Clone phishing: anatomy of an attack
Clone phishing is a type of phishing attack where attackers aim to impersonate a trusted well-known company or entity by cloning their official website or emails. For example, many financial institutions, such as PayPal, use template emails to communicate with customers. Knowing that these templates rarely change in design or content, an attacker can clone an email's design, text, and other elements to craft a new malicious email impersonating a financial institution. The victim, being familiar with the email’s look and feel, is less likely to be suspicious and more likely to be tricked.
Such emails usually contain phishing links that lead to a cloned website of the impersonated companies. What makes this type of phishing particularly dangerous (as we will see in this article) is the existence of many free tools that attackers can use to clone the content of legitimate websites.
One of the largest clone phishing schemes happened in 2017, where attackers attempted to impersonate Google by sending fake Google Docs emails asking victims to log in to a fake Google page to access a shared document.
Summary of key best practices to defend against clone phishing
The table below summarizes the six best practices organizations can use to reduce their risk of falling victim to a clone phishing attack. We’ll explore these best practices in more detail later in this article.
| Best practice |
Description and benefits |
|
Configure/fine-tune email filtering security tools
|
Make use of built-in email filtering (e.g., YARA rules) capabilities of your tools to block emails before they even reach the victim.
|
| Activate anti-phishing email security protocols |
Ensure that your email security tools verify the email's legitimacy by using protocols such as Sender Policy Framework (SPF). |
| Deploy natural language understanding (NLU)-based AI tools |
Use NLU-based AI models to be able to analyze and "understand" the cloned text and its real nature. |
| Ensure a 4-eye principle for approving financial transactions |
Modify your policies to ensure that at least 2 employees are needed to approve high-amount financial transactions. |
| Enforce multi-factor authentication (MFA) |
Mitigate the danger of the credential leak by activating and enforcing MFA across your company. |
| Conduct security awareness training (SAT) and phishing simulations |
Train employees with examples of clone phishing emails and teach them what to look out for. Make use of phishing simulation to measure the results of the training process. |
Example of a clone phishing email
Before an attacker creates a clone phishing email, they must first find an email notification template commonly used by the company to be impersonated and clone its content. For example, let’s assume that an attacker wants to impersonate PayPal. The attacker can either register and open an account with PayPal or search the Internet (e.g., in forums) to learn how PayPal emails look. What makes this particularly easy is that most big companies rarely change their email notification templates. This consistency in email templates makes it easier for an attacker to use the same template to craft malicious emails over a long period of time.
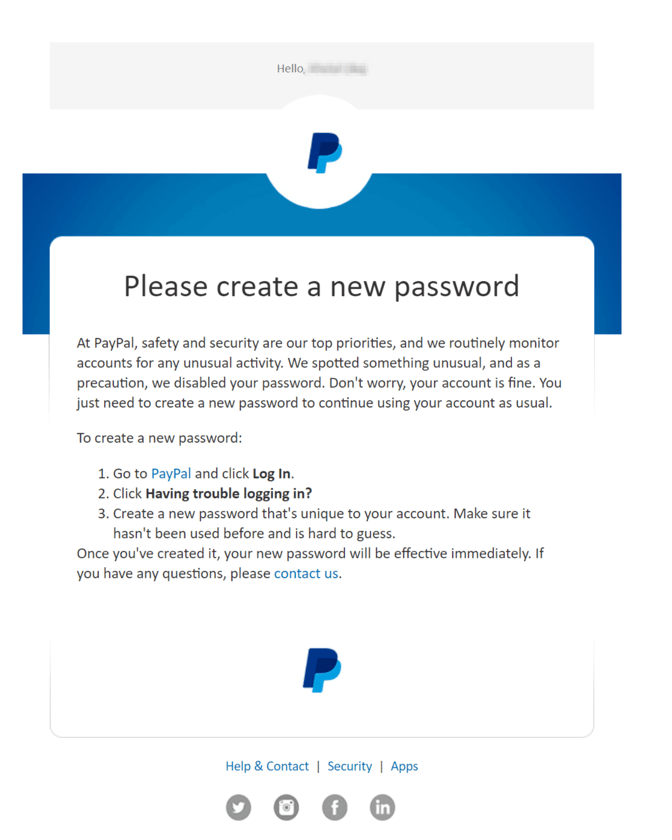
Example of a typical benign email from PayPal asking the customer to log in.
Once the attacker has a sample email from PayPal, they can either directly copy the text from the email or open the email headers and copy the HTML of the email content directly. Depending on the type of the email, this can either be plaintext HTML or base64-encoded HTML, which can be easily decoded with tools such as CyberChef.

Decoding base64-encoded HTML of PayPal's email with CyberChef.

The attacker can then replace the legitimate PayPal login link (marked in green above) with a link that leads to the attacker’s malicious website. The attacker can use various free tools such as HTTrack or Social Engineering Toolkit to clone PayPal's website.

Using HTTrack to clone the PayPal website.
Once the PayPal login website is cloned, the attacker can make minor changes to the cloned HTML of the login website so that the login credentials are now sent to the attacker’s server and not to PayPal. Then, they can host the malicious cloned website on the Internet and place the link to this malicious site on a cloned phishing email template.

