How to defend against URL phishing
Phishing is an attack where an attacker aims to trick the victim into leaking information, clicking on a malicious link, or doing anything else that benefits the attacker. It might occur via emails, phone calls, SMS, or messages on social media. URL phishing is a type of phishing where the attacker sends malicious URLs and tries to trick the victim into clicking them. Over the years, attackers have become more creative, making URL phishing a never-ending problem.
This article discusses some best practices that you can use to protect against the URL phishing vector. We also cover some common mistakes or misunderstandings with these best practices and recommendations on how to avoid them.
Can email security solutions block URL phishing attempts?
While many email security services scan the content of the email and filter malicious URLs, experience has shown that these filters are not perfect. URL phishing emails still bypass basic filtering because attackers use:
- Recently-registered domains for which there is no domain reputation information yet.
- A web hosting service with an excellent reputation to host the malicious phishing website, e.g., SharePoint.
- URL shortening services like Bitly to hide the actual URL.
Alternatively, the attacker might try to fool the victim using typosquatting domains that look similar to legitimate ones. Typosquatting, also called URL hijacking, relies on mistakes such as typos made by end users when typing a website address.
These are only some of the popular approaches that attackers use to bypass URL filters. To remain one step ahead, you must combine security tools and best practices for total protection. In this article, we will look into the best practices that you can use to detect, analyze, and prevent URL phishing emails.
Summary of best practices that prevent URL phishing
| Best practice |
Benefit |
|
Check domain reputation
|
Recognize already-known malicious domains in URLs.
|
| Use URL sandboxes |
Analyze the content of the website without visiting it from your computer. |
| Deploy a proxy for all web traffic |
Identify employees that have clicked on malicious links and use a proxy blocklist to block URLs during IR. |
| Make use of AI solutions |
Stay up-to-date with the latest phishing trends by using AI solutions that are constantly trained with new phishing attacks. |
| Purchase an anti-phishing service |
Detect fraudulent or typosquatting domains impersonating your domain as soon as possible before they are used in URL phishing attacks. |
| User awareness sessions & phishing simulations |
Educate the users on URL phishing and how to recognize malicious emails. Perform phishing simulations with fake URLs to measure the results of the user training sessions. |
Understanding URL phishing
While there are several different styles of URL phishing emails, let’s look at a real-life example where the attacker impersonates your bank or any other familiar entity and asks for your login data, e.g., for PayPal.
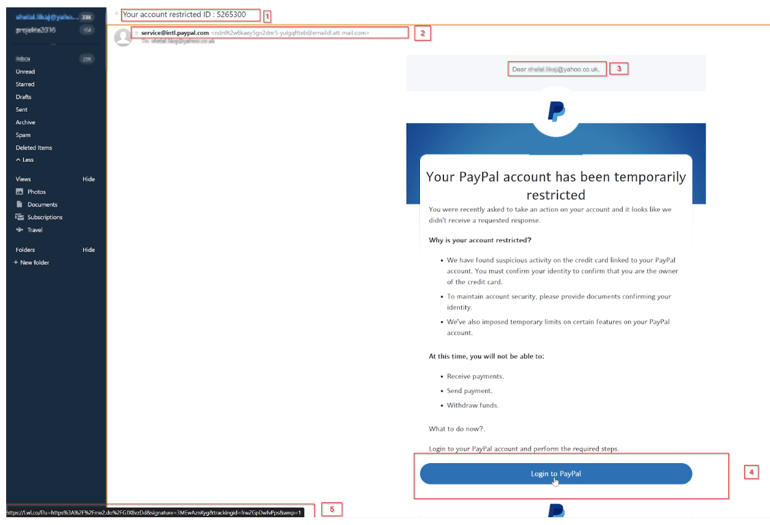
Real URL phishing example where the attacker is impersonating PayPal
Common strategies attackers use on URL phishing emails include
False sense of urgency
Subject Line (red box 1): We see that the subject of the email tries to create a sense of urgency with the target victim, telling them that their PayPal account was blocked/restricted and they need to do something immediately; otherwise, it will remain blocked.

