Guide to phishing awareness training
Phishing remains the dominant cyber threat, responsible for 16% of initial breach access points and contributing to the 60% of incidents involving human actions like clicking malicious links or responding to social engineering. With individual data breaches now averaging $4.88 million in losses, the human element represents one of the costliest vulnerabilities organizations face.
Phishing awareness training—delivered as security awareness training (SAT)—is the most effective defense against these human-targeted attacks. Modern SAT platforms combine interactive training, realistic phishing simulations, and behavioral analytics to help employees recognize and report threats before damage occurs.
This guide explains why phishing awareness training is essential and outlines the key elements of an effective SAT program. For detailed statistics and breach trends, see Verizon's 2025 Data Breach Investigations Report.
Summary of key phishing awareness training concepts
SAT is a powerful way to turn human resources into the frontline defense against phishing campaigns. However, conducting an effective SAT requires following phishing awareness training best practices. Whether you create your own SAT from scratch or rely on an existing commercial solution, you’ll want to ensure that your approach applies the best practices below.
| Best practice |
Description |
|
Tailor training to your threat model
|
Generic training is not helpful. Training material should match what is currently being used by attacks and specific kinds of threats most pertinent to your company.
|
| Regularly conduct phishing awareness training |
Training should not be a one-off event. Periodically refreshing employees' phishing knowledge also ensures new team members are onboarded with up-to-date phishing awareness training. |
| Make use of phishing simulations |
Even the best threat models often crumble when tested by real adversaries. Phishing simulations allow you to find and harden weaknesses in your phishing defenses before threat actors can do the same. |
| Train employees to report threats |
Employees should be taught to recognize phishing emails and how to report to trigger an incident response process. Well-trained employees are less apprehensive about reporting emails they suspect are illegitimate and do so more competently. |
| Make it interactive |
Rather than only providing videos that employees may struggle to pay attention to, interactive training content is better at keeping employees interested and improves memorization and internalization of the conte |
| Deal with non-email phishing threats |
Email is not the only medium through which phishing attacks can occur. SMS (Smishing), phone calls (vishing), and other attack vectors exist. SAT should account for these varieties. |
How phishing awareness training protects organizations
IT teams seeking to mitigate security threats often focus on technical solutions. In the case of phishing, this will typically mean implementing a Secure Email Gateway (SEG) or integrated cloud email security (ICES) product to detect and block phishing emails. These security controls are a valuable component of an overall anti-phishing strategy. However, purely technical methods overlook the core characteristic of phishing that makes it work: exploiting human (rather than technical) weaknesses.
In other words, a holistic anti-phishing defense should go beyond merely hardening networks and systems, although these are also important. SAT offers precisely this: an approach for hardening human resources to identify, report, and ultimately thwart phishing threats.
In the subsections below, we’ll explore each of the best practices we alluded to in the summary, showing you how all of them contribute to the success of SAT.