Example of a cloned PayPal login site hosted on a malicious website. (Source)
Armed with a clone of a PayPal notification email with a malicious link, the attacker can send the phishing email to many victims and wait for them to enter their credentials on the malicious website controlled by the attacker.
Six essential best practices to defend against clone phishing
This section will cover six essential best practices your company can implement to defend itself against clone phishing attacks.
Configure/fine-tune email filtering security tools
While most companies use email gateways or mail transfer agents (MTAs) to receive emails, some might not be aware that these tools provide email filtering capabilities that are either disabled or have default configurations that might not fit the needs of your company. Therefore, security teams should review all the email filtering capabilities of their email tools and activate necessary disabled features or fine-tune the existing ones.
Some email security tools include the ability to write and apply custom email filtering rules, such as Yet Another Recursive Acronym (YARA) rules to filter out specific unwanted emails. For example, a primitive YARA rule to detect a phishing wave with cloned phishing emails impersonating PayPal could be:
rule Clone_Phishing
{
strings:
$string1 = "login"
$string2 = "immediately"
$string3 = "PayPal"
$string4 = "suspend"
$string5 = "account"
condition:
all of them
}
Note that some filters can be aggressive and even block benign emails with business impact. Make sure to test the configuration changes or start by running the blocking capabilities in audit mode to get a feeling of what is blocked and what not.

Activate anti-phishing email security protocols
Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), Domain-based Message Authentication, Reporting and Conformance (DMARC) are the three most crucial email security protocols to verify the legitimacy of an email. Almost all email security tools can enforce the verification of email’s origin via these three protocols; your company should ensure that they are activated and properly configured.
While SPF and DKIM ensure that the email sender is authorized to send the email on behalf of the sender domain (e.g., paypal.com), DMARC goes one step further and, depending on the DMARC record configured by PayPal, will report these impersonation attempts to PayPal so that they can take the appropriate measures and take down cloned malicious websites in time.
Note that these email security protocols are not bullet-proof solutions. Attackers can still register typosquatting domains that are look-alike domains that are very similar to the legitimate domain. Since attackers control a typosquatting domain and its DNS records, they can ensure that the SPF, DKIM, and DMARC verification is always successful. It will be up to user awareness and other best practices to ensure these cases are still detected and prevented.
Deploy NLU-based AI tools
While the typical phishing email might contain spelling or grammar errors that are easy to spot, in clone phishing emails, the content of the email is cloned from a legitimate email and rarely contains mistakes. This makes it harder for victims to recognize the phishing attempt since the email looks familiar and correctly written.
Using natural language processing (NLP)-based AI tools makes it possible to find inconsistencies in cloned emails that do not match legitimate emails, such as the login link leading to an unusual website. NLU-based AI tools have the advantage of “understanding” text and since they are trained with benign and malicious emails, they can spot differences that are hard to notice at first sight. More advanced email security solutions are supplied with continuous feeds to the learning engine of these AI tools with “fresh” clone phishing email trends reported by human experts worldwide. This ensures that the AI model is up-to-date with the most recent trends and benefits from the analysis or the verdict of the human experts who report such malicious emails.
Ensure a 4-eye principle for approving financial transactions
Although most clone phishing emails attempt to trick the victim into providing information such as login credentials, there are also clone phishing attacks where attackers impersonate a service provider or another entity that provides services to the target company. This has happened to Google and Facebook in 2019 where the hacker managed to steal over $100 million by impersonating a supplier and sending fraudulent invoices and emails to these two companies. Therefore, ensuring that at least two people verify critical or high-value financial transactions is essential because it reduces the risk of a single victim approving a fraudulent transaction.
Enforce MFA
Since the most common type of clone phishing email attempts to steal user credentials, enforcing multi-factor authentication (MFA) across your entire company is crucial. In the event of a successful phishing email, these credentials would not be enough to give the attacker an access point to your company. While MFA can come in many forms (SMS, phone call, Authenticator App, code per email, etc.), they might be prone to attacks. Consider using FIDO2 as one of the most secure MFA solutions out there.
Conduct security awareness training (SAT) & phishing simulations
As with all types of phishing, security awareness training (SAT) remains vital to reducing risk. While security tools will filter many malicious emails, attackers get more and more creative, and there is always a chance that a malicious email makes it through and reaches the victim’s mailbox. Training employees periodically is essential to protect your company, as employees are the last line of defense.
In addition to SAT, it is recommended to perform phishing simulation exercises. This way, you can test the effectiveness of your anti-phishing security tools and the results of the SAT. Finally, based on the output of the phishing simulation, you can improve your defenses and adjust SAT to train employees better. If setting up periodic SAT & phishing simulation exercises demands too many resources from your company, consider hiring service providers to assist you in every step of this process.

Summary
Clone phishing is a genuine threat to modern businesses. Attackers can access tools and tactics that streamline the process of conducting clone phishing attacks at scale. Fortunately, several mitigation techniques can help businesses reduce risk. A fundamental takeaway for organizations is that even though cloning legitimate emails makes malicious emails appear more credible, phishing will always remain phishing, so best practices and careful observation will always reveal its malicious intent.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)













