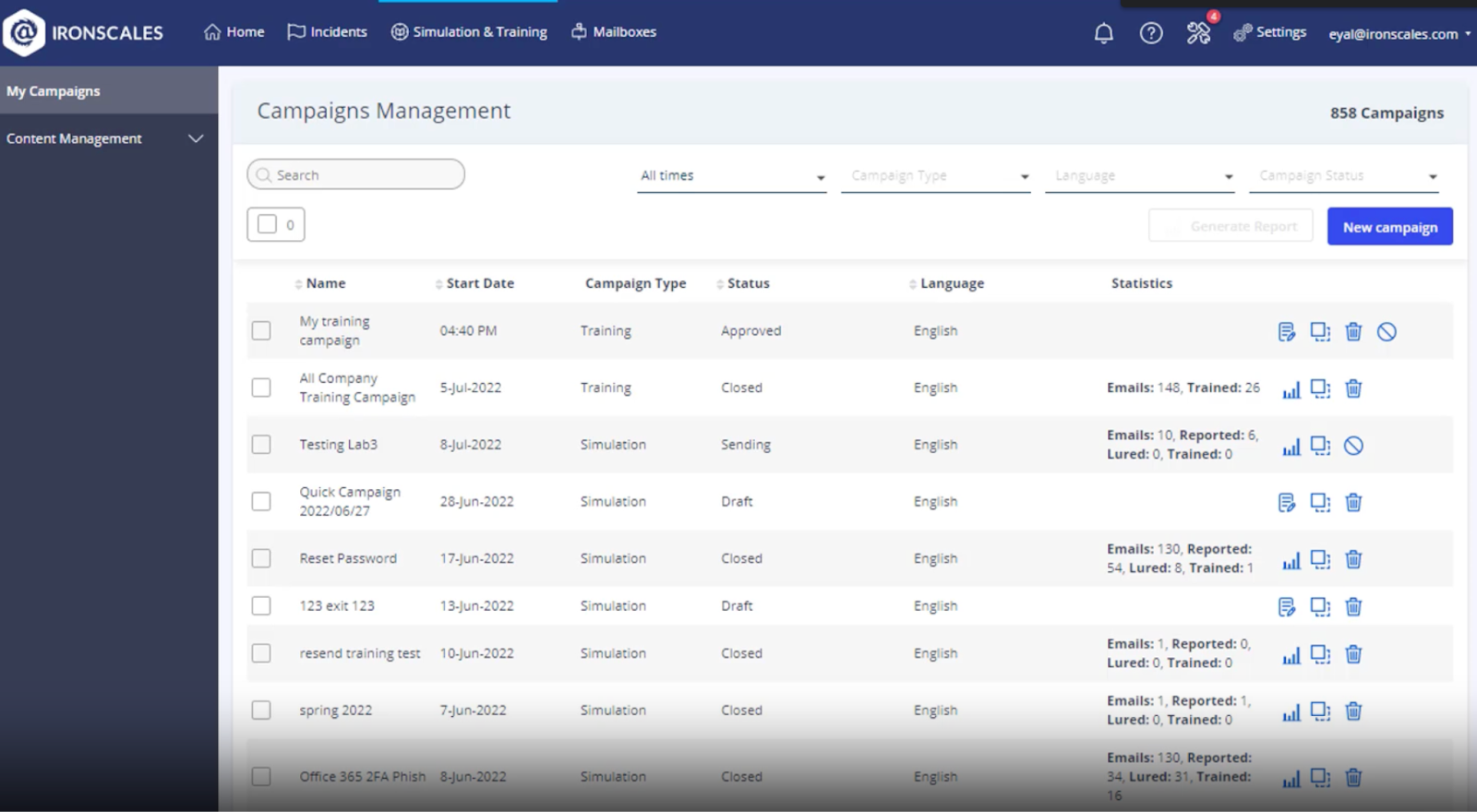
IRONSCALES phishing training and simulation results, showing emails sent, lured, and reported. (source)
Incident analysis and continuous improvement
The data collected from phishing tests, reports, and incidents form a valuable resource for refining your program. Analyze the incident data to identify trends, patterns, and areas of concern. For example:
- Are there specific departments or roles that consistently report higher failure rates?
- Are there particular types of phishing attempts that succeed more frequently?
- Are there specific challenges that employees consistently face?
By dissecting this data, you can tailor your program to address specific weaknesses and continually enhance its effectiveness. Regularly revisit your program's content and structure based on the insights from the collected metrics and feedback. Identify topics that need more in-depth coverage, introduce new content, and incorporate emerging threats into your updated training curriculum.
Promote a cybersecurity culture
In the battle against phishing attacks, knowledge is the most potent weapon. However, this knowledge must be consistently reinforced and applied to be genuinely effective. While one-time or infrequent training sessions temporarily boost awareness, the real impact is making phishing education an ongoing, integral part of an organization's culture.
Consider integrating cybersecurity into company values and encouraging employees to take personal responsibility for cybersecurity. Emphasize employee awareness and incentivize them to contribute to an organization’s cybersecurity by detecting and reporting phishing emails. Doing so makes employees more invested in the phishing education program’s success. Ultimately your organization’s cybersecurity becomes a collective responsibility that strengthens the organization's defenses from within.

Conclusion
In the dynamic landscape of cybersecurity, where threats evolve rapidly, it's often said that "employees are the weakest link in the cybersecurity chain." While this statement might sound harsh, it highlights a critical truth: human error and lack of awareness can unintentionally expose an organization's sensitive data and assets to malicious actors. While advanced technical security measures, like firewalls, encryption, and intrusion detection systems, help, they are not foolproof. Cybercriminals will exploit those lapses in employees' judgment that these systems may not detect to gain unauthorized access and launch damaging attacks.
However, there is hope—with the proper education, employees can become your first line of defense. An effective phishing education for employees includes engaging and interactive training, realistic simulations, and real-world examples. It is supported by continuous updates and a strong culture of cybersecurity measured through incident data analysis and relevant metrics.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)









