Guide to phishing simulation tools
Phishing is an old but effective attack type and the most common initial attack vector today, often combined with ransomware. Although its mode of operation is known and has been widely studied since it appeared in 1996, it remains successful because of the complexity of human nature. It exploits key human traits like curiosity, fear, urgency, distraction, desire for rewards, and impulsivity because humans are the weakest chain of every anti-phishing strategy.
While more and more companies are incorporating security awareness training (SAT), reducing the risk of phishing, companies need a way to test the effectiveness of such training before they are attacked. Phishing simulation remains one of the most effective methods of achieving this by testing employees and their knowledge on phishing as well as identifying employees who need additional SAT.
In this article, we describe six different tools for phishing simulation. We cover their key features, strengths, and weaknesses and how they can benefit your organization in improving the SAT content.
Summary of tools for performing phishing simulation
The table below lists six different phishing simulation tools to consider for simulating a phishing attack within your organization. We’ll cover each of them in detail later in this article.
| Phishing simulation tool |
Description |
|
Social Engineering Toolkit (SET)
|
SET is a tool used for social engineering assessments and awareness training that enables the user to create convincing phishing websites or write targeted spear phishing emails.
|
| GoPhish |
GoPhish is an open-source option to organize large-scale phishing campaigns that allows you to customize the phishing landing page. |
| Phishing Frenzy |
Phishing Frenzy is another open-source tool for phishing simulation that comes with built-in phishing templates and provides real-time reporting. |
| M365 Attack Simulator |
Integrated into Microsoft Defender for Endpoint (MDE), this tool allows you to send phishing emails to specific employees and track their interaction with the phishing email and with its URL. |
| IronScales Starter - Free Phishing Simulation Testing |
This is a free phishing simulation product with a phishing incident insights dashboard, reporting and analytics of the phishing campaign, SSO integration, etc., all in one tool. |
| Evilginx |
Evilginx is a powerful man-in-the-middle phishing tool that can also be used to bypass 2-factor authentication (2FA) protection. |
Six tools for phishing simulation
This section will present details on the six different phishing simulation tools to be used with SATs that were summarized above.
Social Engineering Toolkit (SET)
SET was developed by a security researcher to show different techniques that attackers can use to exploit human traits during phishing attacks.
SET’s interface and its variety of features
Its main advantages are:
- It allows you to set up a large phishing campaign with a few clicks and simple configuration.
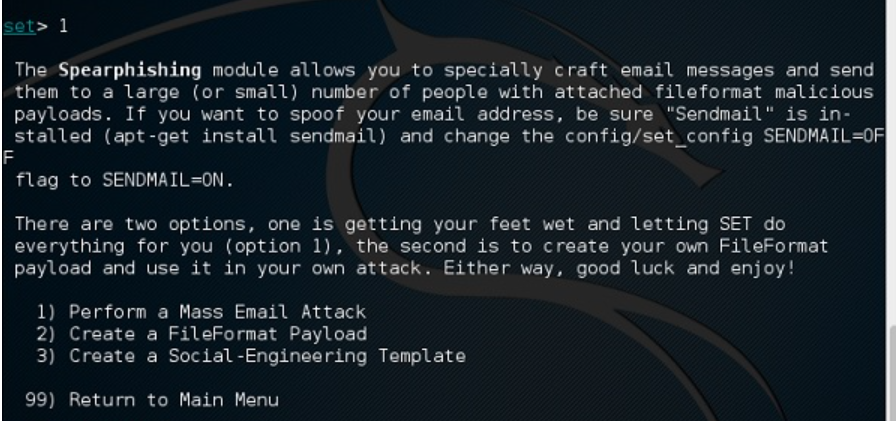
SET’s phishing campaign options
You can then choose between the following:
- E-Mail Attack Single Email Address: Choose this option to organize a spear phishing email and not a mass campaign.
- E-Mail Attack Mass Mailer: Import a list of email recipients who are the targets of the phishing campaign. The list has no size limit.
- It ships with built-in templates that can be easily customized to fit your needs.
- It allows you to clone a target website to make your phishing domains look like the target:
SET’s template alternatives
- It is free, since it is open source.
That said, SET has a number of disadvantages as well:
- Since SET is known to be abused by attackers as well, there is a considerable chance that the email security tools will recognize emails generated from SET and block them.
- It is not straightforward to track user/victim interactions or even generate a report: One must go through the logs and parse them to generate a report.