Disguised sender address
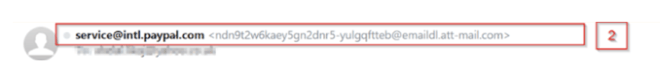
Email Sender (red box 2): While the visible part of the sender tells you that the email is from service@intl.paypal.com, looking further on the line, we notice the sender's email address, ndn9t2w6kaey5gn2dnr5-yulgqftteb@emaildl.att-mail.com, definitely not a PayPal domain.
Generic email style:
Greeting: (red box 3): The attacker uses the email address instead of a personal greeting that uses the target victim’s name and surname (like in legitimate cases). This is often a sign that the email was automatically generated and was not carefully crafted like in other targeted (spear) phishing emails.

Malicious URL
Hyperlink (red box 4): Finally, the attacker advises the victim to log into their PayPal account. However, hovering over the “Login to PayPal” button, we observe the real URL (red box 5); this will direct the user to hxxps://l.wl[.]co website, which is most certainly not a PayPal website.

Best practices to defend against URL phishing
In this section, we will cover some of the best practices that your company can implement to defend itself against URL phishing attacks.

#1 Check domain reputation
A common attribute of many domains used in phishing attacks is their age. Attackers can register hundreds to thousands of new domains in a matter of minutes and launch email attacks the same day in many cases. New domains won’t get flagged by domain reputation lists for a while, so additional investigation and inspection is required for emails sent from these fresh domains.
Manual checks
One way your security team can check when a domain is created is via WHOIS. This protocol is used to query different databases containing information on every domain, its registrant, registrar, dates, etc. Your security team can use various free WHOIS websites to check the WHOIS information for the sender domain or the domain in the URL to decide on its legitimacy before blocking it. Alternatively, you can use threat intelligence platforms like VirusTotal to see if the community considers this domain malicious.
Automatic checks
However, your company probably receives thousands of URL phishing emails, and it is infeasible to review all of them manually. Although most email servers can be automatically configured to reject emails from domains that are less than X days or months old, setting or finding the right threshold is not always easy. Moreover, while this security feature might filter out many phishing or spam emails, it might also block legitimate emails, e.g., from clients that have recently started their business and have set up a new domain. To avoid these false positives with business impact and to reduce the burden on the security team, consider investing in an automated solution specializing in malicious URL recognition in emails.
#2 Use URL sandboxes
Sometimes, it might be challenging to infer whether a URL is malicious only by looking at its domain. For example, attackers often use URL shorteners like bit.ly to hide the domain and URL or use a subdomain in the (popular) SharePoint website, aiming to fool detections focused only on the domain name. That is why a security analyst should also scan the URL to understand its purpose and whether it should be blocked.
Instead of clicking on the malicious URL directly, you can use URL sandboxes that visit the website on your behalf. This way, a security analyst can infer if the URL is benign or malicious and if it aims to steal credentials, download malware, or perform a scam. These sandboxes can be software-based, e.g., Cuckoo, or online-based such as VirusTotal or urlscan.io.
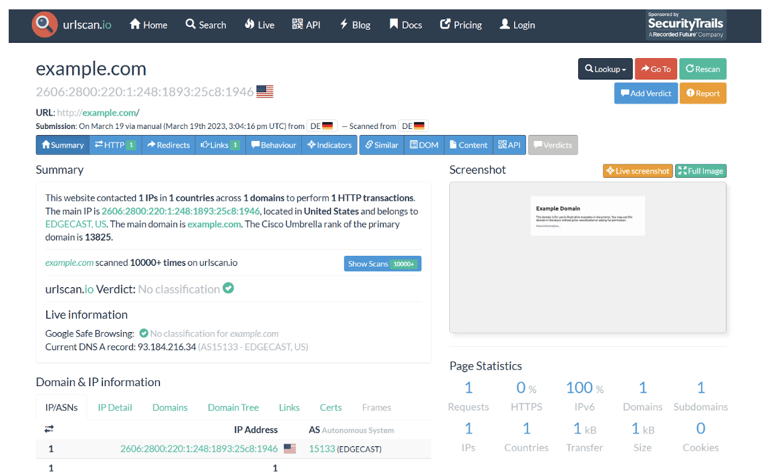
Example of an online sandbox that you can use to scan malicious URLs without directly clicking the URL from your company’s network.
If your company deals with a high amount of phishing emails, you might prefer an email security solution that automates this process and blocks emails with malicious URLs before it even reaches the victim.
#3 Deploy a proxy for all web traffic
While different security products block most malicious URLs, no system is perfect as defenses might be bypassed and the victim might click on the malicious URL. That is why it is essential to use a web proxy and ensure that employees have no alternative way to browse the Internet.
The proxy creates a central place for your security team to check the weblogs in case a malicious URL is reported by an employee or detected during threat hunting. The security team can identify affected employees who have clicked on the malicious URL and start the Incident Response (IR) process.
It is also worth mentioning that most enterprise web proxies perform reputation checks and other controls when an employee visits a specific domain. Such proxies also provide a blocklist to the security team to block malicious URLs so that other employees are not lured into malicious websites.