Tailor training to your threat model
Cybersecurity is a broad domain with so many attack surfaces that could always be hardened just a little more. Realistically, you will have to prioritize specific attack vectors over others.
For example, if you run a small software development company, training employees to avoid Nigerian Prince scams is not the best investment of time and effort. Instead, you will want to teach them to be careful about installing untrusted packages from users claiming to have technical issues or running code snippets supplied by open source contributes that may be malicious.
SAT solutions often offer an immense variety of training materials tailored to different threats and hypothetical scenarios. You should select materials that most closely align with threats most relevant to your environment.’
Choosing an email security solution with a wide variety of SAT materials will make it much easier to tailor the content to your specific threat model and security needs.
 IRONSCALES’ solution offers a catalog of 1150+ Phishing Templates in 10+ Languages with accompanying reinforcement training modules. (Source)
IRONSCALES’ solution offers a catalog of 1150+ Phishing Templates in 10+ Languages with accompanying reinforcement training modules. (Source)
Regularly conduct phishing awareness training
Imagine a company that hopes to improve its capacity to thwart phishing campaigns. Consequently, the company purchases a high-quality, commercial SAT product and begins training employees. To ensure employees absorb the training material, they do a phishing simulation immediately afterward, and most employees perform well.
Months go by, and eventually, nearly a year later, a ransomware gang launches an actual attack against the company. However, most employees have forgotten the best practices they learned during training. Moreover, the company has hired dozens of new employees since then, none of whom were present for the training.
For optimal results, companies should do several phishing simulations each year. This leads to the highest rates of employee phishing reports and lower rates of false positive reports. Of course, how often to perform simulations and retraining depends on how high of a priority phishing awareness is for your company.
Anti phishing training is vastly cheaper than a successful ransomware attack or a data breach. The pros and cons should be weighed carefully, but at the very least, training must not be a one-time event.
Make use of phishing simulation testing
A simulated phishing attack enables you to assess how well your organization would resist a real phishing campaign. This is useful for two reasons:
- Find weaknesses in your anti-phishing defenses
- Assess how well your employees absorbed anti-phishing training
Often, a SAT product will offer an easy-to-use system for setting up and deploying a phishing simulation. For example, the solution pictured below provides a web panel for doing exactly this:
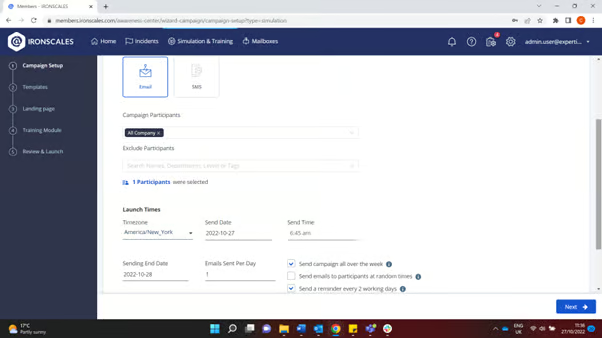
IRONSCALES web panel lets users easily manage phishing simulations. (Source)
The phishing campaign should be customizable depending on your specific security needs and should match the SAT content. For example, if you trained your employees against Business Email Compromise (BEC), you should be able to customize your phishing simulation toward that kind of attack.
Train employees to report threats
Training your team to be aware of phishing threats makes them less susceptible to falling for phishing attacks, and that’s one of the primary benefits of SAT. However, it is not the only benefit. Phishing-aware employees also learn to report phishing attempts to security personnel effectively.
SAT training should go hand-in-hand with empowering employees to detect and report phishing.
This approach effectively utilizes employees as an additional source of anti-phishing intelligence. Leveraging frontline intelligence from non-security employees aids the security team because the security team cannot detect or handle every phishing email that bypasses email security defenses. Some phishing mail will inevitably go unnoticed by your security tools, and employee reporting helps act as an additional layer of protection.

Make it interactive
Even the best training material can be useless if it is not presented in an engaging way. Forcing employees to watch several hours of videos and then testing them two weeks later is unlikely to bear desirable results.
There are various ways to make training more lively. One approach is to run a phishing simulation before the training, and then let everyone know that another simulation will occur after training. This makes the training more engaging because employees know what went wrong and can connect the training to their recent experience.
Finally, this approach gamifies SAT by encouraging teams to do their best at averting simulating phishing attempts and reporting them.
Deal with non-email phishing threats
Although email is still the dominant vector for phishing attacks, various other forms of phishing exist that don’t use email or combine it with some other attack medium. For example:
- Smishing uses SMS (text messages)
- Vishing attacks occur using voice calls
- Angler phishing poses as legitimate company social media resources
- Cryptocurrency scams use various methods to trick coin holders into giving up their private keys or other sensitive data
Some phishing variants can be difficult to replicate in a scalable way during phishing simulations, which is precisely what makes them so challenging to defend against. Nevertheless, it’s critical that your company can protect against threats, including ones that are hard to train for.
If voice-based attacks, smishing, etc., are relevant to your threat model, then you should ensure that your phishing awareness training accounts for non-email phishing attacks. These risks should be accounted for whether in simulations, in SAT material, or both.

Conclusion
In summary, a robust SAT program is the best way to provide phishing awareness training. Specifically, SAT should rely on the best practices mentioned above, such as periodic retraining and phishing simulations. Ideally, a single SAT solution should address all the concerns and best practices mentioned in this article.
Additionally, a SAT solution should employ cutting-edge methods like ISAT (Integrated Security Awareness Training), integrating employee reporting mechanisms directly into the mail client so that users can use their SAT training to more effectively identify and report phishing threats.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)








 IRONSCALES’ solution offers a catalog of 1150+ Phishing Templates in 10+ Languages with accompanying reinforcement training modules. (
IRONSCALES’ solution offers a catalog of 1150+ Phishing Templates in 10+ Languages with accompanying reinforcement training modules. (