- Since it is open source, SET does not come with support in case something breaks or does not go as intended.
- It does not come with training packages to support security awareness training in the aftermath of the phishing simulation.
Note that SET is not restricted to only phishing: It can also generate payloads that exploit browser vulnerabilities or generate Metasploit-alike backdoors.

GoPhish
GoPhish is another open-source tool. It was written in the Go programming language (thus the name) and is free to use. It comes with many benefits such as simple installation, a web UI for those that are not comfortable with the CLI, a full REST API, cross-platform support, and reports.
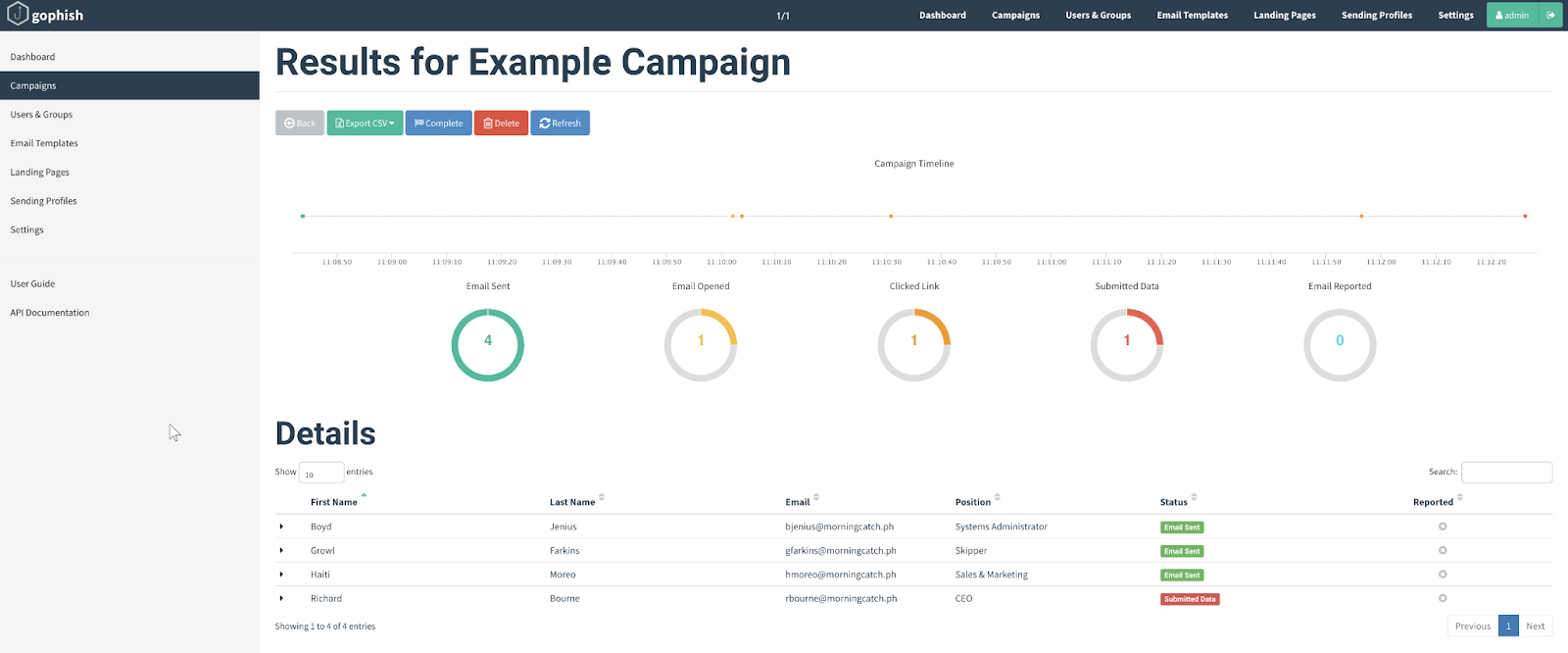
GoPhish UI of a phishing simulation (source)
While it is certainly more user friendly and provides better reporting capabilities than SET, it suffers from some limitations. GoPhish is only focused on email phishing and does not cover phone-based or SMS-based phishing. Additionally, integration with external email service providers requires some expertise and effort. Since it is open source, you cannot rely on customer support to walk you through the integrations. Finally, it does not provide training content to support SAT and is focused on phishing simulation alone.