#4 Make use of AI solutions
As noted earlier in this article, the creativity of attackers continues to evolve in crafting deceptive URLs. Their tactics can include employing URL shorteners, leveraging popular web hosting sites, utilizing file-sharing platforms such as SharePoint, or even spreading QR codes that redirect to harmful emails – and that's just to name a few. This unending cat-and-mouse game shows no signs of abating. However, by incorporating Artificial Intelligence (AI) and Machine Learning, you can effectively detect malicious URLs amidst the ever-evolving phishing landscape. Continually training these AI solutions with current trends in phishing emails enables us to maintain defenses that counter the latest strategies employed by attackers.
#5 Purchase an anti-phishing service
One of the most deceiving schemes attackers use in URLs is typosquatting domains. These domains are, at first glance, very similar to the domain name of your company or other famous companies. However, they often contain typos or use special characters that look identical to the user. For example, if the victim is not attentive, they might not observe that company.com is not the same as compány.com (notice “á” instead of “a”). Your company might consider purchasing an anti-phishing service that checks for newly-registered domains (including typosquatting) before they are abused.
#6 Security Awareness Training and & phishing simulations
The end goal of a URL phishing email is to trick the user into clicking on it. No matter how advanced your email security stack is, some phishing emails will occasionally make it to your employees’ mailboxes. That is why training your employees to recognize phishing emails in general and weird URLs, in particular, is essential. For example, suppose a trained employee reports a URL phishing email to your security team. This gives the security team the opportunity to check if other employees received this email or if they have fallen victim and clicked on the malicious URL (via proxy logs).
Security awareness training (SAT) sessions are a crucial defense against phishing emails. But awareness only goes so far. The best way to make sure the lessons are effective is to test your employees by conducting periodic phishing simulations. A good phishing simulation tool (like this totally FREE one from IRONSCALES) makes it simple to automate and find users who needs additional follow-up training.
If your company lacks the resources to coordinate SAT and phishing simulation testing, consider hiring a service provider specializing in these activities.
Additional recommendations to strengthen URL phishing protection
There are however some additional things to consider as you implement these best practices.
Proxy vs. QR codes
Note that a web proxy is installed on the company network. If the attacker uses QR codes, employees might use their mobile phones to scan the QR code and access the URL through their mobile network. The URL will not appear in the proxy logs. This creates a blind spot, and it is essential to cover this aspect in user awareness training.
Using the right AI solution
Since AI solutions are only as good as the data used to train them, it is also important to feed these models with threat intelligence from human experts that deal with the latest phishing emails on a daily basis. There are already solutions in the market that merge AI and human insights to ensure the quality of the data that trains and further improves the AI model.
Blocking domains vs. URLs
Analyze a domain or URL properly before you block it. Note that many malicious URLs are hosted on benign websites. Blocking the entire domain might impact your company's business if other departments use it.
On the other hand, blocking a specific URL might also not be enough since attackers might use different encodings to generate different URLs, ultimately leading to the same final URL. Consider these facts before blocking an URL, domain, or subdomain!

Conclusion
In this article, we explained what URL phishing is, how it works, and why it can be dangerous. While it is one of the most common types of phishing, it is also one of the most ever-changing types, with attackers getting increasingly creative. You can use several best practices to analyze, detect, and prevent such malicious emails. Remember to combine the best practices with a comprehensive email security solution that keeps up with the latest threat intelligence.

/Concentrix%20Case%20Study.webp?width=568&height=326&name=Concentrix%20Case%20Study.webp)