Phishing Frenzy
Phishing Frenzy is another open-source phishing simulation tool that provides a web-based interface for quickly creating, modifying, and launching phishing campaigns. Compared to other tools, it excels at multi-campaign management as well as scheduling them at the desired date and time. It also provides multi-user support, allowing your entire team to contribute to the “shaping” of the phishing simulation. It can also provide different kinds of phishing campaign statistics to provide a feel for success in numeric terms.
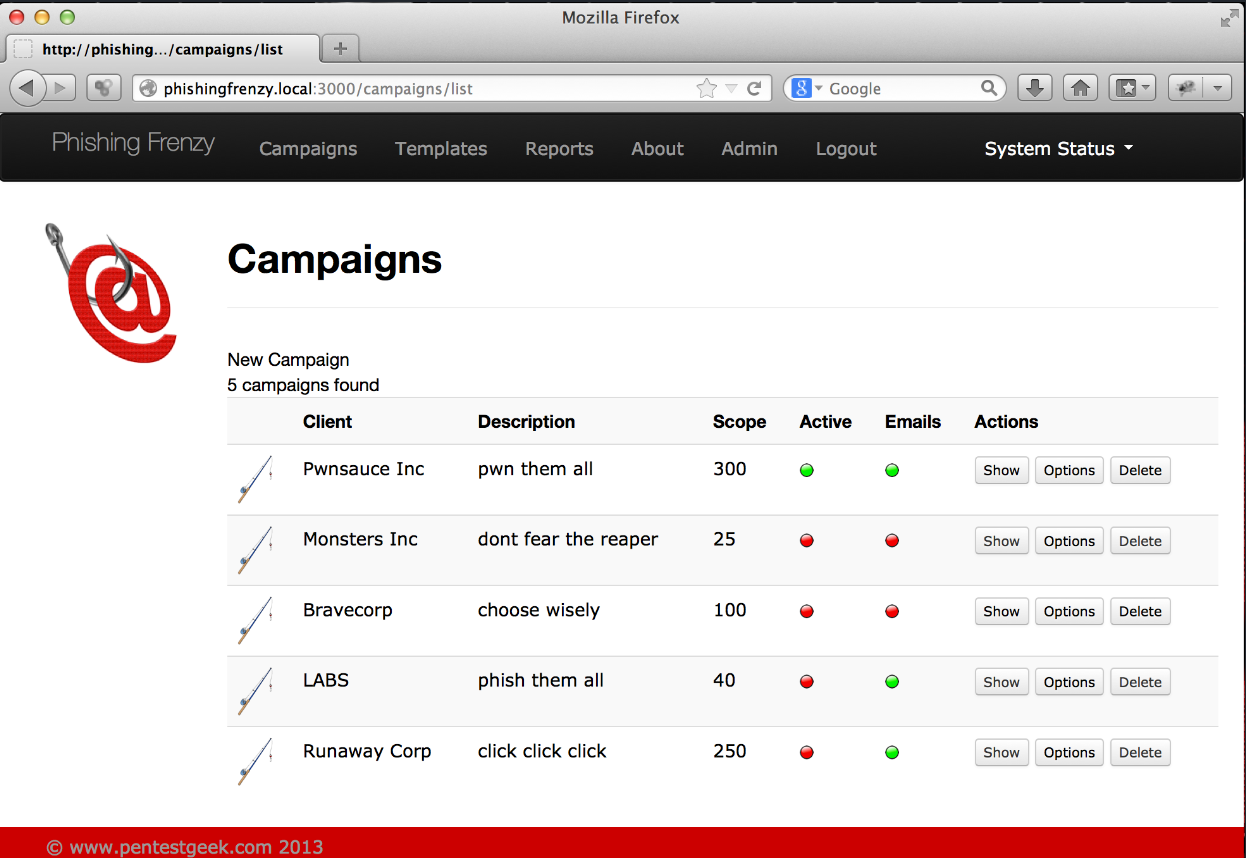
Phishing Frenzy UI components (source)
Unfortunately, the tool is no longer maintained, and the available community support is smaller compared to other open source solutions, such as GoPhish or SET. Like GoPhish, it comes with integration complexity and a lack of training content.

M365 Attack Simulator
Microsoft365 comes with a central security tool called Microsoft Defender For Endpoint (MDE). This is a commercial solution that comes with license requirements since MDE offers different security services, such as cloud application security, Exchange Online message tracing, endpoint detection and response (EDR), etc. One of its features is the Attack Simulator module, which enables a company to simulate different kinds of attacks, including phishing campaigns.
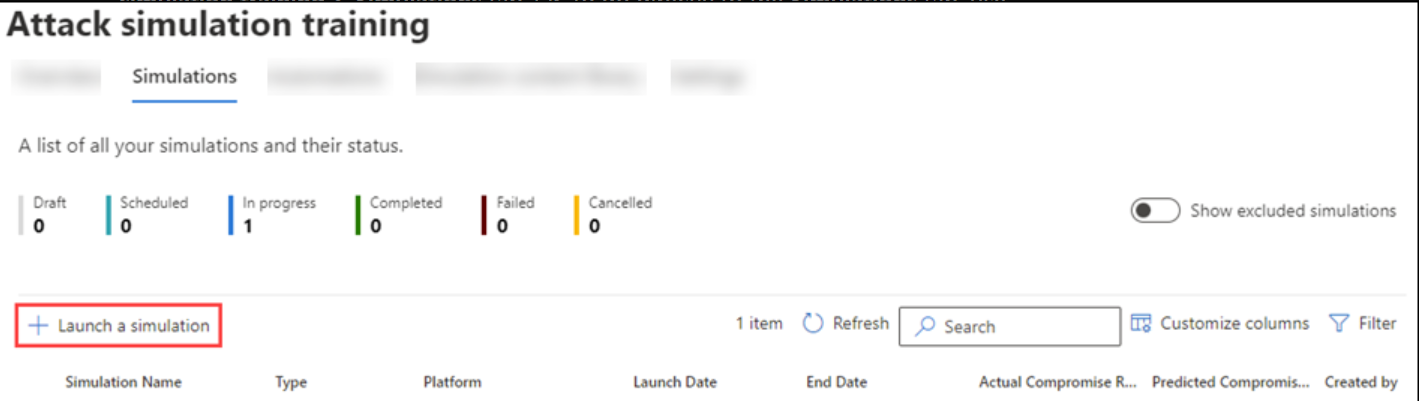
Attack Simulator UI in MDE (source)
MDE ships with the Attack Simulator, which is easy to use. If your company is already using MDE, you can benefit from its features without needing any setup, reading documentation, or integrating with email service providers.
Attack Simulator provides a wide range of phishing scenarios, including:
- Credential harvesting: The “typical” scenario with phishing websites.
- Malware attachment: Instead of URL phishing emails, it sends emails with “malicious” attachments to check how many employees are willing to install or execute a script or software sent by email.
- Link in attachment: A hybrid form where an attachment is sent by email that includes the phishing link in it (as compared to writing the phishing URL in the content of the email).
- Drive-by-URL: Here, the phishing email contains an URL that takes the user to a familiar-looking website that attempts to exploit the victim’s browser to silently run unauthorized code or software (the so-called drive-by-download).
- OAuth Consent Grant: The phishing email contains an URL that asks users to grant permissions to data for a malicious Azure application.
While the Attack Simulator covers different email-based phishing scenarios, it does not cover other types of phishing, such as phone-based or SMS-based phishing. Moreover, it cannot be acquired as a separated service: The company must purchase a license for MDE to be able to use the Attack Simulator and conduct a phishing campaign. In other words, while the feature itself does not need integration, your company still needs to integrate and configure MDE to be able to use Attack Simulator.
IronScale Starter: Free Phishing Simulation Testing
IronScale Starter is another free phishing simulation service that provides a fast setup for a phishing simulation campaign, taking the burden of configuration and integrations away from the security team. It allows your team to incorporate it with M365 in a simple two-click integration process. Additionally, it adds a “Report Phishing Button” to the Outlook email client, making it easier for employees to report the email to the security team.
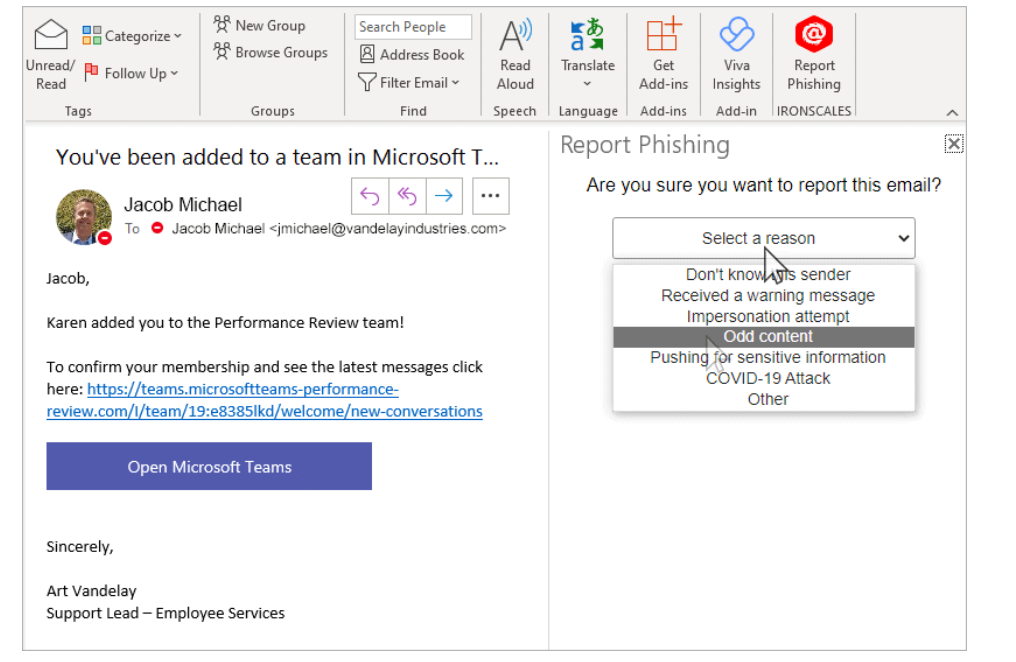
IronScales phishing button for the Outlook email client (source)
From a security perspective, it provides a Threat Management Dashboard that reflects the phishing incidents from the campaign as well reporting dashboards and analytics to measure the progress of the phishing campaign in numbers. Finally, it comes with a mobile app that enables security analysts to access the phishing incidents while on the go. This helps the security team make time-sensitive decisions on phishing incidents immediately with one click.
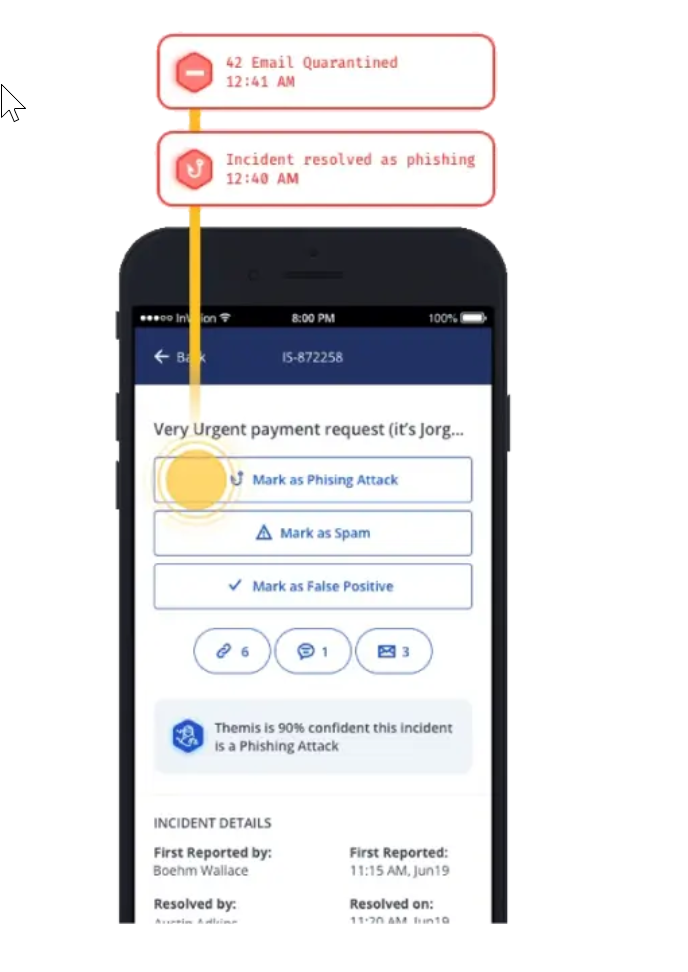
IronScales Mobile App for phishing incidents (source)
If your company wants to take this one step further, it should consider more advanced solutions that provide additional benefits. For example, the IronScales Complete Protect solution provides frequently updated libraries with phishing templates based on real-life situations by using real-time data from a global community of security analysts. This ensures that the phishing campaigns are credible and always up to date with the latest phishing trends:
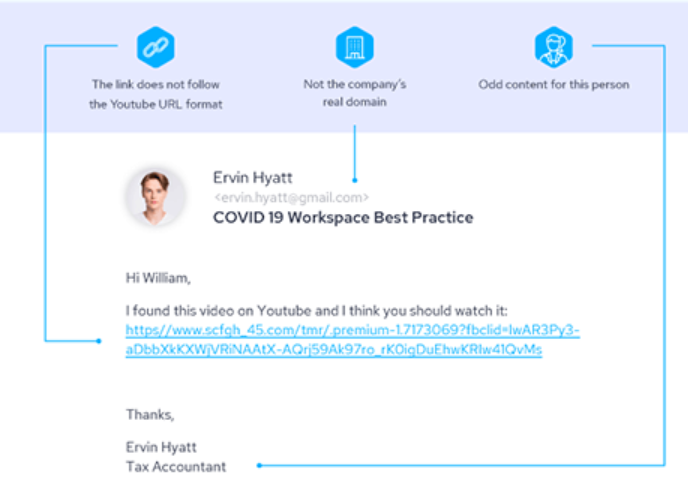
Real-life phishing email example from IronScale(source)
IronScales Complete Protect is also bundled with many security training content packs, providing additional training material for employees immediately after they fall victim to the phishing to help them understand what they did wrong and how to improve.
IronScale’s 1-Click Campaigns and Auto-Generated Content (source)
Evilginx
While Evilginx is not exactly a phishing simulation tool, it can be used as an extension of the tools above since it provides many features and can be used to generate a phishing simulation. Its main strength and purpose is its ability to defeat the two-factor authentication (2FA) scheme. Although the goal of a phishing simulation is to check if users will provide credentials or not, we can go one step further: We can show employees that 2FA being activated does not eliminate the risk associated with entering credentials in phishing websites. 2FA cannot help if the victim is deceived and willingly enters the 2FA code.
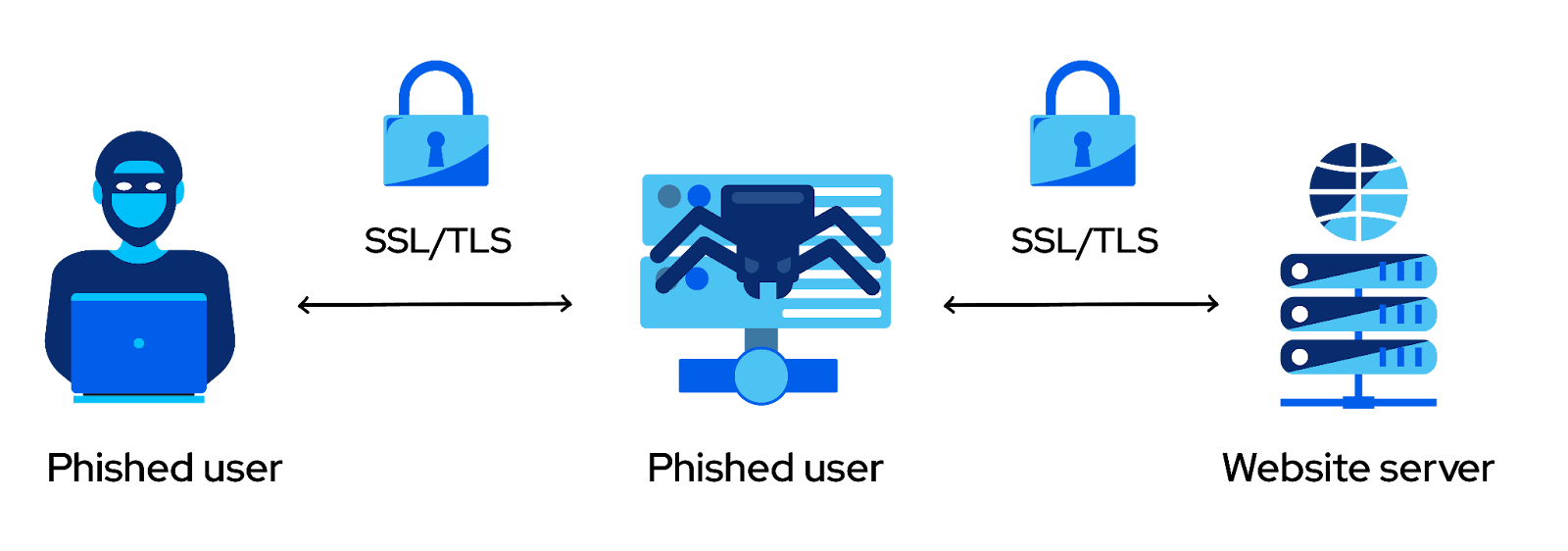
Evilginx man-in-the-middle scheme
Evilginx operates using the man-in-the-middle principle, residing between the user and the web application that the user is trying to visit. While a full guide on how to set up the phishing campaign is beyond the scope of this article, we can summarize the process:
- Set up an internet-facing system (e.g., via a cloud provider) and install Evilginx on it.
- Ensure that the TCP/443 (HTTPS), TCP/80 (HTTP), and UDP/53 (DNS) ports are listening for new connections.
- Register a phishing domain, e.g. exampel.com (notice that this is a typosquatting version of example.com). Many people read through text very fast and might not notice the “typo.”
- Set up the DNS records for your new domain to point to the internet-facing system you set up in step 1.
- Start Evilginx.
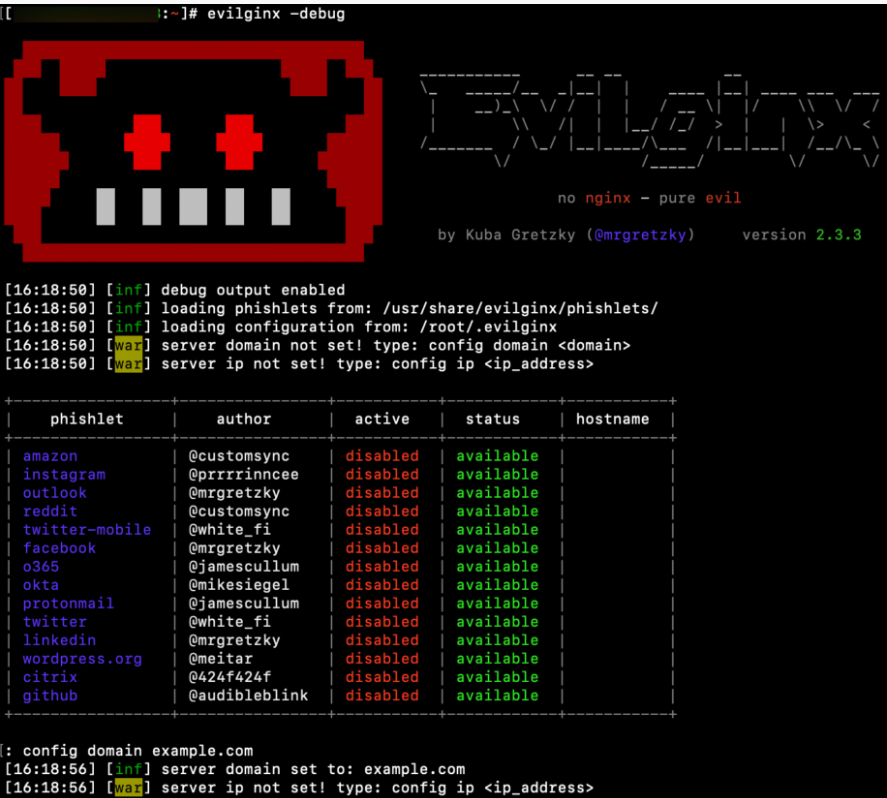
Evilginx’s CLI and IP configuration step
- Choose from a variety of phishlets (i.e., phishing templates) to use for the phishing simulation. Most popular MFA services, such as Microsoft or Okta, are already offered by this tool.
- After identifying the phishlet that fits your case, open its YAML config file and replace “example” with your new phishing domain.
- Enable the phishlet from the command line with a command such as “phishlets enable m365”.
- By using the “lures” module of Evilginx, you can create a phishing URL (e.g., “https://exampel.com/login”) for your new phishing domain, which you will send to the target employees.
- Wait for the victim to visit your phishing URL.

Summary
In this article, we looked into the importance of security awareness training and how phishing simulation can help with measuring its effectiveness. We looked into six different phishing simulation tools and their strengths and limitations. While the perfect simulation tool does not exist, there are certainly tools that cover the most important features and incorporate them into a single, easy-to-use tool.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)










